Fortinet FortiGate IPsec Configuration through CLI
Before you start
Overview
This article will show you how to use CLI to connect the FortiGate managed network to the Acreto Ecosystem.
Prerequisites
- FortiGate installation
- Ecosystem set up with proper security policies
How-To
Create Gateway for IPsec
This step is optional, skip it if you already own the Gateway.
Firstly, you will need to create a new Gateway device in the Acreto platform. Instructions on how to create a new Gateway are available here.
- Name: IPsec connection name must meet the same requirements as the Strongswan connection name (letters and numbers only).
- Category: IoT
- Type: IPsec
- Allow connection from: Empty (describes the source IP address where the IPsec connection will be permitted).
- Local Networks: any local network addresses that will be routed
through this gateway.
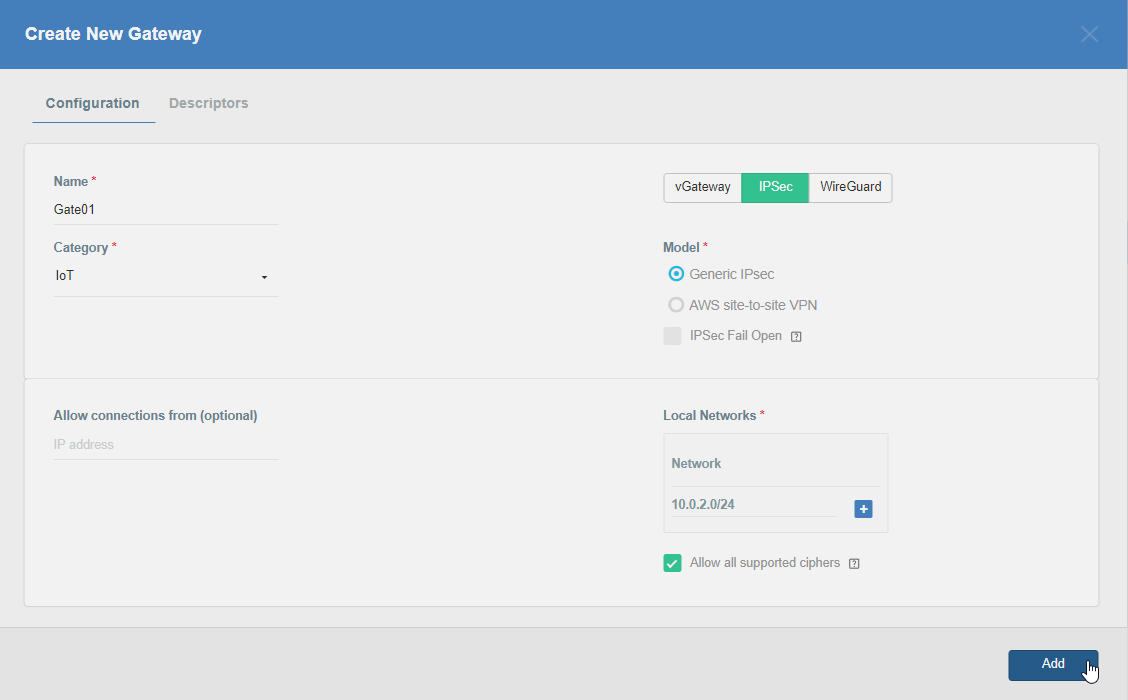

To simplify testing, add the IP addresses of all interfaces connected to your gateway as Local Networks (you can use /32 prefix for public interface). This will allow you to test connectivity from the gateway through Acreto by using Ping, Traceroute, or similar tools.
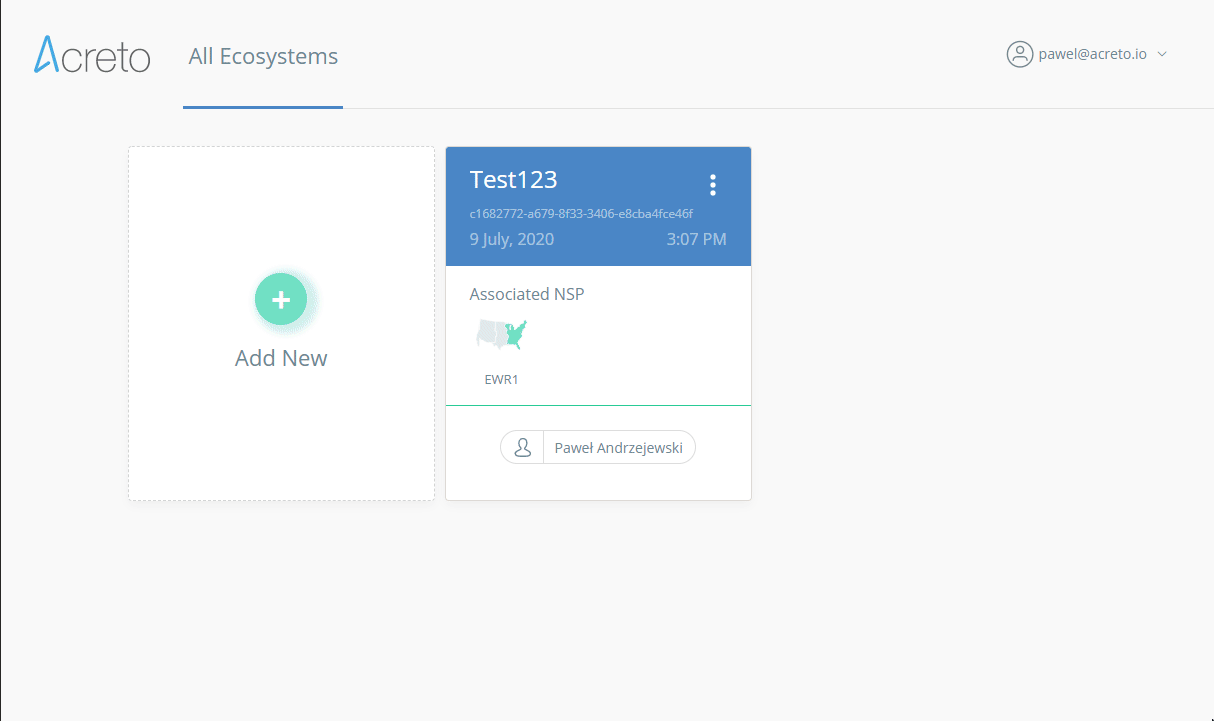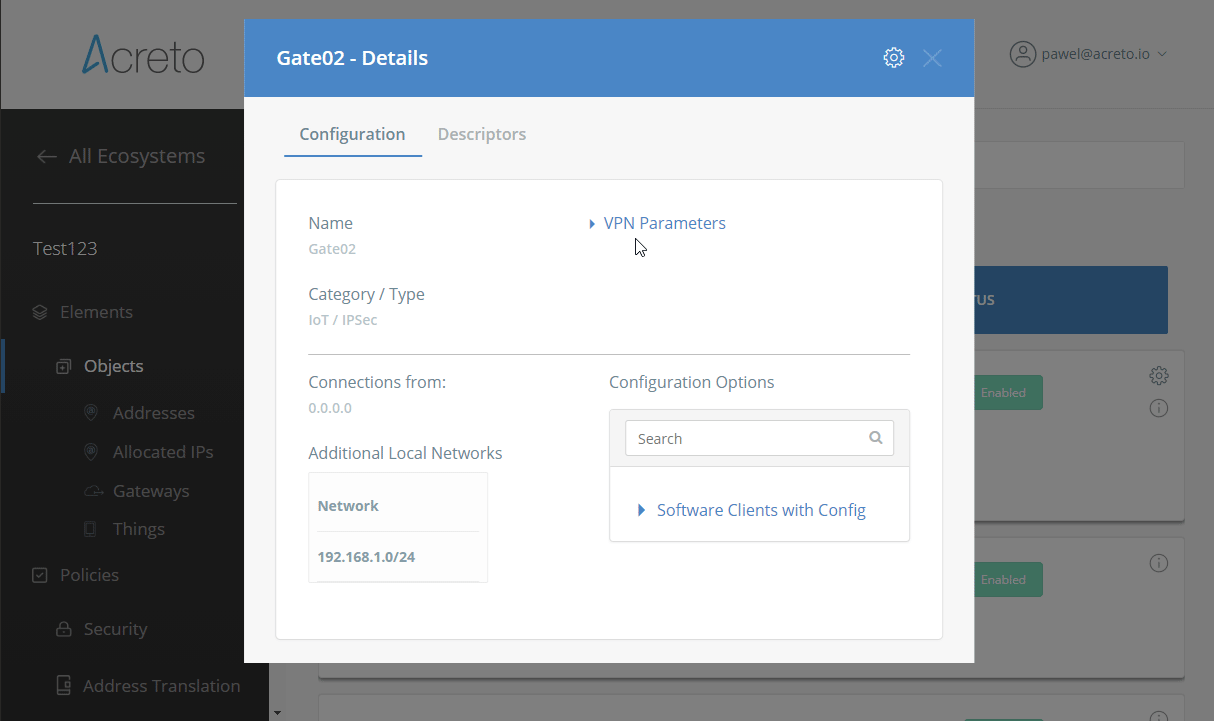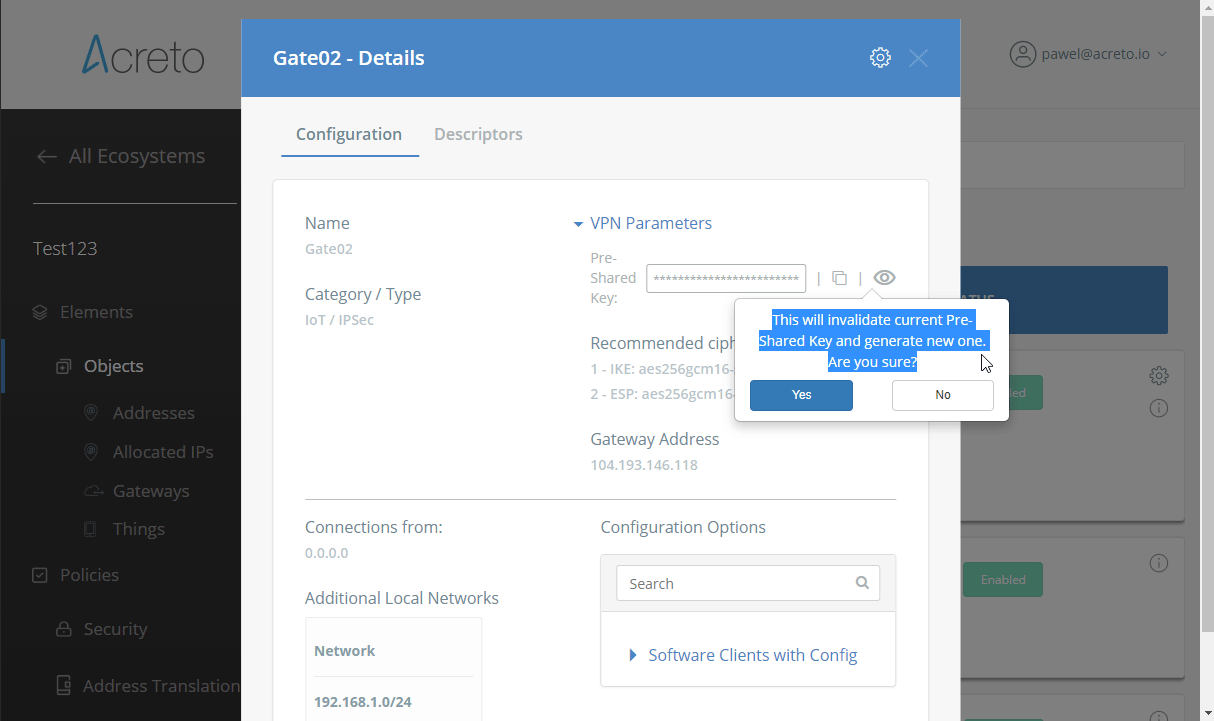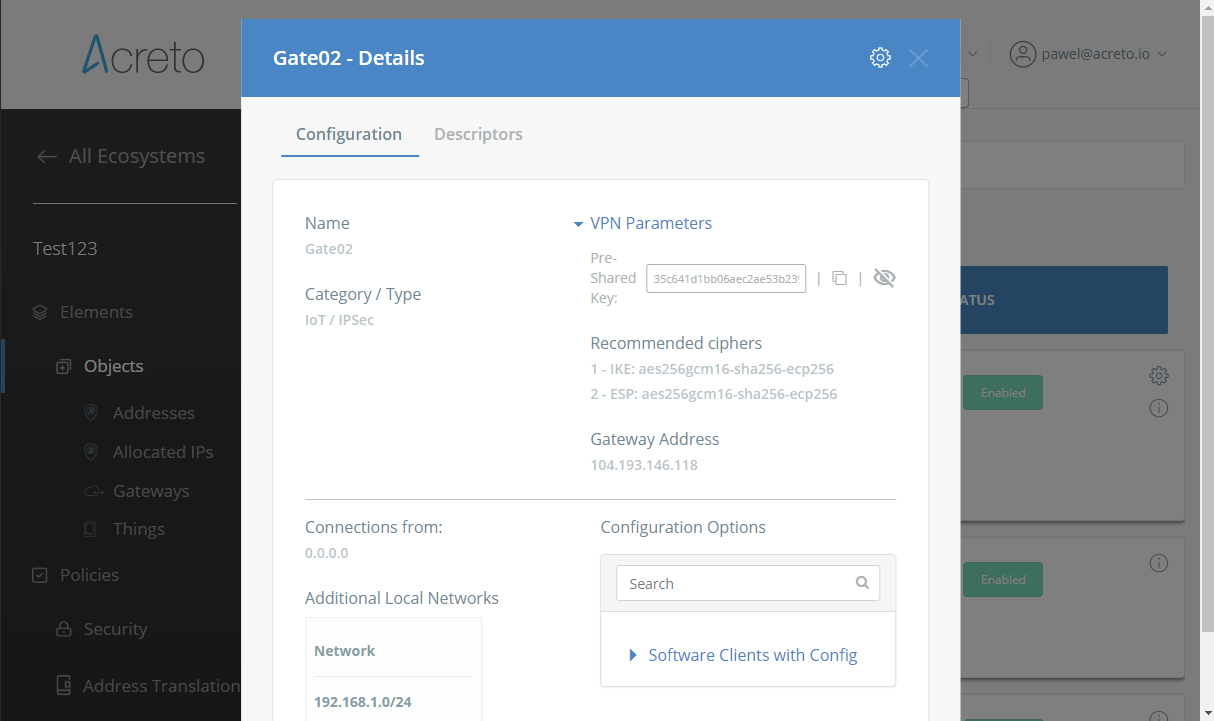
Step 1: Read IPsec Gateway Values Required for Fortigate Configuration
To proceed with the Fortigate configuration, you will need a few values from an existing committed Acreto Gateway:
- Gateway Address
- Pre-Shared Key
- Recommended Ciphers
All of these may be found within the Gateway details panel - view the below animation for further instruction.
Step 2: Configure Fortigate - Create VPN (Phase1 and Phase2)
Use the following commands to create a VPN through CLI.
Log in to the Fortigate CLI.
-
Configure IPsec VPN Phase-1
config vpn ipsec phase1-interface edit AcretoGate set interface <wan_interface> set peertype any set net-device disable set mode-cfg enable set proposal aes128-sha256 aes256-sha512 set ike-version 2 set keylife 10800 set remote-gw acreto-peer-ip (Copy from Wedge Dashboard) set psksecret psk (Copy from Wedge Dashboard) set dhgrp 16 set localid local-id (Copy from Wedge Dashboard) next end -
Configure IPsec VPN Phase-2
config vpn ipsec phase2-interface edit AcretoGate set phase1name AcretoGate set proposal aes256-sha512 aes256gcm set dhgrp 16 set keepalive enable set keylifeseconds 3600 next end
Step 3: Configure Fortigate - Create Address and Address group
-
Create addresses for all local addresses/subnets
config firewall address edit AcretoGate_local_1 set allow-routing enable set subnet 192.168.1.0 255.255.255.0 next edit AcretoGate_local_2 set allow-routing enable set subnet 192.168.2.0 255.255.255.0 next end -
Create an address group to add all the addresses created in the previous step
config firewall addrgrp edit AcretoGate_local_grp set member AcretoGate_local_1 AcretoGate_local_2 next end
Step 4: Configure Fortigate - Create Firewall Policy for Traffic
-
Outbound Policy for traffic originating from Local lan interface to internet through Acreto VPN
config firewall policy edit 0 set name Outbound_toAcreto set srcintf lan_interface_ip set dstintf AcretoGate set srcaddr AcretoGate_local_grp set dstaddr all set action accept set schedule always set service ALL next end -
Inbound Policy for traffic coming from Acreto VPN to Local lan
config firewall policy edit 0 set name Inbound_fromAcreto set srcintf AcretoGate set dstintf lan_interface_ip set srcaddr all set dstaddr AcretoGate_local_grp set action accept set schedule always set service ALL next end
Step 5: Configure Fortigate - Routing Changes
Scenario 1: When traffic from all local subnet/interfaces need to pass through the tunnel
-
Add Static Route
config router static edit 0 set dst Acreto_PeerIP set device wan_interface Set gateway ISP_Gateway next edit 0 set dst 0.0.0.0 0.0.0.0 set device AcretoGate set distance 4 next end
Scenario 2: When traffic from a specific subnet/interface needs to pass through the tunnel.
-
Add IP at the tunnel interface
config system interface edit "AcretoGate" set ip 2.2.2.2 255.255.255.255 set remote-ip 2.2.2.3 255.255.255.255 next end -
Add Static Route to direct the traffic through the tunnel with a higher administrative distance
config router static edit 0 set distance 254 set device AcretoGate set dst 0.0.0.0 0.0.0.0 next end -
Add Policy Route to direct the specific traffic through the tunnel
config router policy edit 0 set input-device lan_interface set srcaddr AcretoGate_local_grp set dstaddr all set output-device AcretoGate Set gateway 2.2.2.3 next end
Step 6: Configure Fortigate - Bring the Tunnel Up
Run the following command to bring the tunnel up bash diagnose vpn tunnel up AcretoGate
diagnose vpn tunnel up AcretoGateStep 7: Configure Fortigate - Verify
- Check the status of tunnel Phase-1
diagnose vpn ike gateway list name AcretoGate- Check status of Phase-2
diagnose vpn tunnel list name AcretoGateSummary
Once the VPN connection is successfully established, all the internet traffic will be routed through Acreto.