Connect first SaaS application - Office365
Overview
The company wants to restrict access to Office 365 in the following ways.
- A user can’t go direct to O365
- A user has to go through a secure infrastructure before they gain access to O365
- A users access to the Onedrive application is blocked if they are not in the USA or EU
- A user has to go through two-factor authentication before they can access OneDrive, even though they have access to other office applications without the need for two-factor authentication.
Apply these configurations to O365 in a simple fashion. (e.g. from a centralized GUI without having to log into MSFT console)
Solution
Acreto solution allows us to secure access to Office365/OneDrive using Microsoft Azure AD.
Acreto will provide the policy configurations to control the following:
- All users logged in through Acreto SASE+ can access O365.
- All users not logged in through Acreto SASE+ are not allowed to reach O365. e.g. they can’t go from home cable modem direct to O365 going around Acreto VPN.
- All users logged in through Acreto SASE+ but not logging in from a specific location such as China will not be allowed to log in to O365
- All users logged in through Acreto SASE+ but not logging in from a specific location such as the United States or Europe can access O365, but not OneDrive
Before you start
To solve the described issue you will need:
- Acreto account with configured security policy
- Microsoft Azure ActiveDirectory with more than one user
- Office365 licenses managed by Azure ActiveDirectory
- Active Directory users with Office365 licenses and internet connection secured by Acreto
Make sure that you have all the required elements before you will start.
Create Acreto security policy
As a first step you need to create a secure connection between end-user and acreto - use one of two possible solutions:
- configure vGateway connection and secure whole network connection
- configure Thing to connect using Acreto client
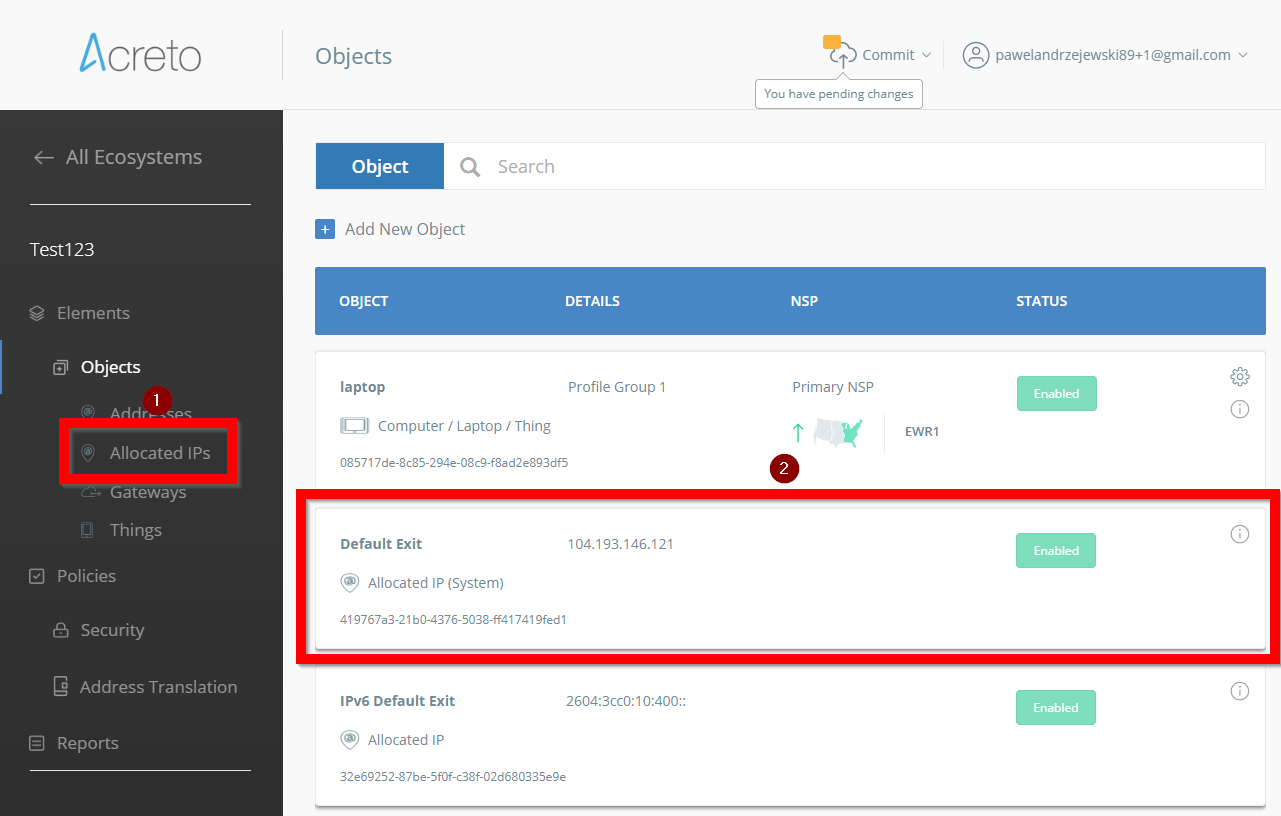
No matter which way you choose, after you connect to Acreto your external IP address should be masked with Acreto gateway - this means that any Internet service or website will be not able to see your real IP address. Acreto will mask your IP with an address that you may find in WEDGE panel - go to Allocated IP’s and then find Default Exit position - this is your Secured IP address.
Make this IP address to be the only address that should be allowed to access Office365/OneDrive services in your organization.
Configuration of Active Directory
If you already secured your internet connection with Acreto it’s time to make a security rule on Microsoft Azure ActiveDirectory.
1.Login to Azure panel as a user with administrator right and click on Azure Active Directory icon:
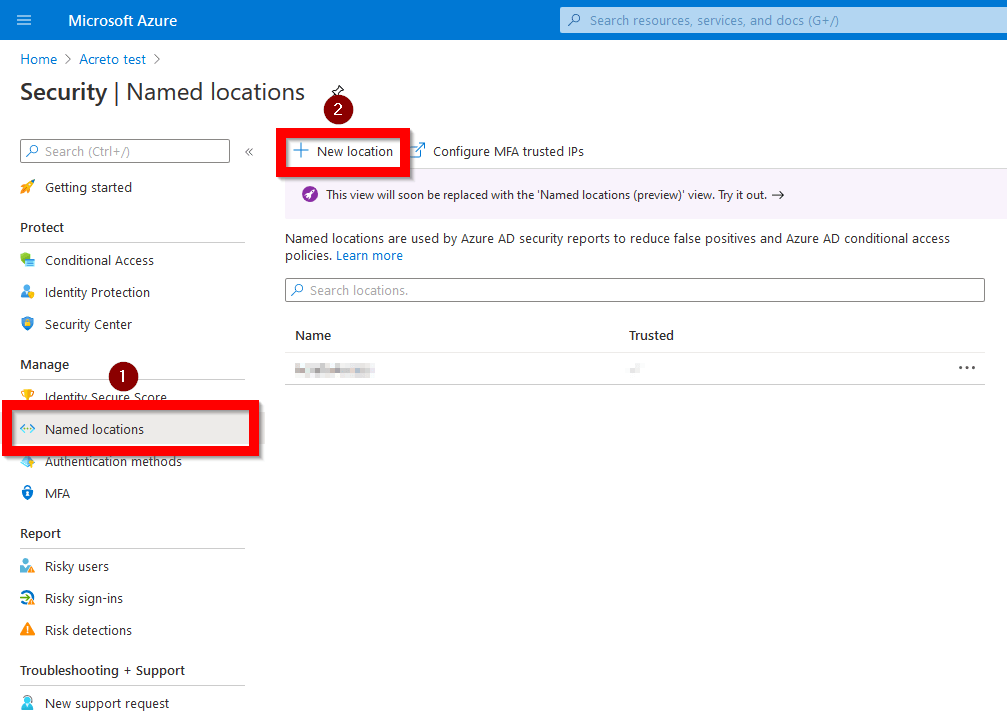
2. Choose the “Security” option marked on the screen below.
3.Create Named location - named and defined IP address range that will be allowed to access Office365/OneDrive.
To do this click on Named location on side menu (marked as “1”) and then click on + New location (marked as “2”).
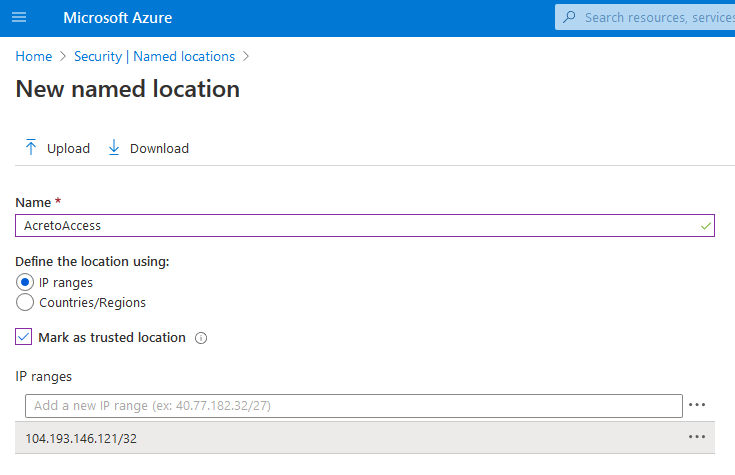
4. Fill new location form with readable name and choose options and save:
- Define the location using - choose IP ranges
- Mark as trust location - check
- IP ranges - add the IP address of Acreto gateway (104.193.146.121/32) - this is an example address, your Acreto Gateway may have different IP.
5.Create a security rule to limit access to Office365/OneDrive
Choose Conditional Acces option from the side menu and click on ** + New policy ** button.
The form of policy creation is advanced and offers many options, in this scenario we will use a minimal amount of options that allow us to get a working configuration.
- Assignments > Users and groups - select users or a whole group of users that needs to be under control.
- Assignments > Cloud apps or actions - choose the select apps option and then mark all apps that should be under control: Office 365 Exchange Online, Office 365 SharePoint Online, Office 365 (preview).
- Assignments > Conditions > Locations - choose Configure: yes and Selected location to be able to restrict access only from previously configured Named location. Be sure that the selected option is the Named location with the Acreto IP address.
- Assignments > Conditions > Client apps (Preview) - choose all available options to make sure that there will be no security gap in access rules.
- Access controls > Block access/Grant - decide do these rules should grant or block access when conditions are true. Here you may also define additional authentification steps like multi-factor authentication.
- Access controls > Session - choose Use app enforced restrictions, Use Conditional Access App Control
That’s a minimum required configuration necessary to make a goal of this case.
6. Make sure that Enable policy: On. -
This option is displayed on the bottom right part of the screen and it decided does the whole configuration is on.
If you can’t turn the rule on it’s possible that you need to disable Security Defaults
7. Double-check all rules and click on the save button.
Security verification
To verify does the created access rules works we do a two-part test:
- Login into Office365 without the Acreto
- Login into Office365 with the Acreto
In both tests, we will use a user account managed by Azure AD. This account is added to the created rule of conditional access.
Login into Office365 without the Acreto
At the first test, we will check dose it possible to log in to Office365 from an internet connection that is not secured with Acreto.
- The user goes to www.office.com and clicks on the login button
- Fill login form with username and password
- Click on the Log in button
The login page should return information that the User is not able to log in because does not meet the criteria to access this resource. This means that created security rule work.
Login into Office365 with the Acreto
In the second test user use Acreto secured internet connection and trying to login to office.com
- The user goes to www.office.com and clicks on the login button
- Fill login form with username and password
- Click on the Log in button
The login page works in a standard way and allows the user to access his account.
Summary
Thanks to Acreto and Azure AD conditional access rules you can create advanced security solutions.