Azure Site-to-Site connection using VPN Gateway
Before You Start
Overview
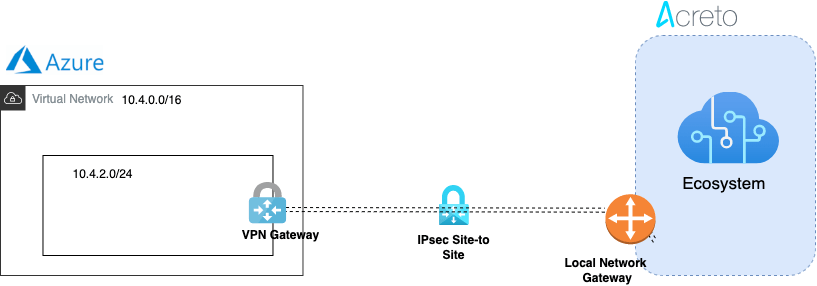
This article describes configuring a Route-Based Site-to-Site IPsec VPN between an Acreto Ecosystem and Azure network.
Network Diagram
Pre-requisite
To set up an IPsec Site-to-Site VPN tunnel between Acreto Ecosystem and Azure, you need:
- Access to Active Acreto Ecosystem (Wedge)
- Access to Azure Portal
How To: Configure Site-to-Site VPN in Azure
Use the following procedures to set up the Azure Site-to-Site VPN connection manually.
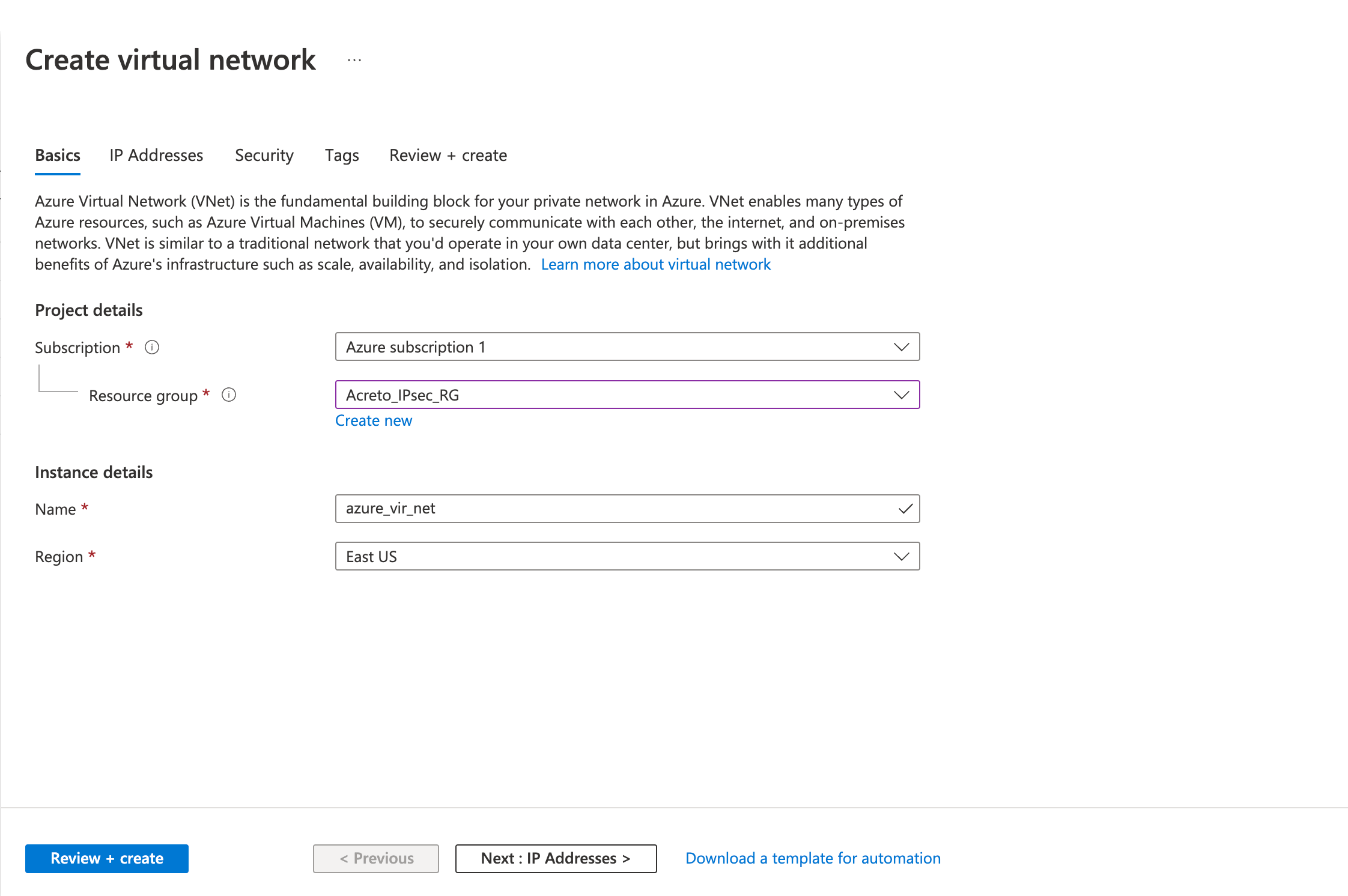
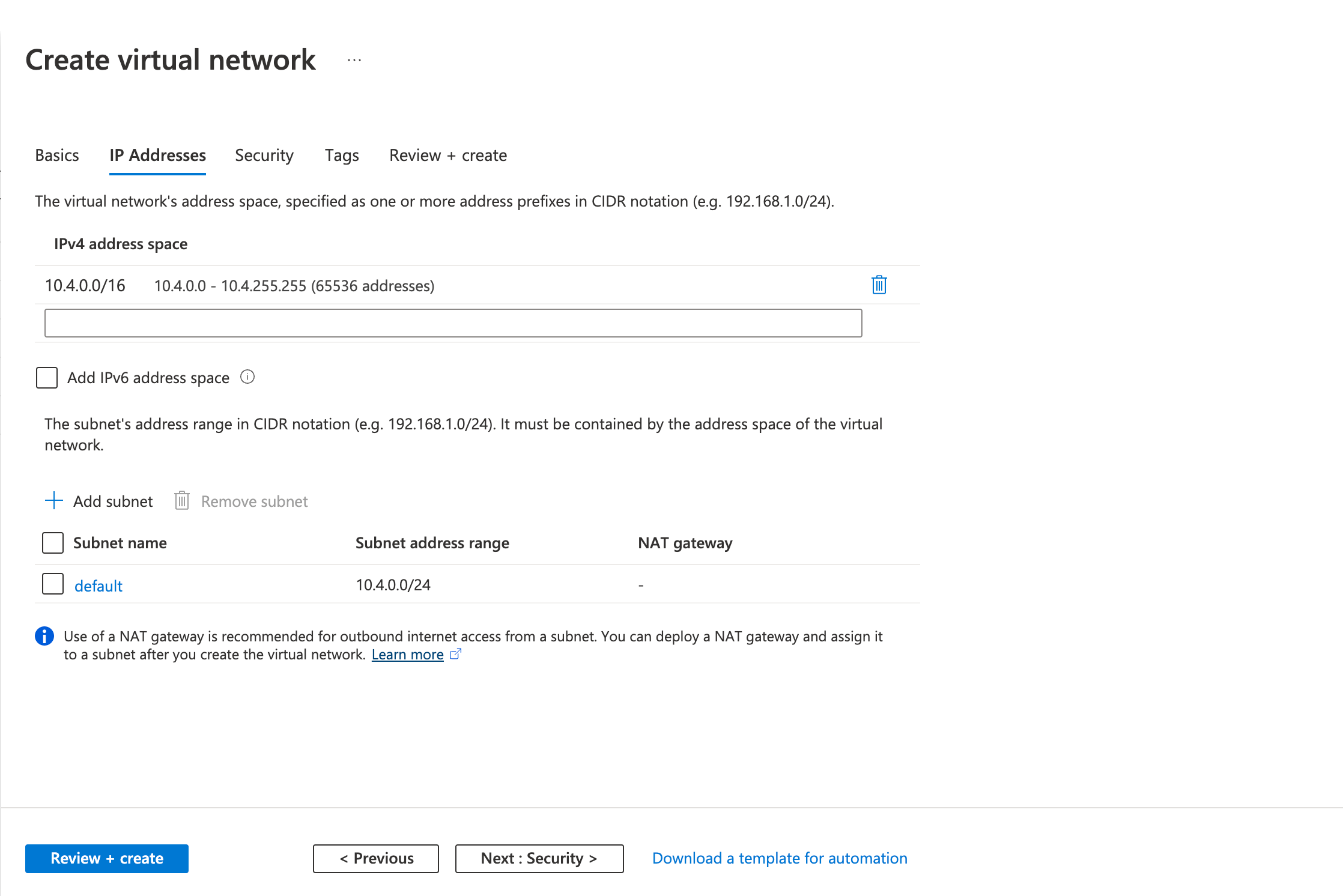
Step 1: Create a virtual network
Use an existing virtual private network or create a new virtual private network using the steps below:
- Login to Azure Portal
- Click on Create a resource
- Click on Networking from the left sidebar.
- Click on Virtual Network
- Fill in the following fields in the Basics tab.
- Fill in the following fields in the IP Addresses tab
- Review the configurations on the Review + create tab and click Create
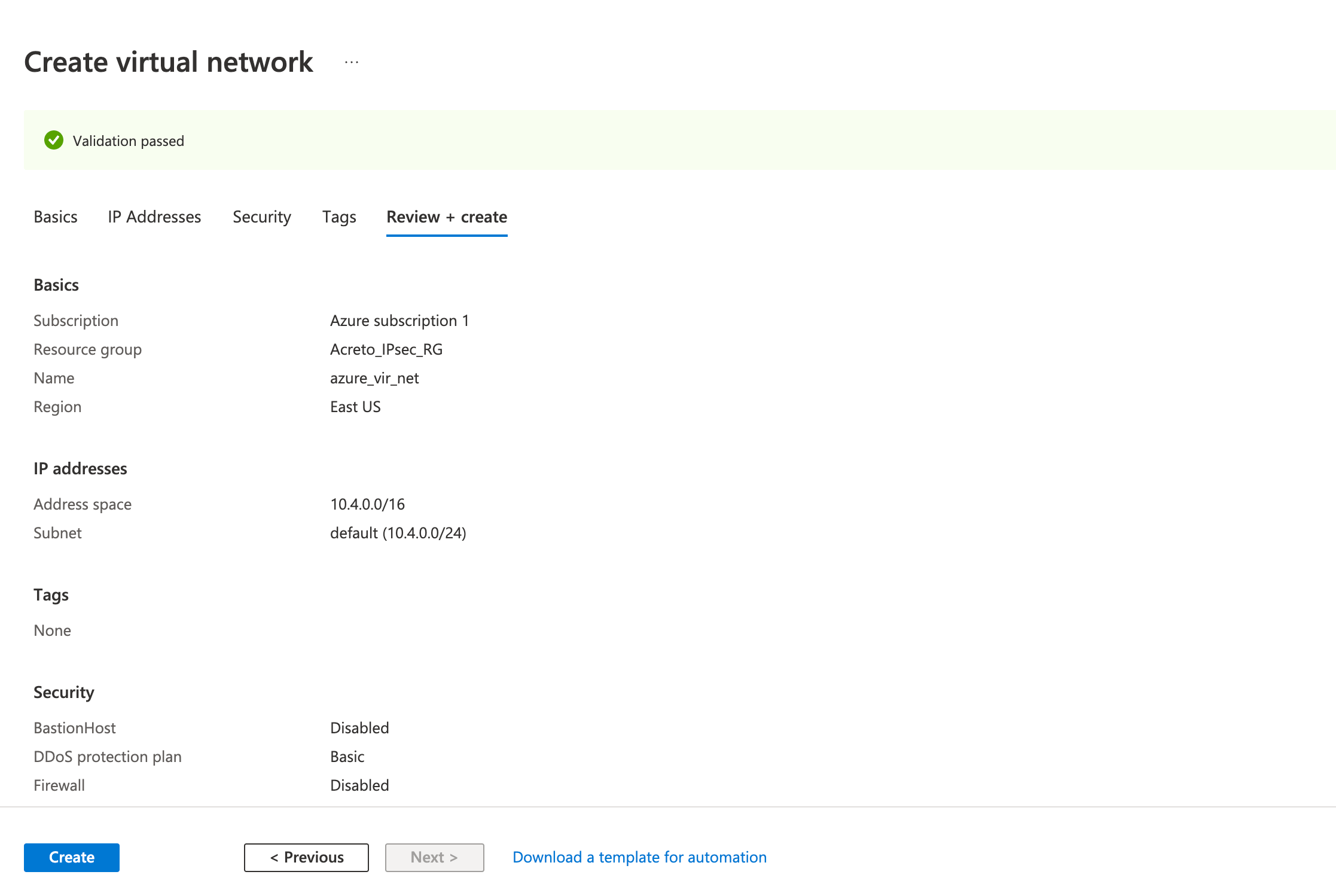

Wait for the deployment to finish and the Virtual Network to be created.
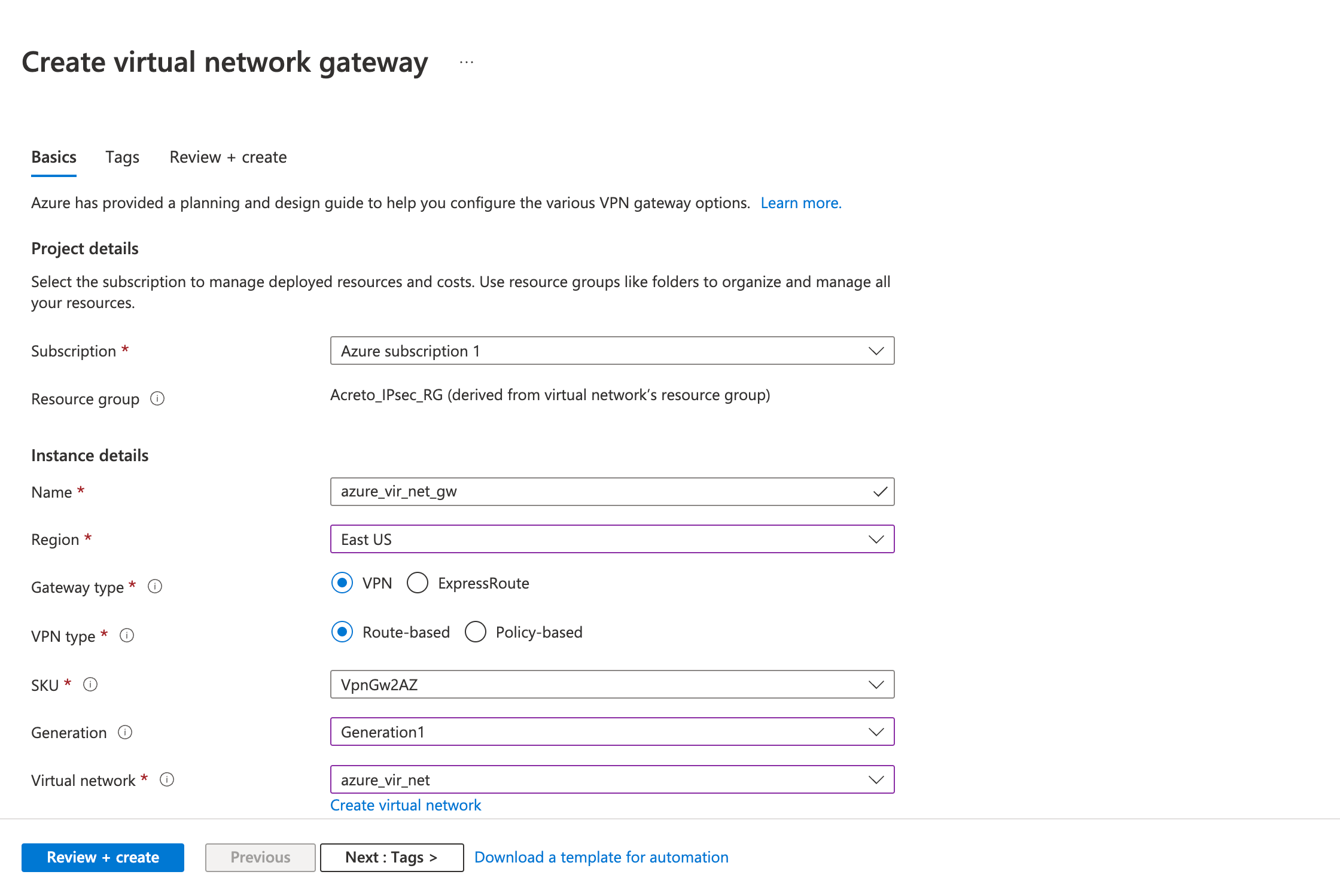
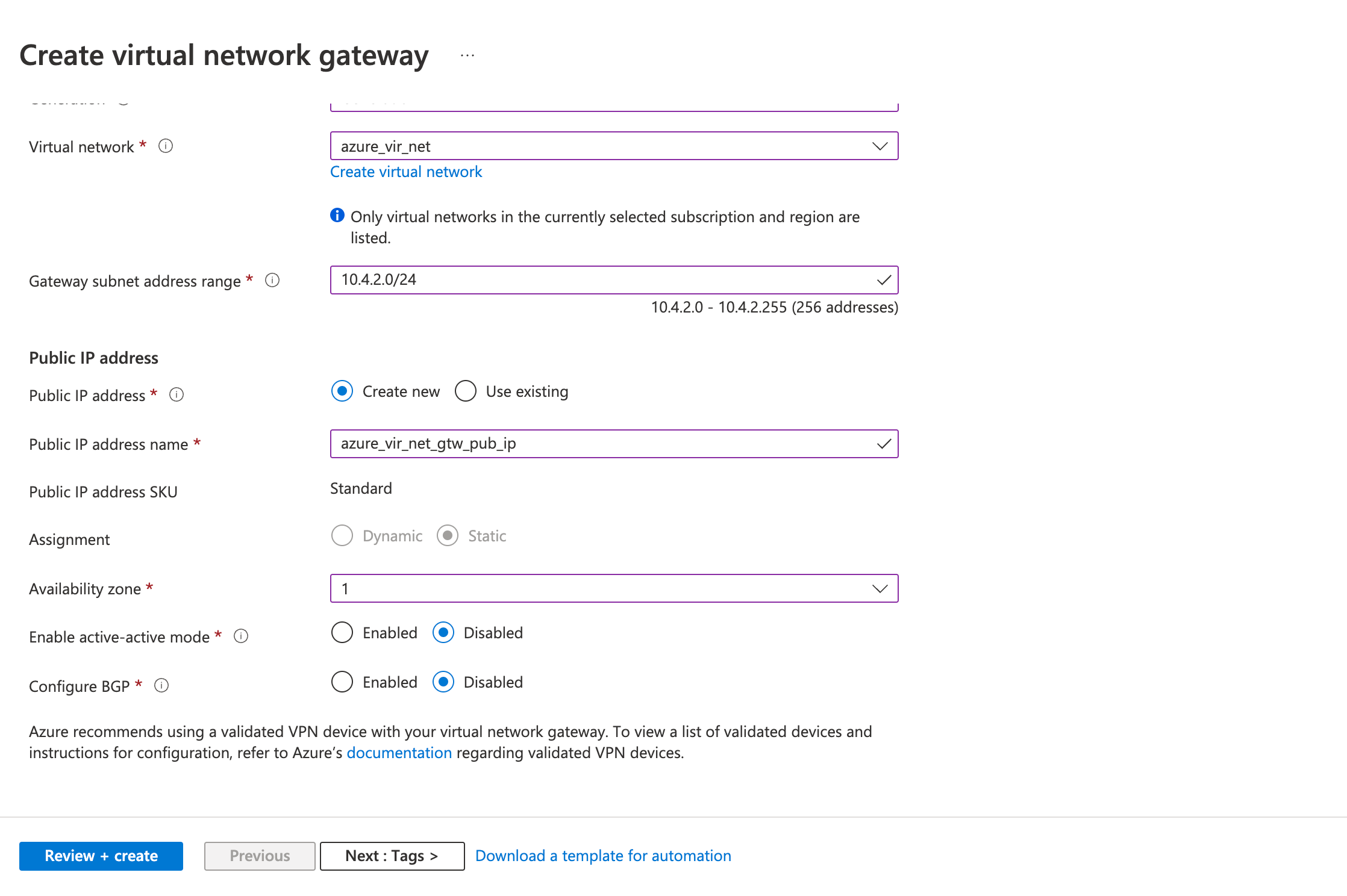
Step 2: Create a VPN gateway
Create the virtual network gateway for your virtual network. Creating a gateway can often take 45 minutes or more, depending on the selected gateway SKU.
- Click on Create a resource
- Click on Networking from the left sidebar
- Click on Virtual network gateway
- Fill in the following fields in the Basics tab.
- Project details
- Subscription
- Instance details
- Public IP address
- Public IP address: Create a new ( or use existing)
- Public IP address name
- Project details
- Review the configurations on the Review + create tab and click Create
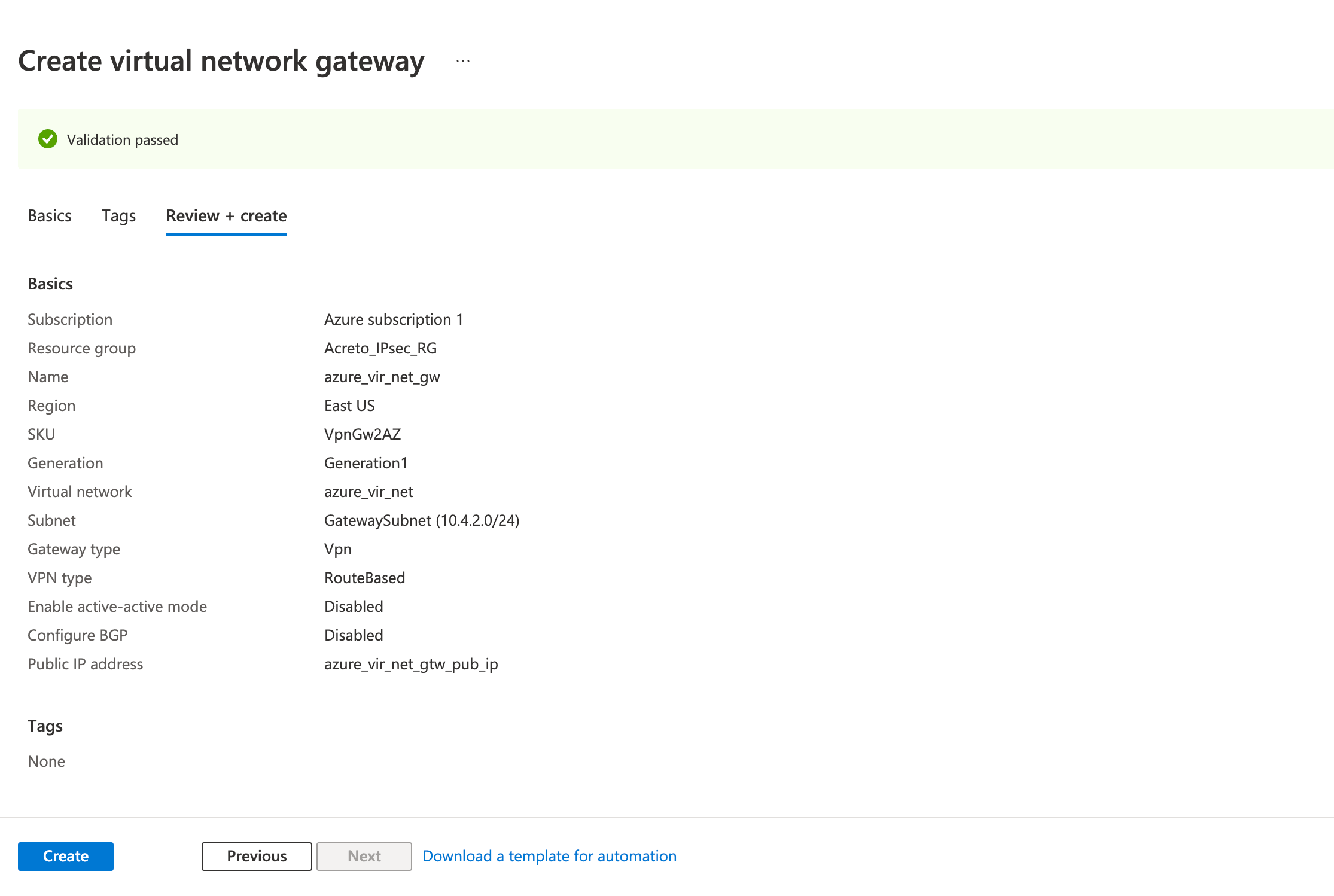

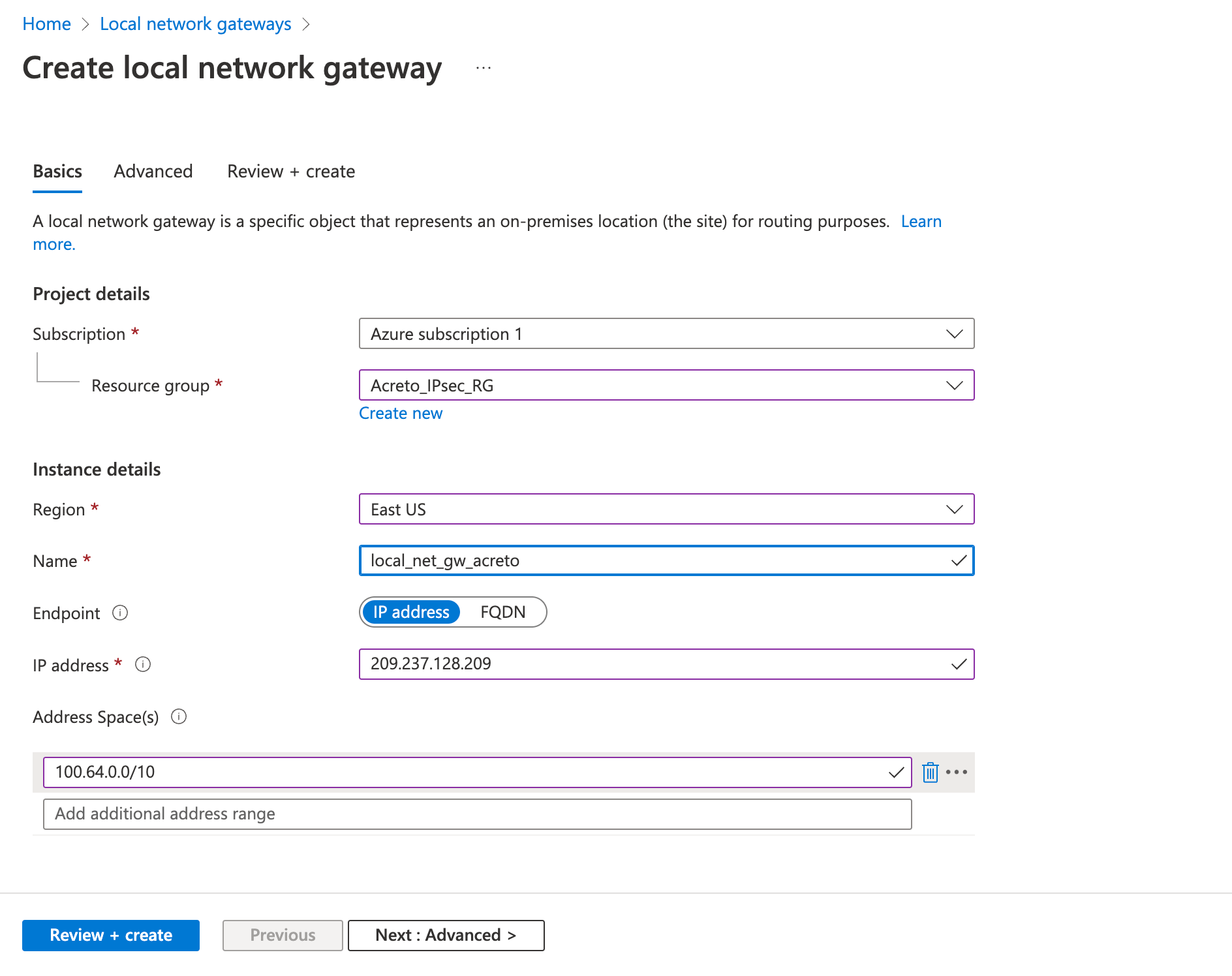
Step 3: Create a local network gateway
The next step is to create a local gateway representing your local network.
- Click on Create a resource
- In the search bar, search for Local Network Gateway
- Click on Create.
- Fill in the following fields in the Basics tab.
- Review the configurations and click Create
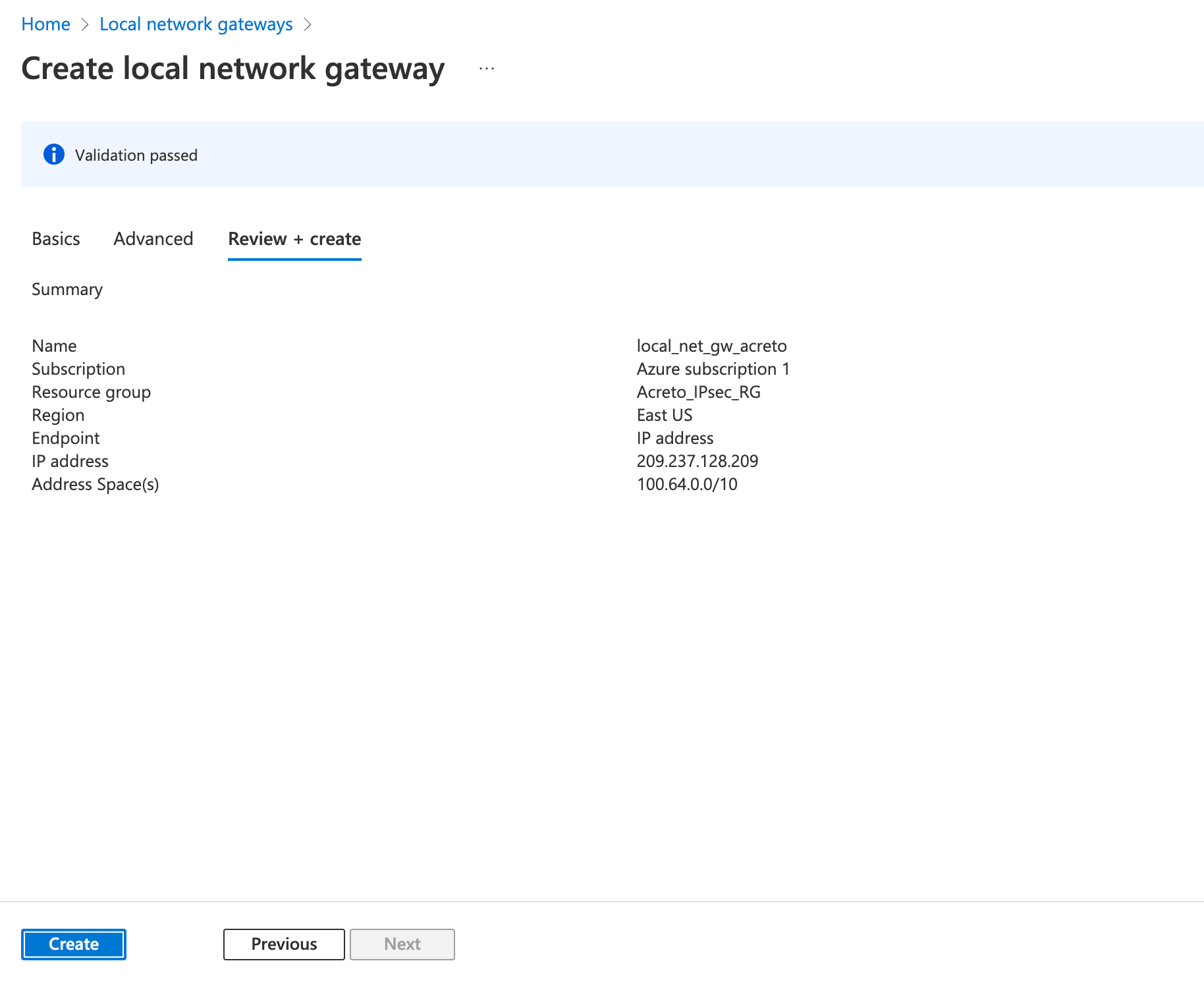

Step 4: Create a VPN connection
This step creates a Site-to-Site VPN connection between your VPN device and the virtual network gateway.
- Click on Create a resource
- In the search bar, search for Connection
- Click on Create.
- On the Basics tab, fill in the following fields:
- Connection type (Site-to-site)
- Subscription (select the same subscription as before)
- Resource group (select the same resource group as before)
- Location (select the same location as before)
- Click on Next
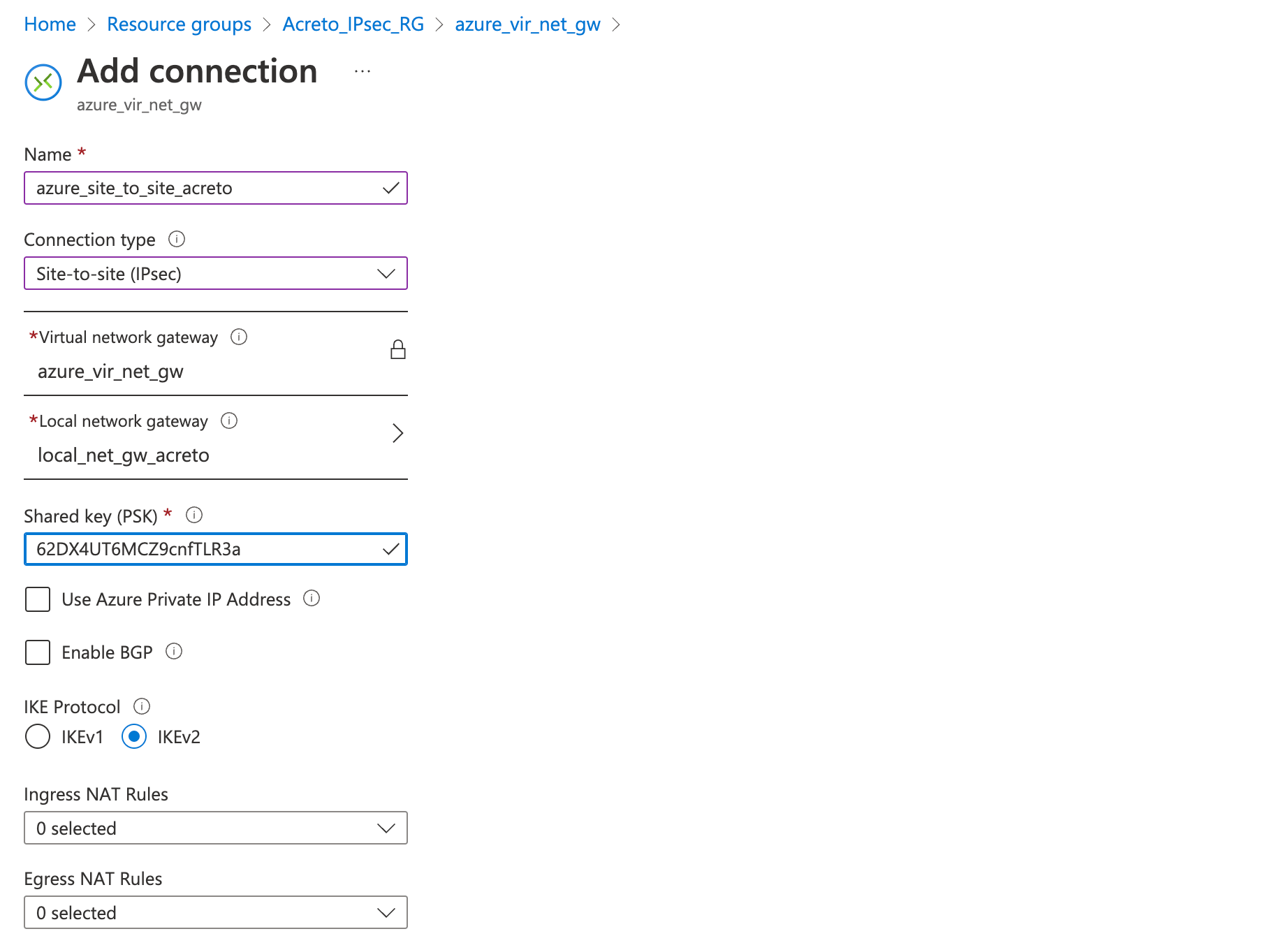
- On the Settings tab, fill in the following fields:
- Virtual network gateway (created in step 2)
- Local network gateway (created in step 3))
- Shared key (create a temporary password)
- Click on Next
- Click on Review + Create

Wait for the deployment to finish and the connection created.
Step 5: Download strongswan configuration
Next, download the VPN configurations from Azure to use it to configure the Acreto gateway.
- Go to the VPN connection created in step 4.
- Click Overview from the left sidebar
- Click Download Configuration
- Select any Device vendor, Device family, and Firmware version of your choice.
- Click the button Download configuration
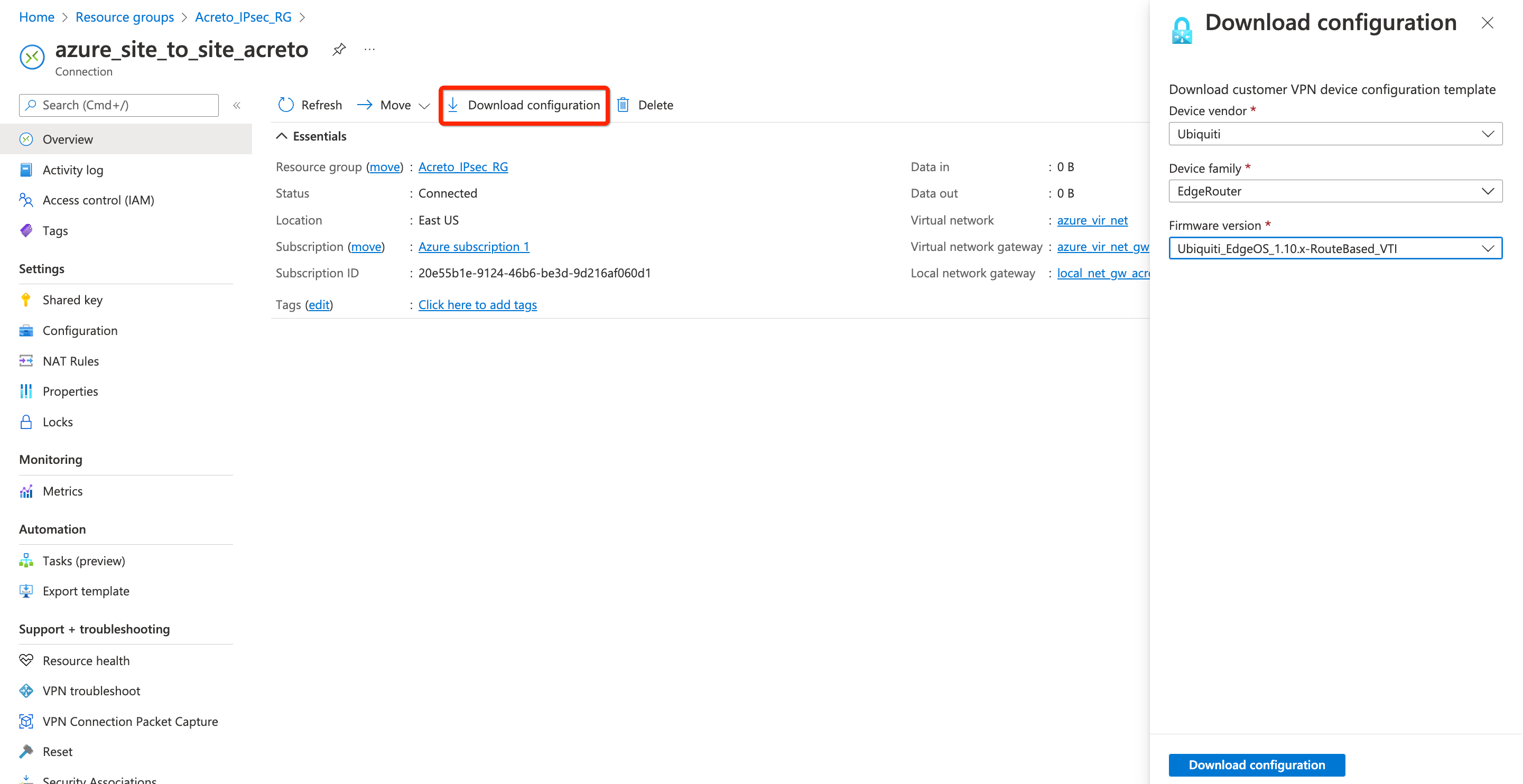

- Open the downloaded file and note the Azure VPN Gateway IP
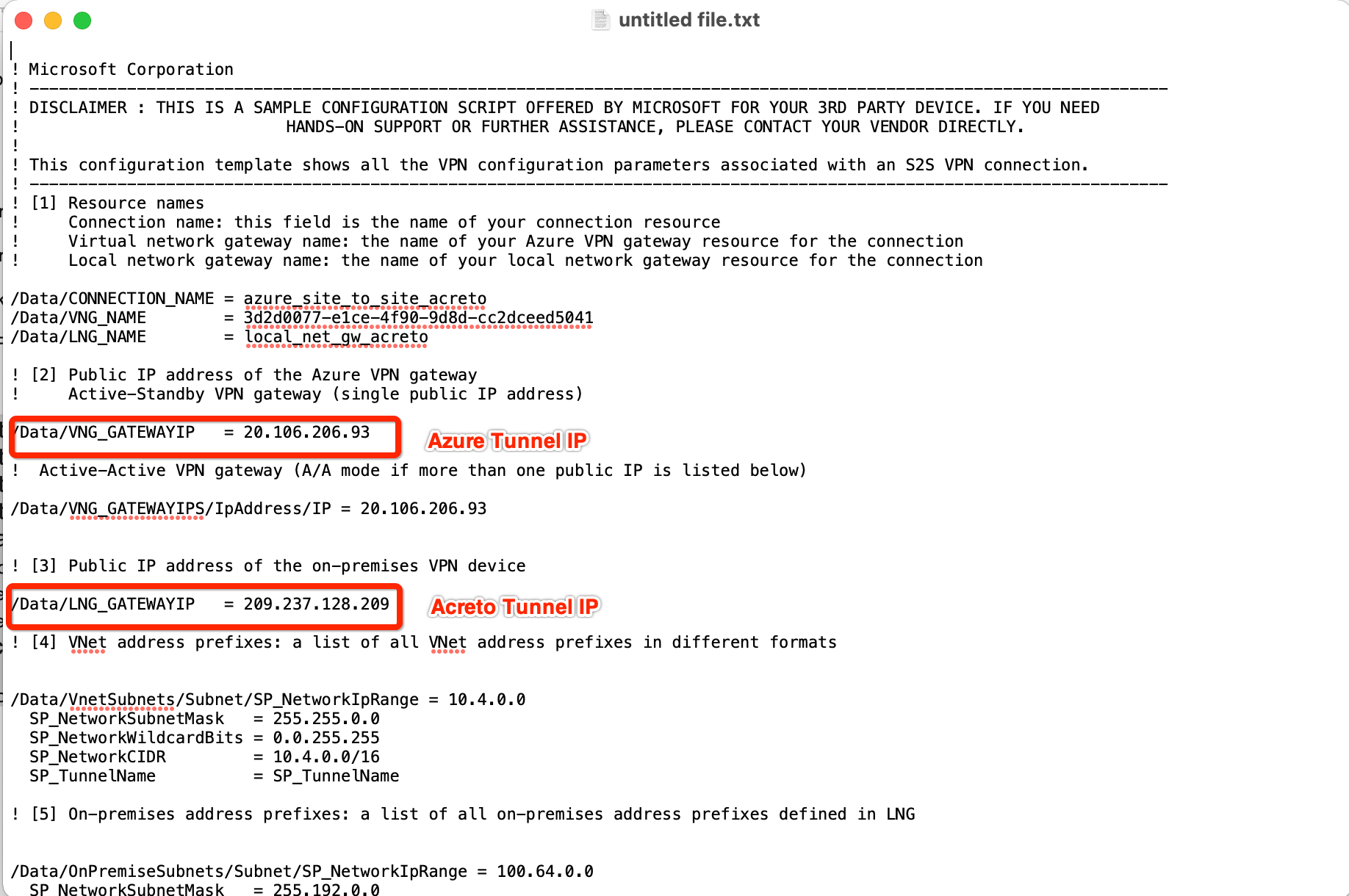

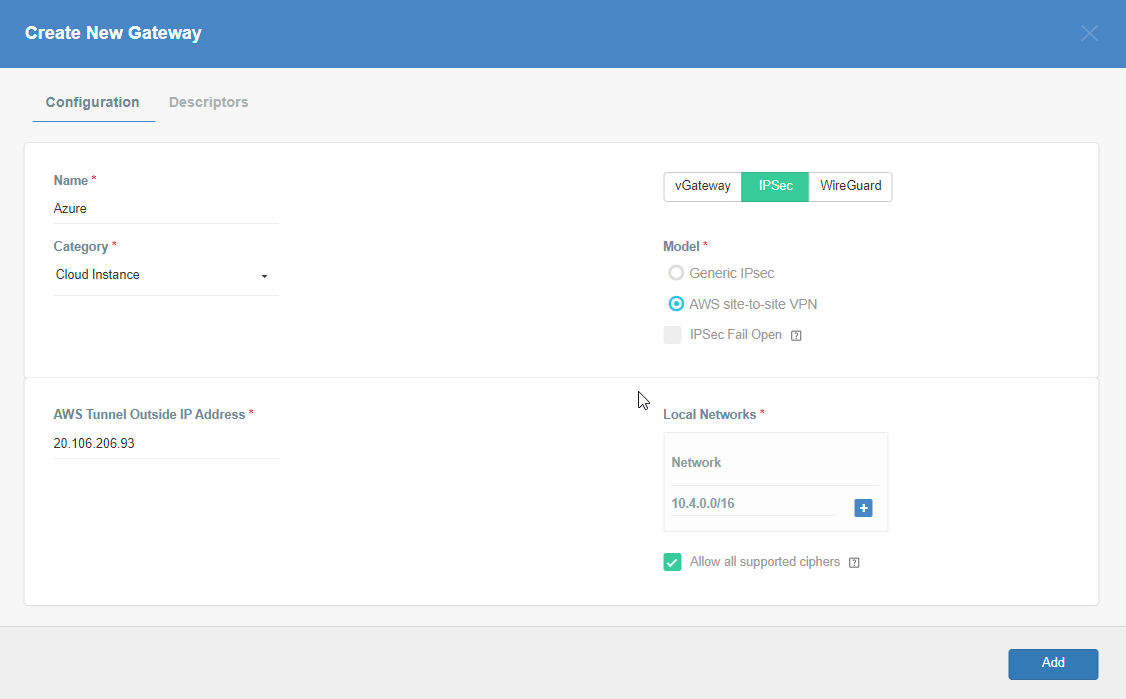
Step 6: Create Gateway on Wedge with option AWS Site-to-Site IPsec and Azure Tunnel IP
Create Gateway on Ecosystem by following the instruction in the link. Provide the following values:
-
Goto Objects » Gateways
-
Add New Gateway
-
Provide the following information :
- Name: Azure
- Category: Cloud Instance
- Type: IPSec
- Model: AWS site-to-site VPN
- AWS Tunnel Outside IP Address: <Azure VPN gateway IP from Step 5>
- Local Network
Step 7: Read the Configuration
Read the PSK information from the Acreto gateway created in the previous steps.
- Click the gateway created on Acreto in Step 5.
- Click the Play button under Configuration Options to generate the strongSwan Config.
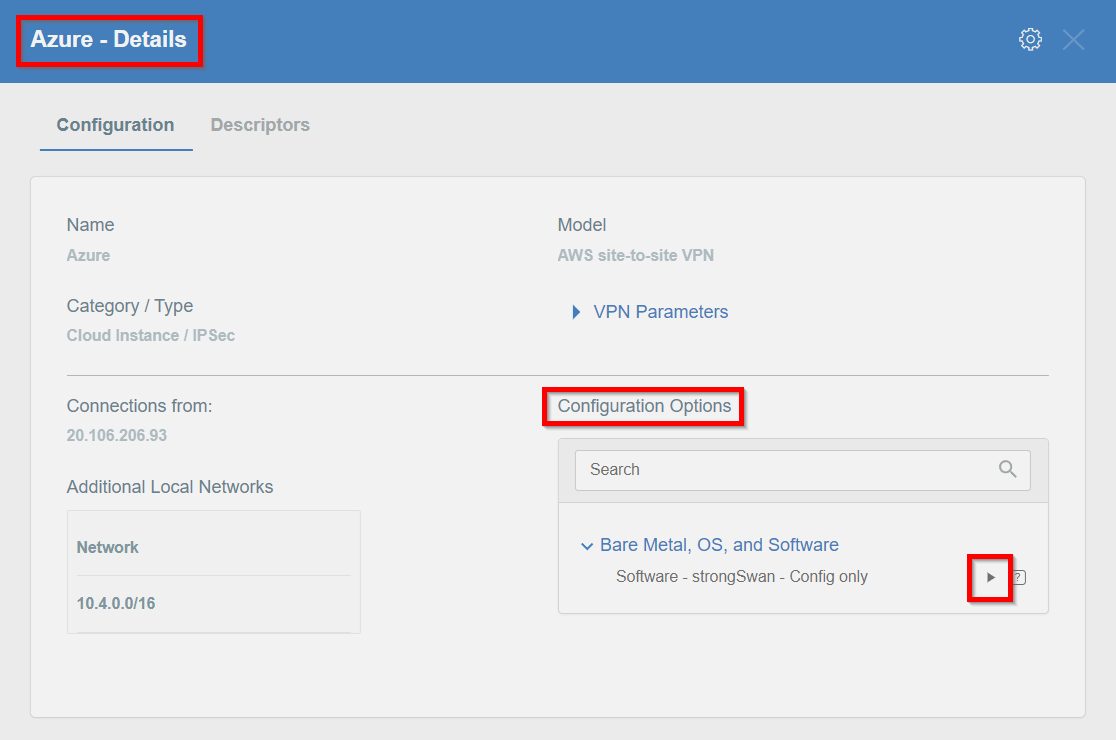

- Once the Config file is generated, click the Download button to download the configuration on the local computer.
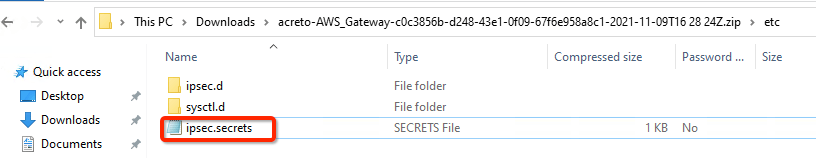

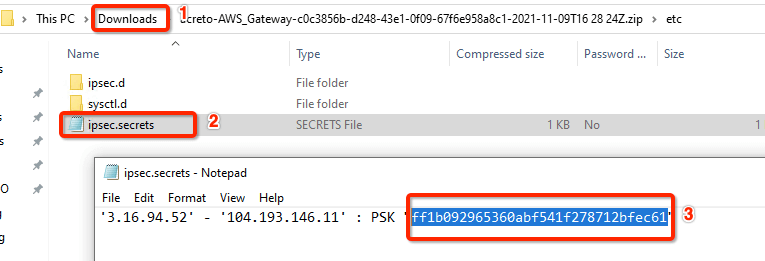
- Unzip the downloaded file and copy the PSK from the file ipsec.secrets

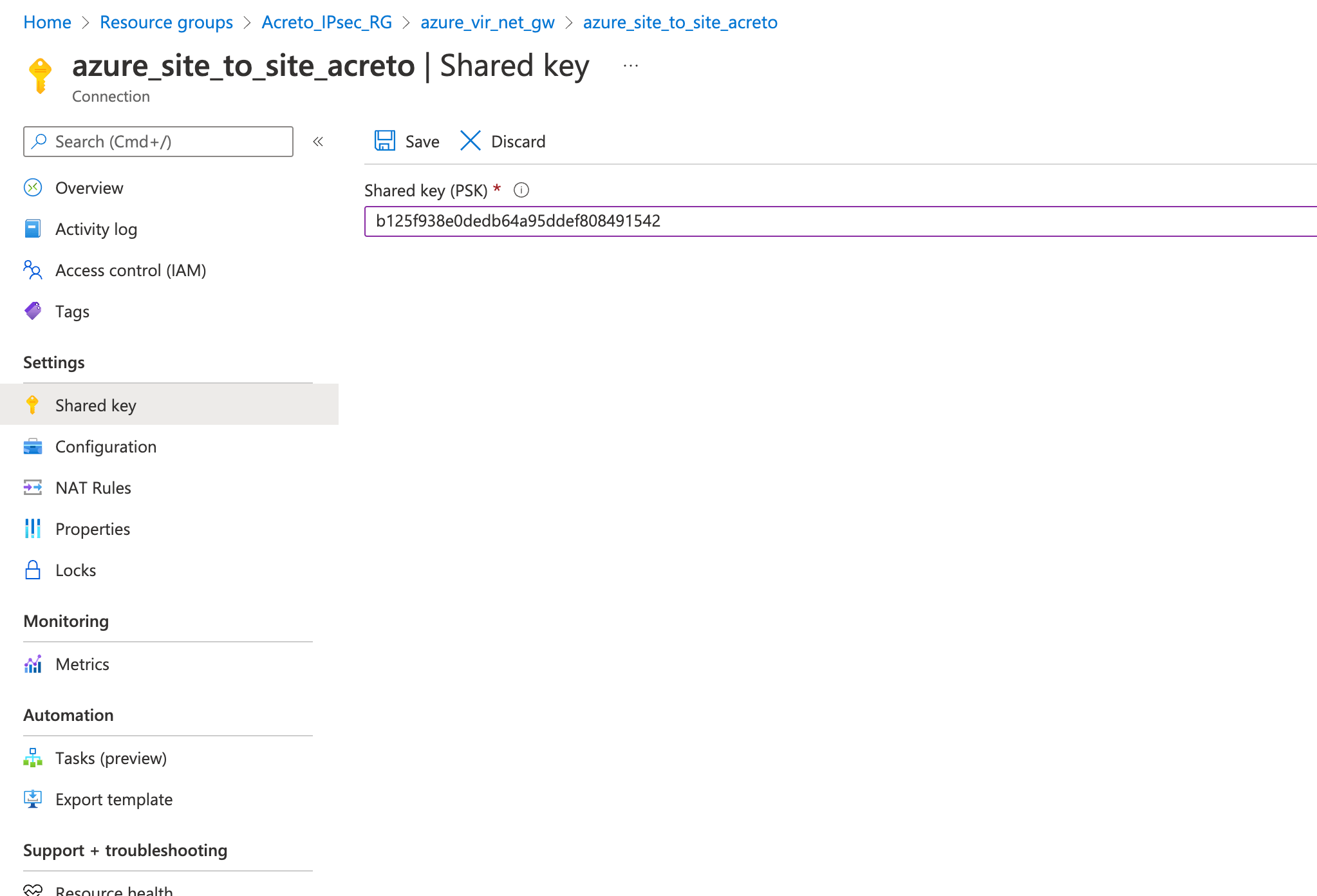
Step 8: Update the PSK from Wedge in Azure VPN
Update the new PSK from the previous step and update the VPN connection on Azure.
- Goto VPN connection created in step 4
- From the left sidebar, click Settings » Shared key
- Update the Shared key (PSK) from the Step 7
- Save

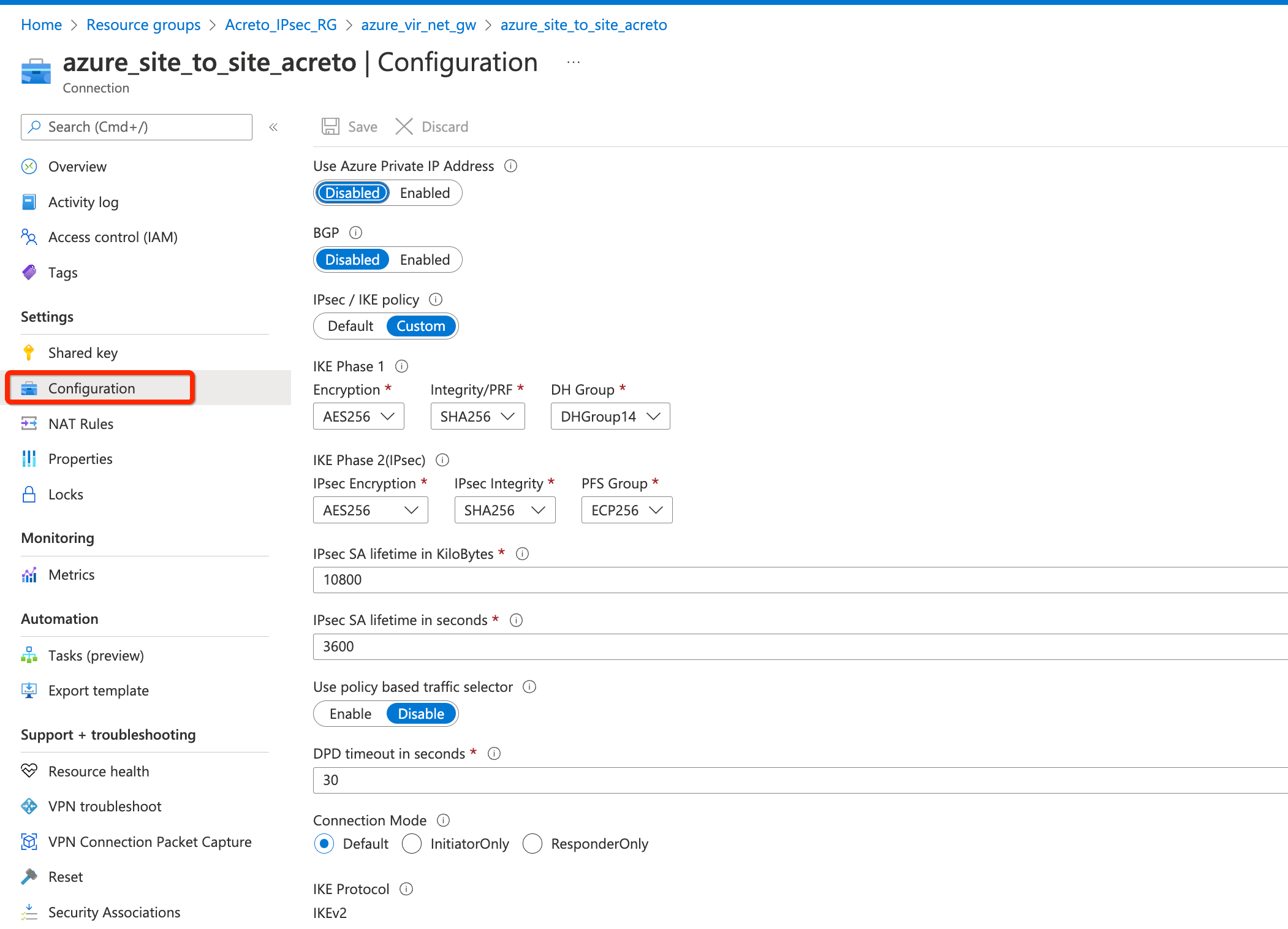
Step 9: Update IPsec Parameter
- Goto VPN connection created in step 4.
- From the left sidebar, click Settings » Configuration
- Update the following
- IPsec / IKE policy - Custom
- IKE Phase 1
- Encryption - AES256
- Integrity/PRF - SHA256
- DH Group - DHGroup14
- IKE Phase 2(IPsec)
- Encryption - AES256
- Integrity/PRF - SHA256
- DH Group - ECP256
- IPsec SA lifetime in seconds - 3600
- DPD timeout in seconds - 30
- Save.

Step 10: Check Connection
- Goto VPN connection created in step 4.
- From the left sidebar, click Settings » Connections
- Give a few minutes for changes to be effective.
- Once all the configurations are saved, the status of the VPN connection will be shown as Connected.


References and Related Articles
What is Azure Site-to-Site connection?
Summary
Acreto IPsec Gateway allows to set up VPN tunnel to connect Acreto Ecosystem with Azure VPN Gateway.