Fortinet FortiGate Dual VPN setup
Before You Start
Overview
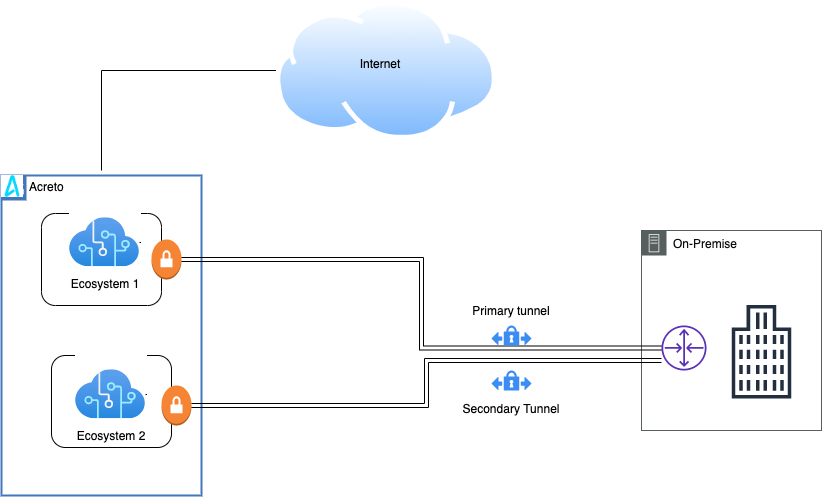
This article illustrates a Dual VPN setup and explains how to connect the secondary tunnel from your environment to the second Ecosystem which can act as a backup in case of failure of the Primary ISP or Ecosystem. With this setup, when the first tunnel is down, the traffic will automatically start going through the second tunnel to the backup Ecosystem.

Prerequisites
- FortiGate installation
- Ecosystem set up with proper security policies
How-To
Create Gateway for IPsec
Firstly, you will need to create a new Gateway device in the Acreto platform. Instructions on how to create a new Gateway are available here.
- Name: IPsec connection name must meet the same requirements as the Strongswan connection name (letters and numbers only).
- Category: IoT
- Type: IPsec
- Allow connection from: Empty (describes the source IP address where the IPsec connection will be permitted).
- Local Networks: any local network addresses that will be routed through this gateway.
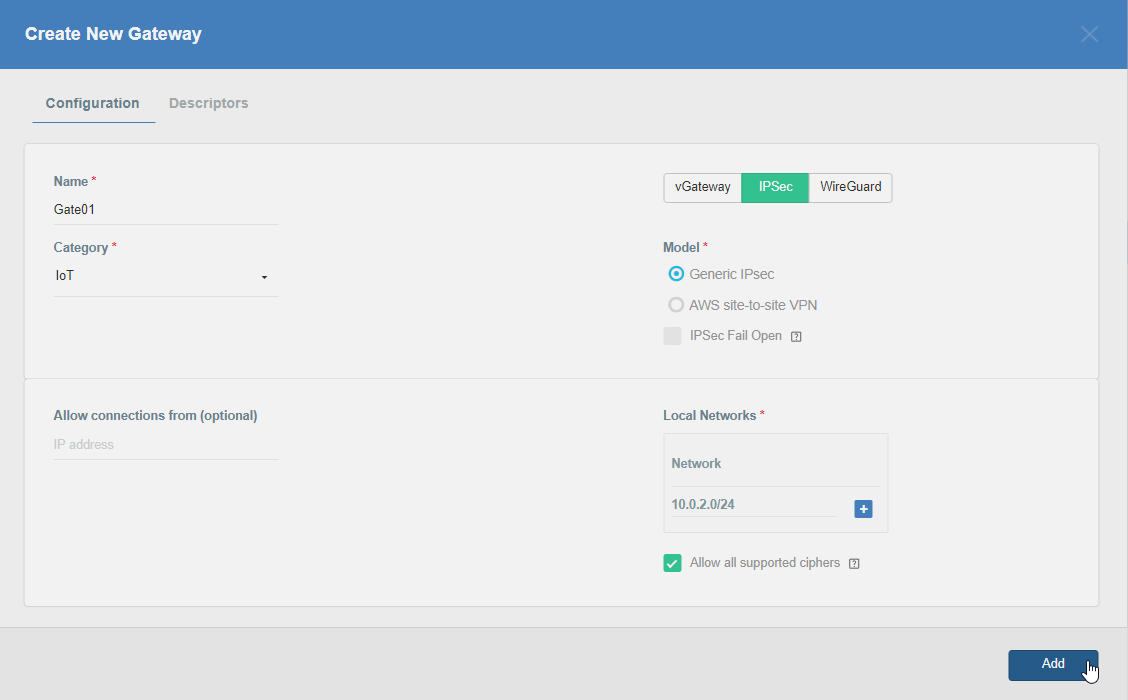

To simplify testing, add the IP addresses of all interfaces connected to your gateway as Local Networks (you can use /32 prefix for public interface). This will allow you to test connectivity from the gateway through Acreto by using Ping, Traceroute, or similar tools.
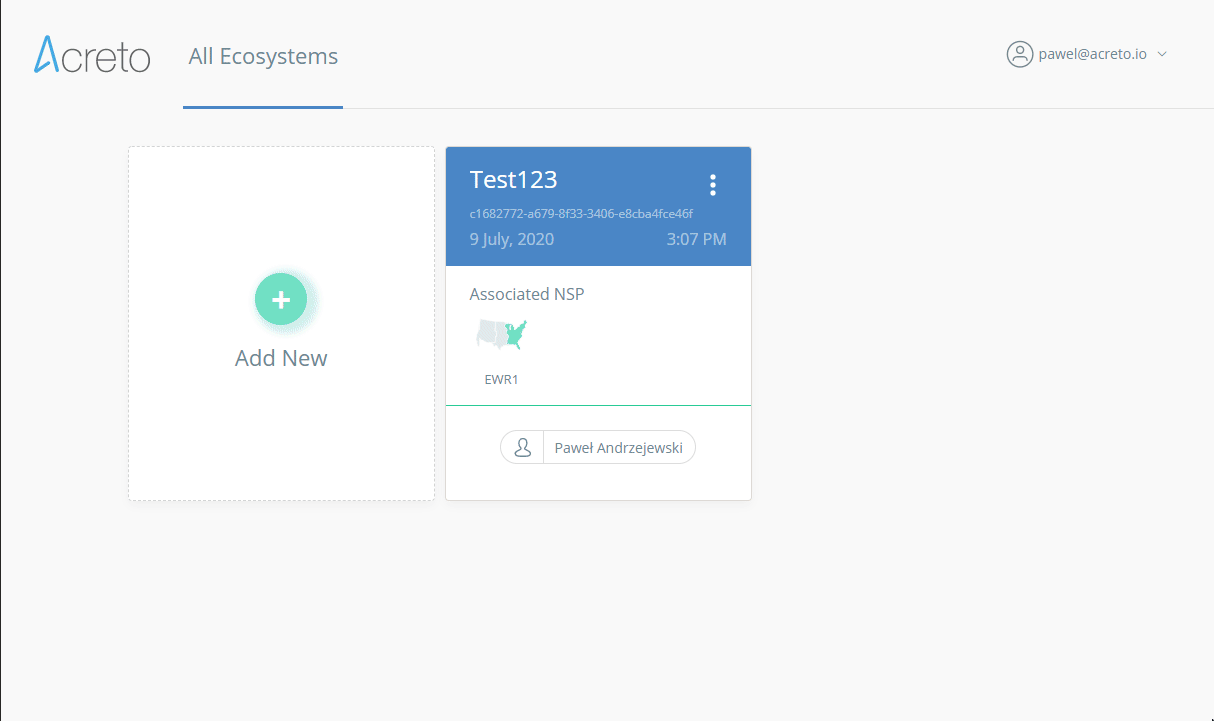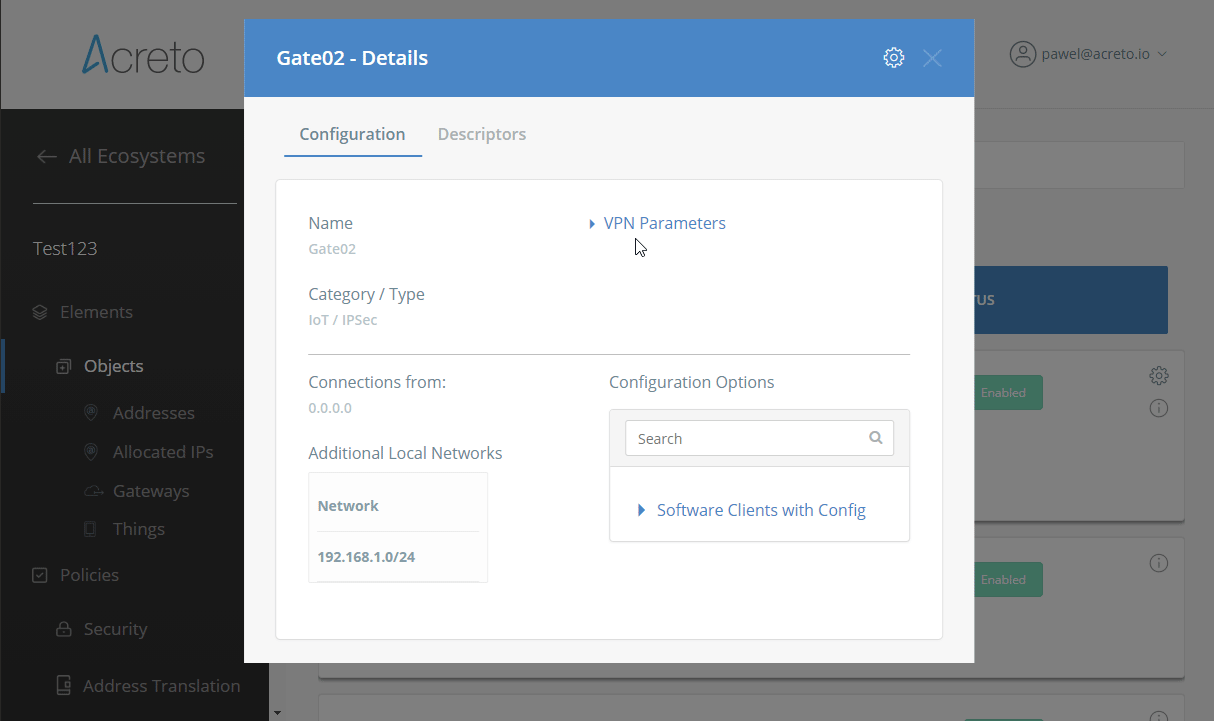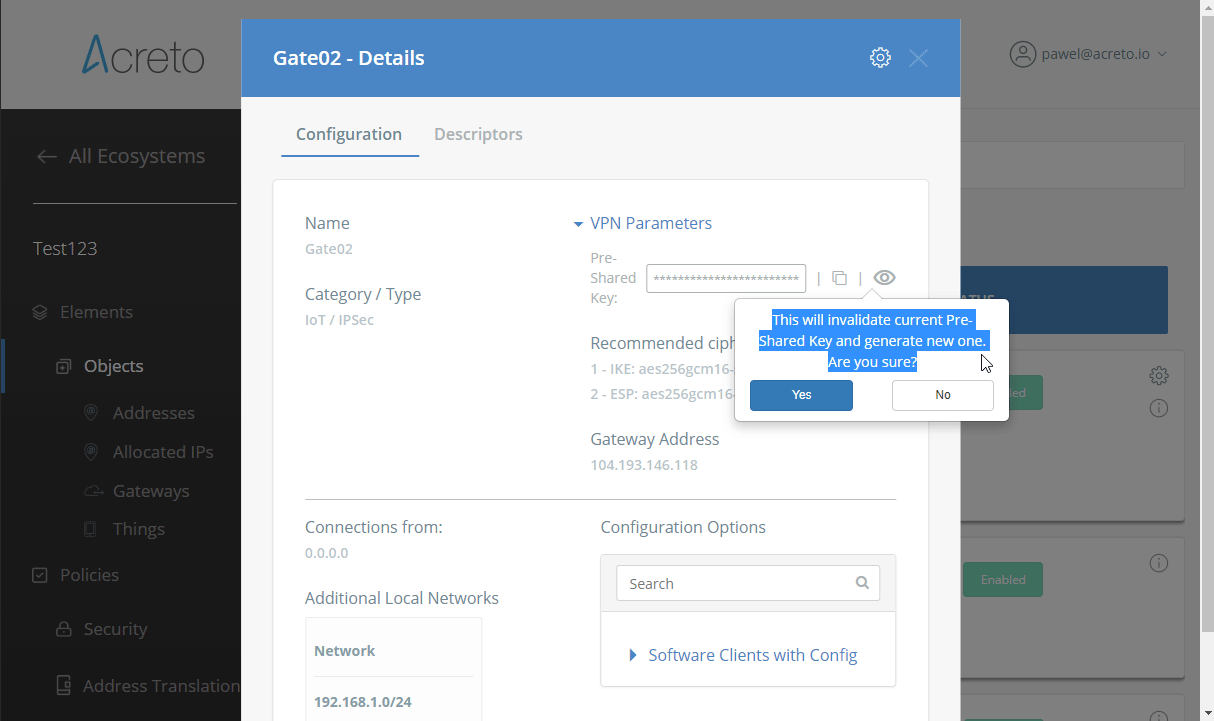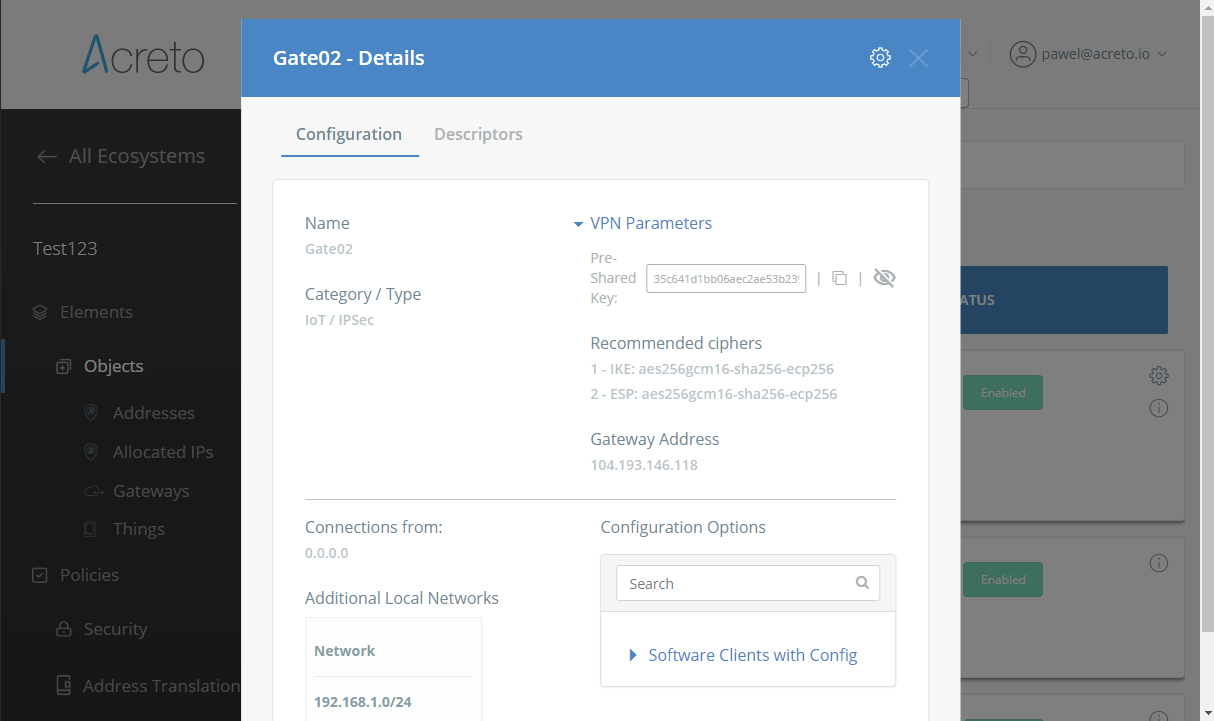
Task 1: Read IPsec Gateway Values Required for FortiGate Configuration
To proceed with the FortiGate configuration, you will need a few values from an existing committed Acreto Gateway:
- Gateway Address
- Pre-Shared Key
- Recommended Ciphers
All of these may be found within the Gateway details panel - view the below animation for further instruction.
Task 2. Configure Primary Tunnel on FortiGate with Acreto Primary EcoSystem
- In FortiGate, go to VPN > IPsec Tunnels. From Create New drop-down menu, select IPsec Tunnel

- In the next window, give the primary tunnel name and click on Custom and click on Next.

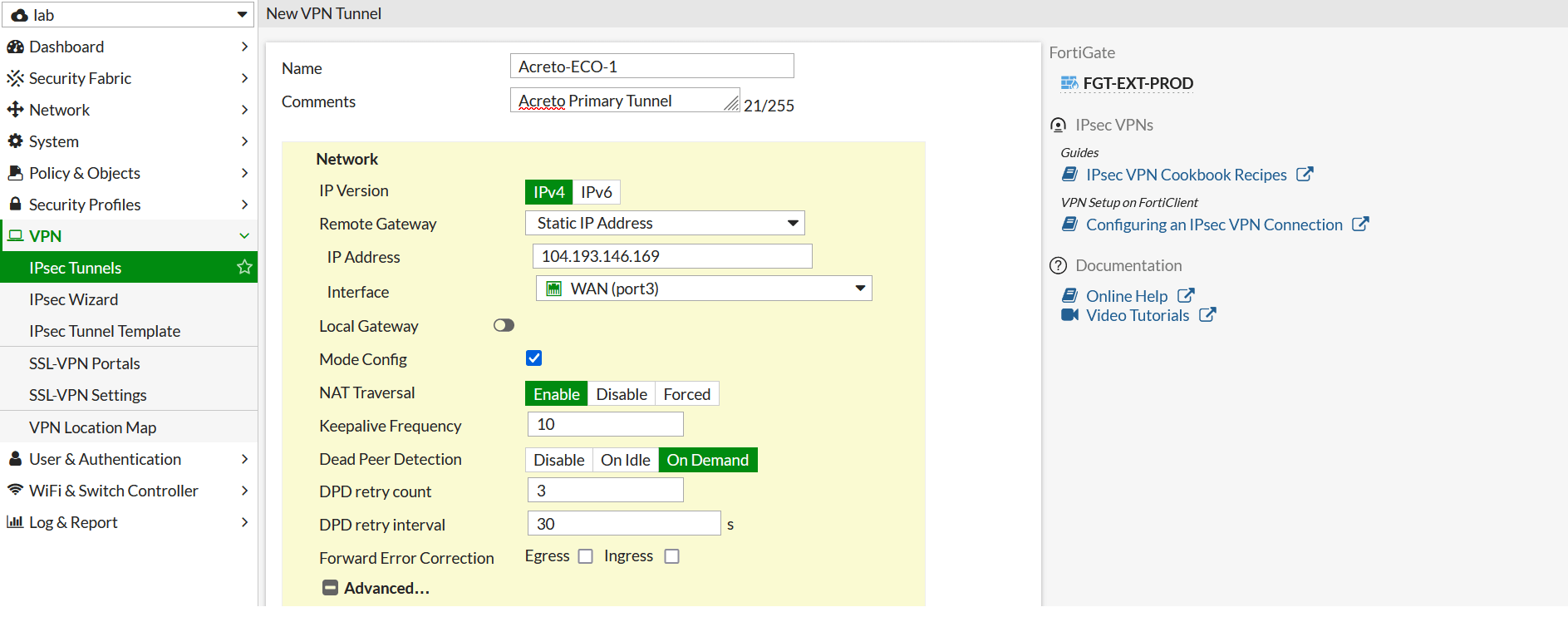
- Configure the following VPN settings:
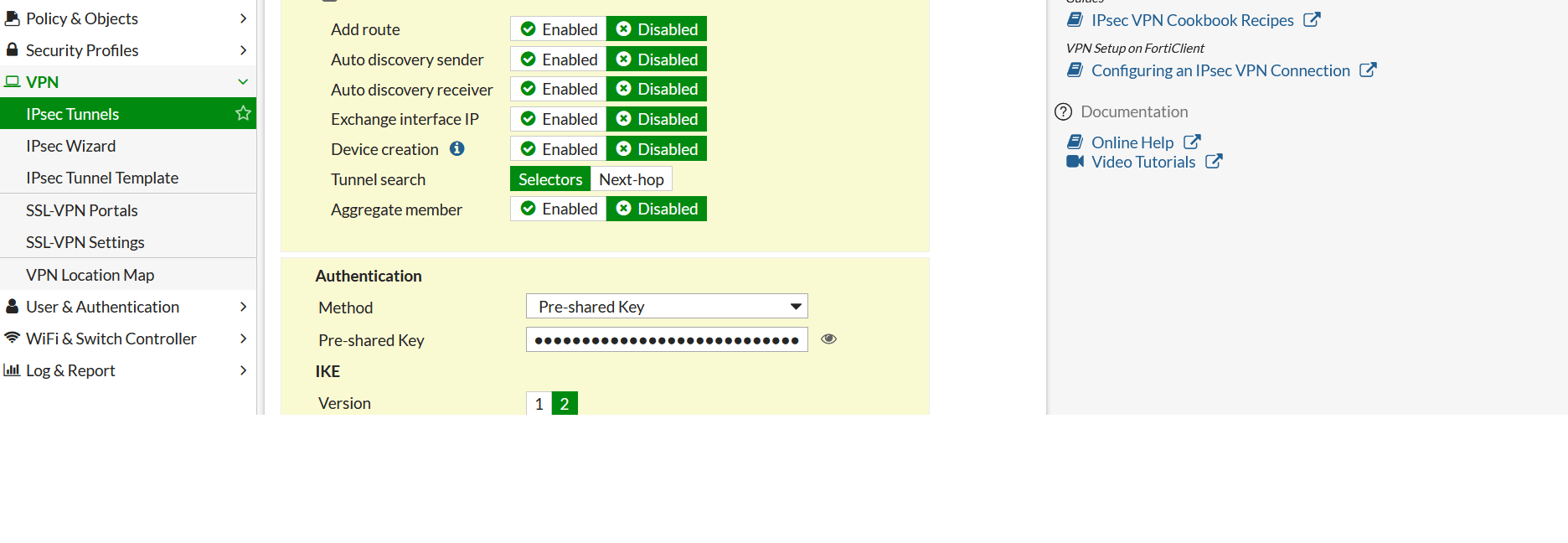
- Expand Advance Option and configure as below:
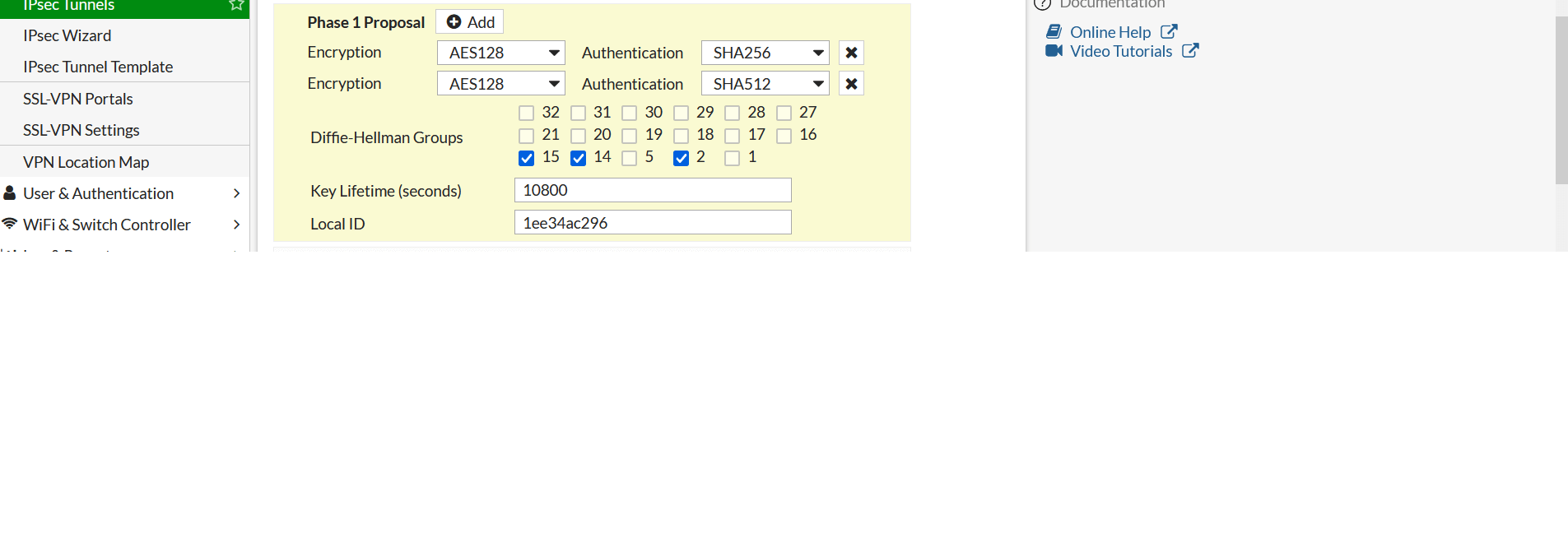
- In Phase1 Proposal. Delete all proposals except two as below:
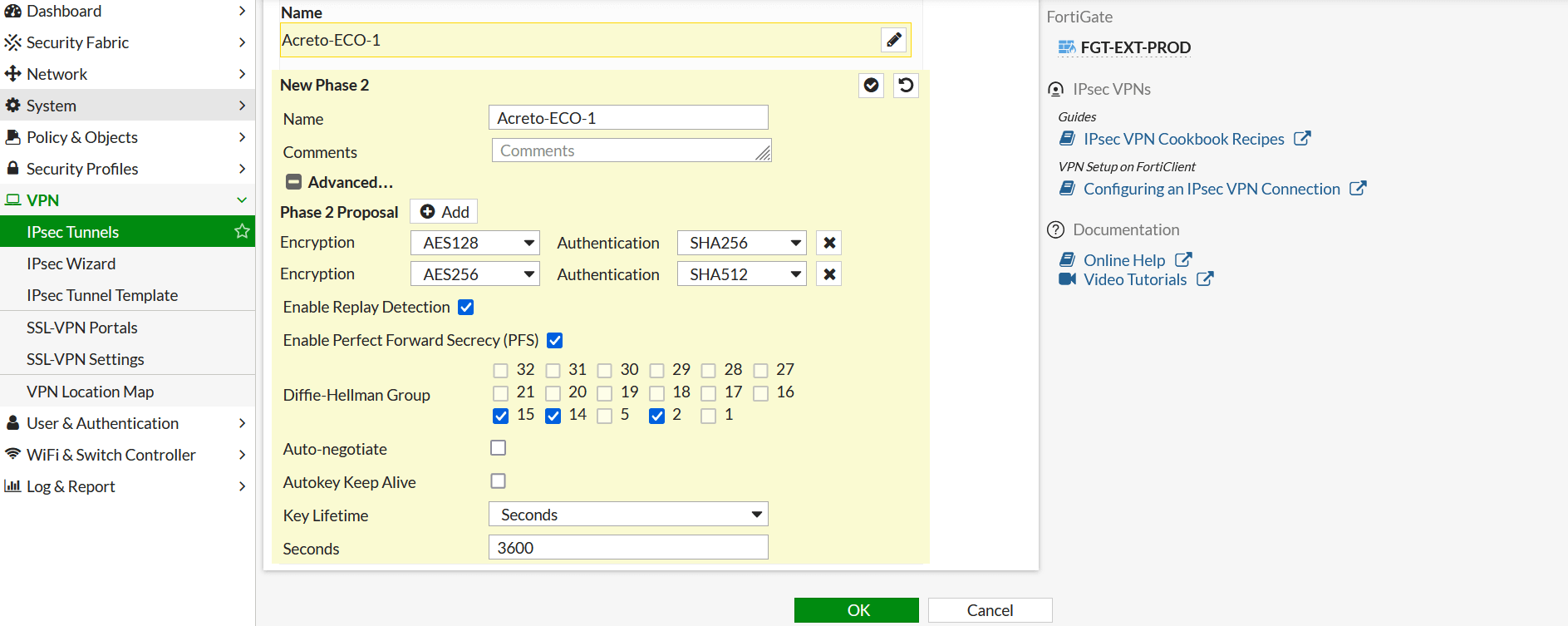
- In Phase2 setting, please enter below:
- Click OK to save the VPN setting.
Task 3. Configure Secondary Tunnel on FortiGate with Acreto Secondary EcoSystem
- Repeat the above steps for the creation of a secondary tunnel. We will use Acreto-ECO-2 as the name of a secondary tunnel in this article.
Task 4. Configure IPs on Tunnel Interfaces
This step is required for policy routing to work. Any dummy/unused IPs can be used for interfaces.
- Go to Network > Interfaces. Select Acreto-ECO-1 Tunnel interface and click on Edit
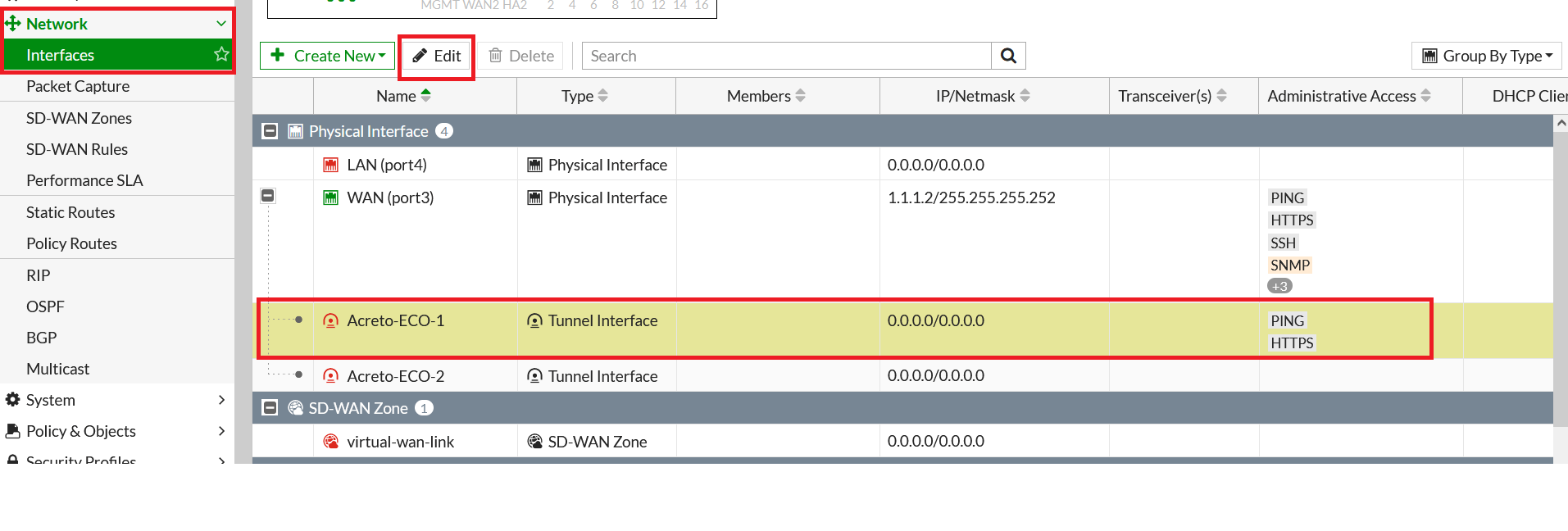

- Configure IP as below:
- IP: 169.254.254.1
- Remote IP: 169.254.254.2/32
- Click on Save
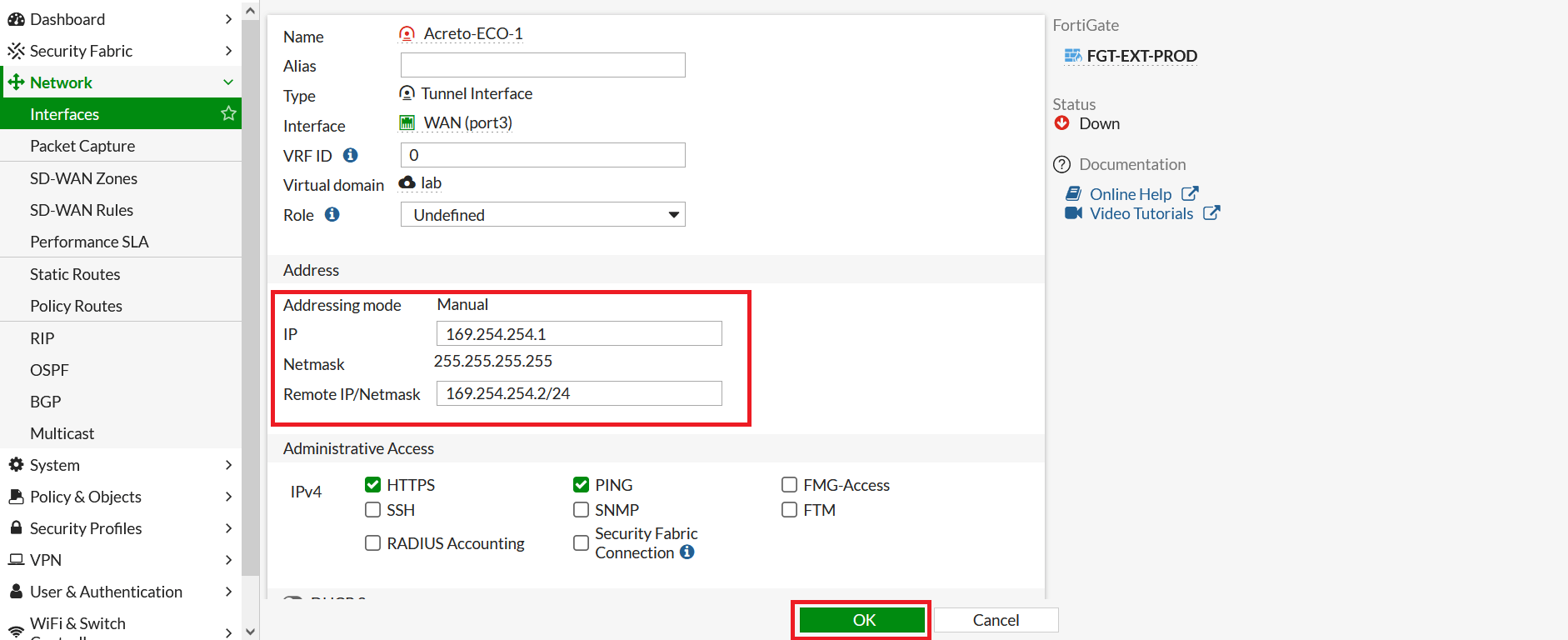

- Repeat the step to configure IP on the secondary tunnel interface.
- Go to Network > Interfaces. Select Acreto-ECO-2 Tunnel interface and click on Edit.
- Configure IP as below:
- IP: 169.254.254.3
- Remote IP: 169.254.254.4/32
- Click on Save.

Task 5. Configure Routing for VPN Traffic
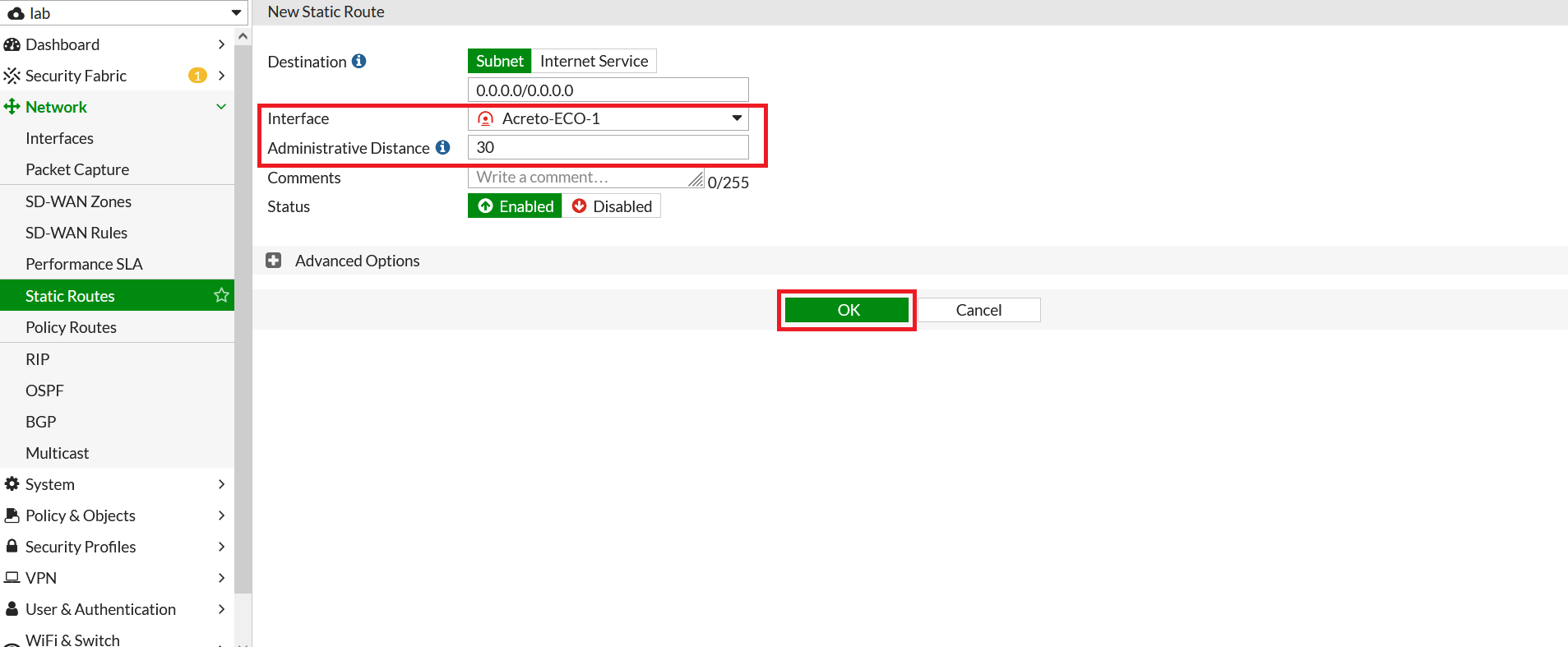
- Go to Network > Static Route. Click on Create New.

- In the next window, configure the static route as below:
- Destination: 0.0.0.0/0
- Interface: Acreto-ECO-1 (Acreato-primary-tunnel)
- Administrative Distance: 30
- Click on Save

- Repeat the step to configure a static route for the secondary tunnel.
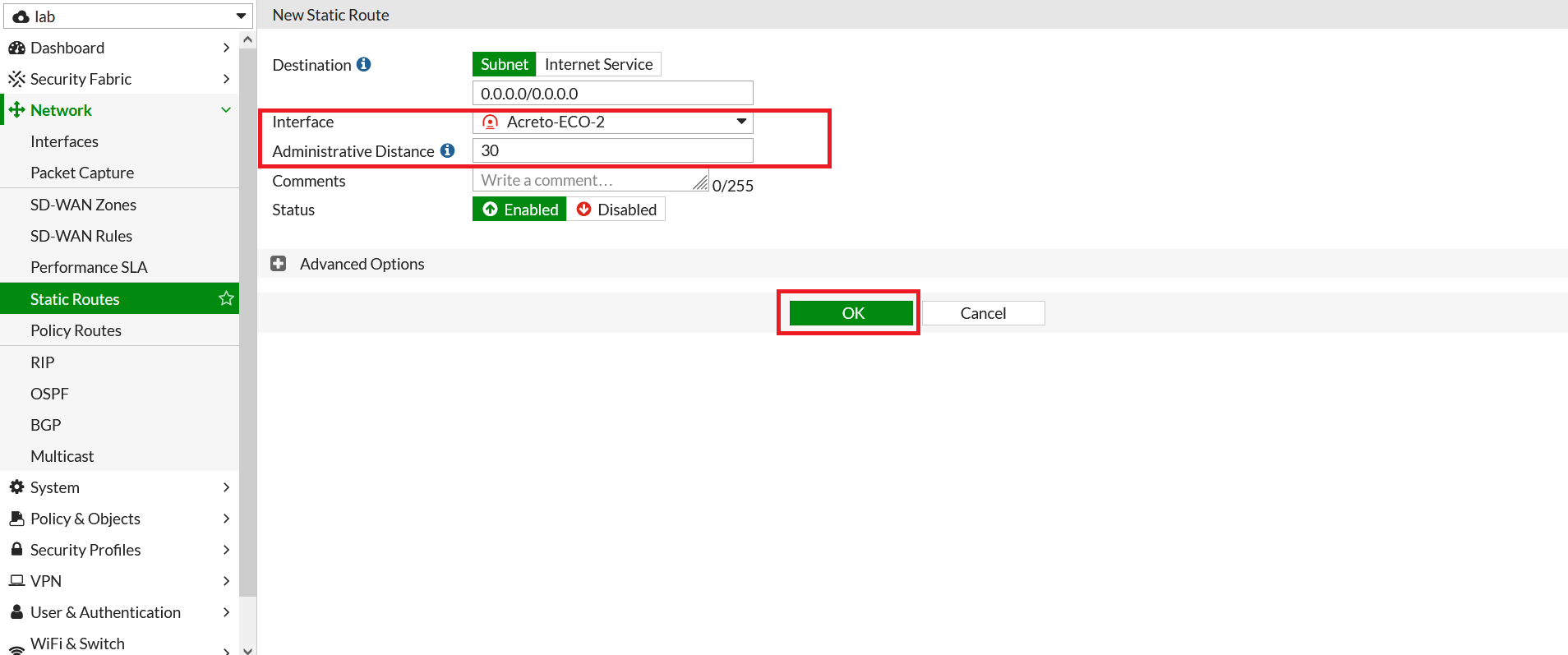
- Go to Network > Static Route. Click on Create New.
- In the next window, configure the static route as below:
- Destination: 0.0.0.0/0
- Interface: Acreto-ECO-2 (Acreato-secondary-tunnel)
- Administrative Distance: 30
- Click on Save

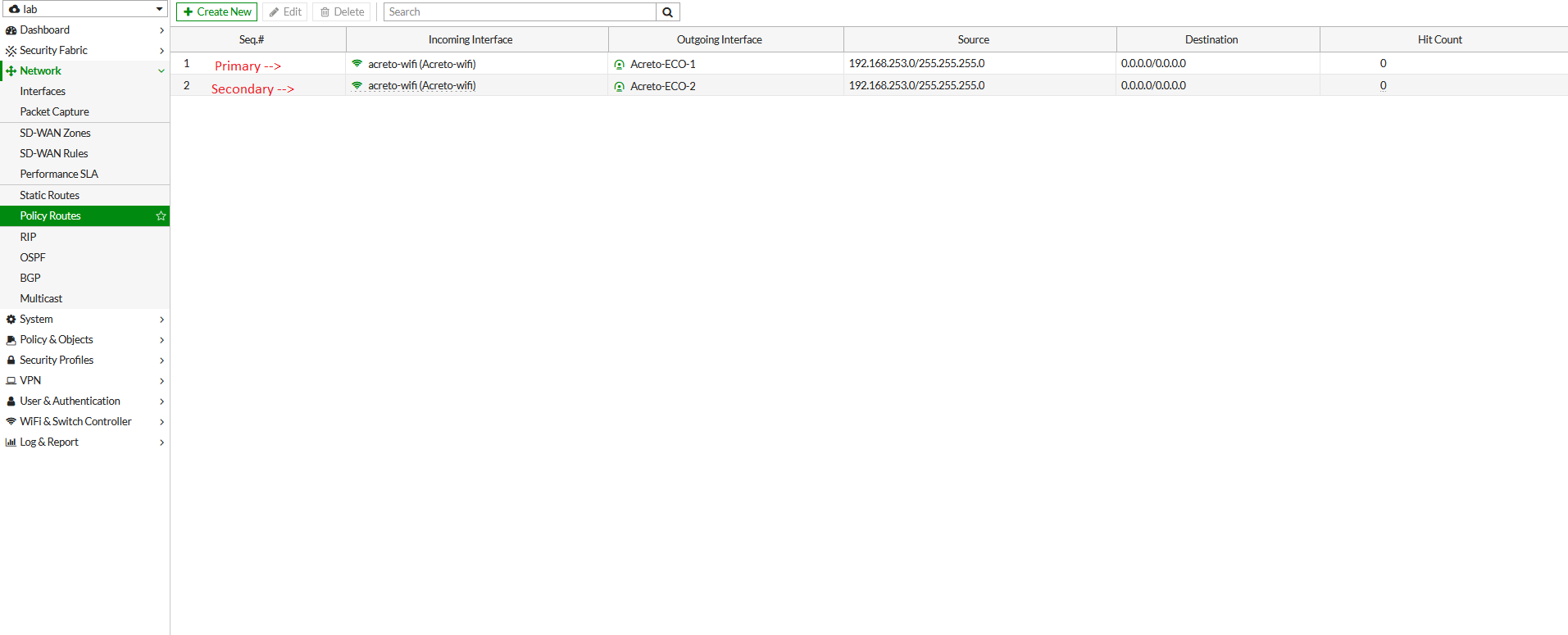
Task 6. Configure Policy Route on FortiGate for Traffic from LAN to Acreto.
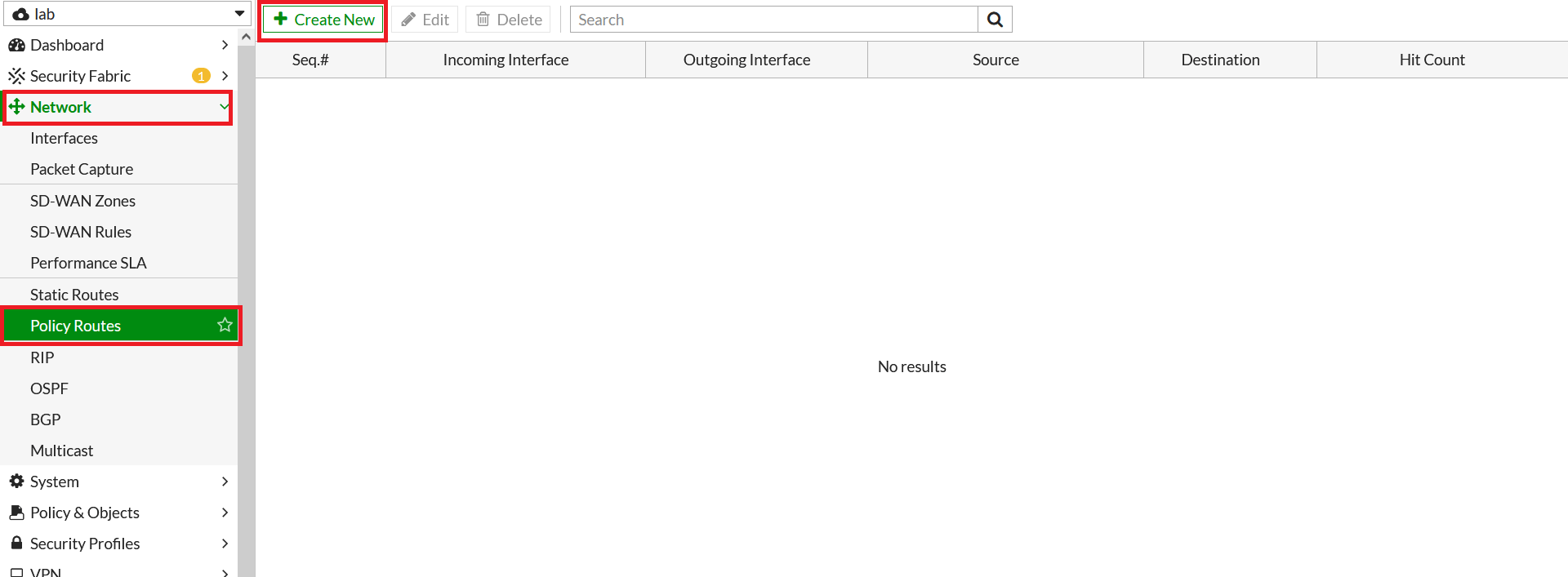
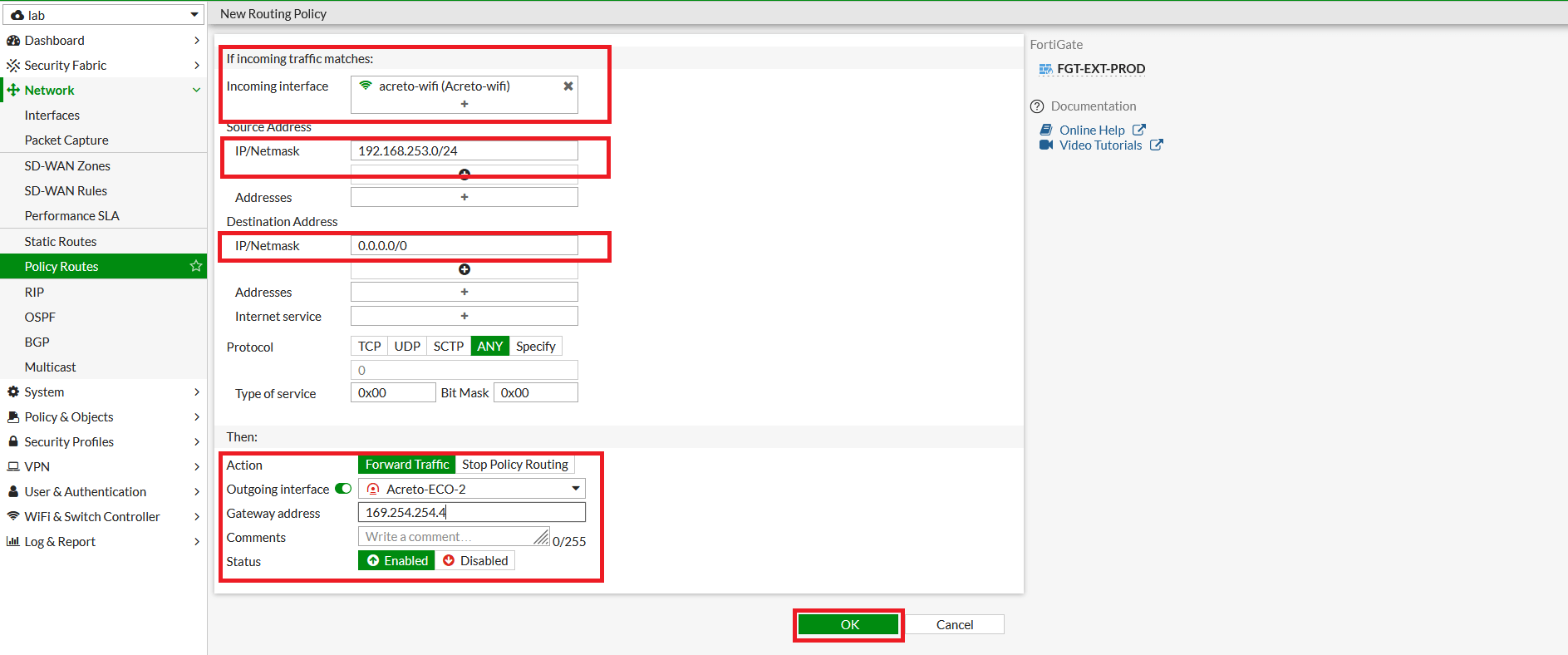
- To configure the policy route, Go to Network > Policy Route. Click on Create New.

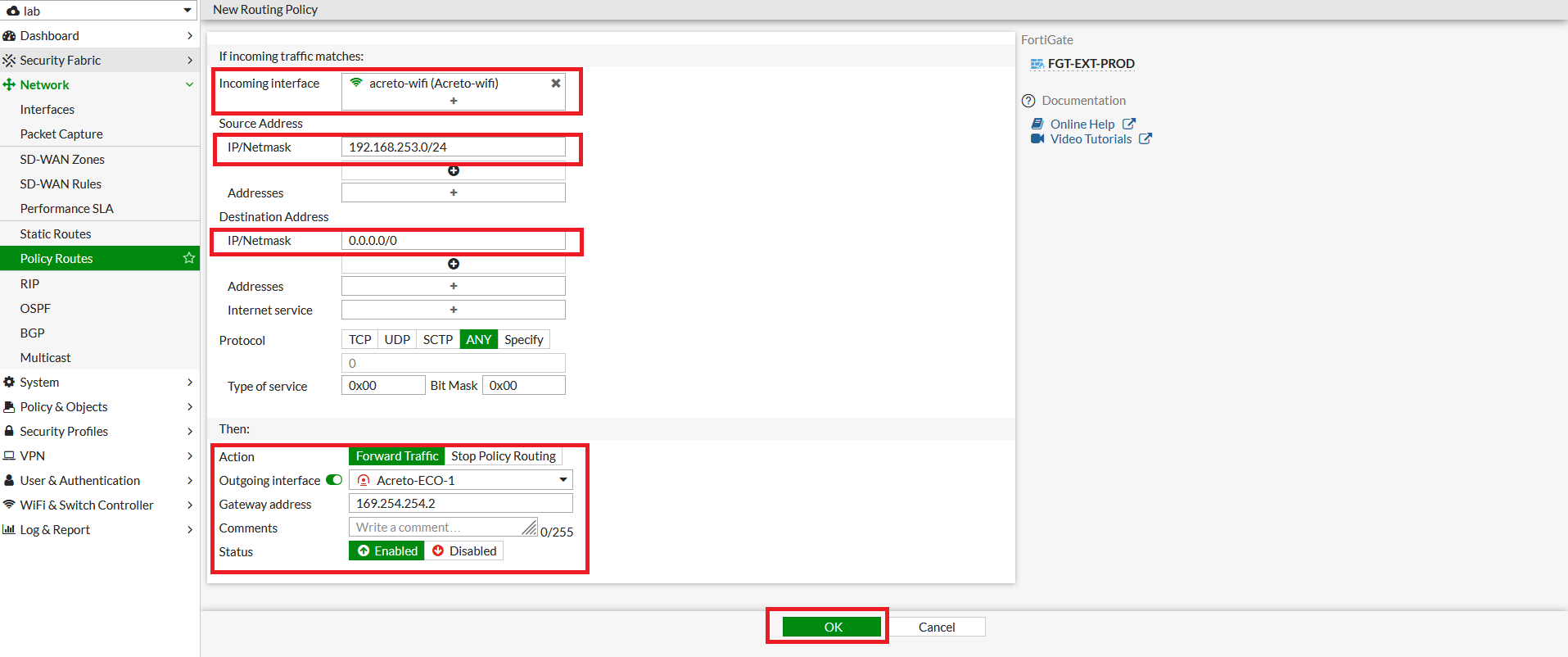
- In the next window, configure policy route setting as below:
- Incoming Interface: Select LAN interface
- Source - IP/Netmask: 192.168.253.0/24 (LAN Network)
- Destination - IP/Netmask: 0.0.0.0/0
- Outgoing Interface: Acreto-ECO-1 (Primary Tunnel)
- Gateway Address: 169.254.254.2 (Remote IP for primary tunnel interface)
- Click on save.

- Repeat the step to configure the policy route for the secondary tunnel.
- Go to Network > Policy Route. Click on Create New.
- In the next window, configure policy route setting as below:
- Incoming Interface: Select LAN interface
- Source - IP/Netmask: 192.168.253.0/24 (LAN Network)
- Destination - IP/Netmask: 0.0.0.0/0
- Outgoing Interface: Acreto-ECO-2 (secondary Tunnel)
- Gateway Address: 169.254.254.4 (Remote IP for secondary tunnel interface)
- Click on Save.

Task 7. Configure Firewall Policies to Allow the Traffic.
- Go to Policy & Objects > Firewall Policy. Click on Create New.
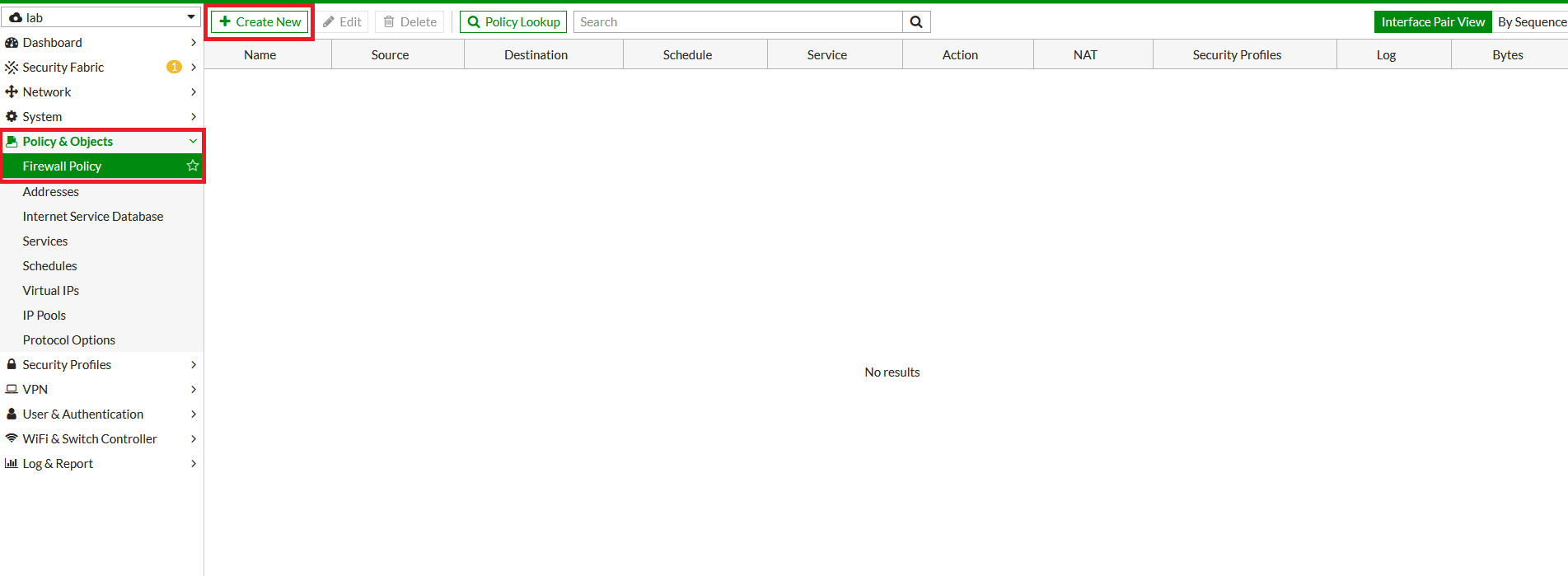

- In the next window, configure the policy setting as below for primary VPN.
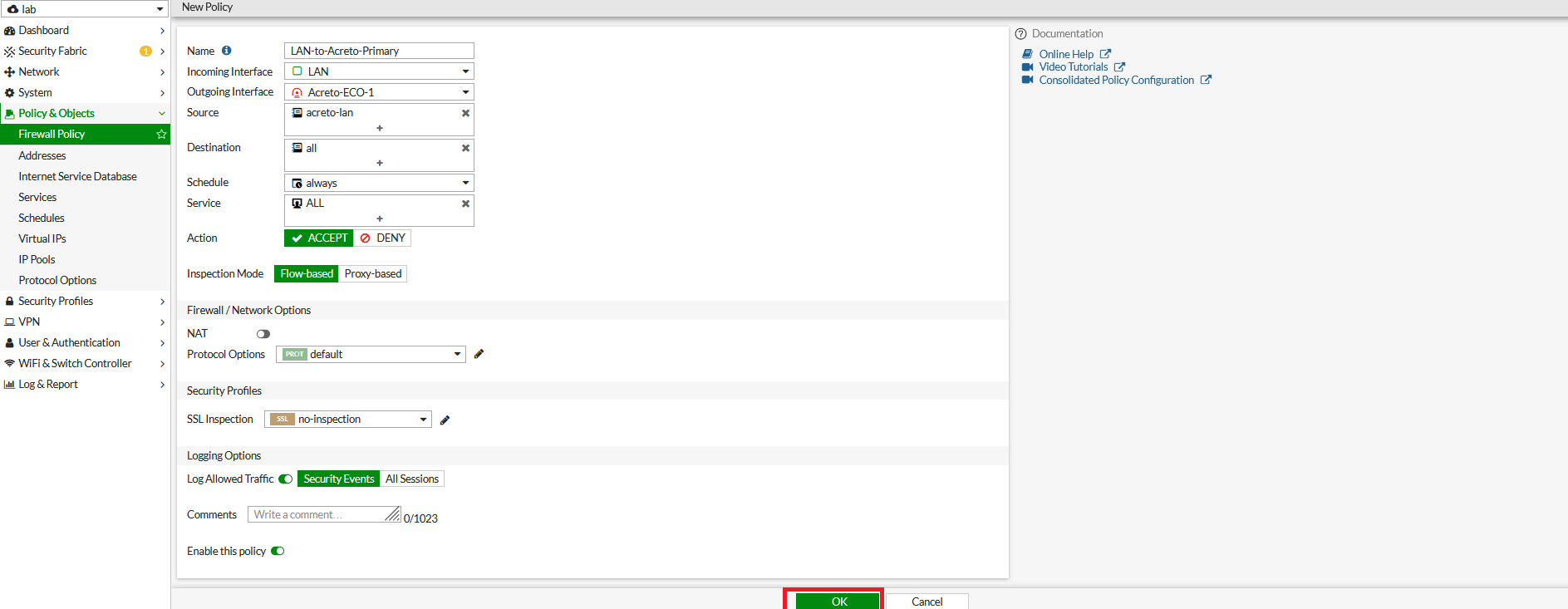
- Name: Give a name to the primary policy
- Incoming Interface: LAN
- Outgoing Interface: Acreto-ECO-1 (Primary Tunnel Interface)
- Source: LAN Address
- Destination: all
- Schedule: Always
- Service: All
- Action: Accept
- NAT: Disable
- Protocol Option: default
- SSL Inspection: no-inspection
- Logging: As needed
- Click on Save.

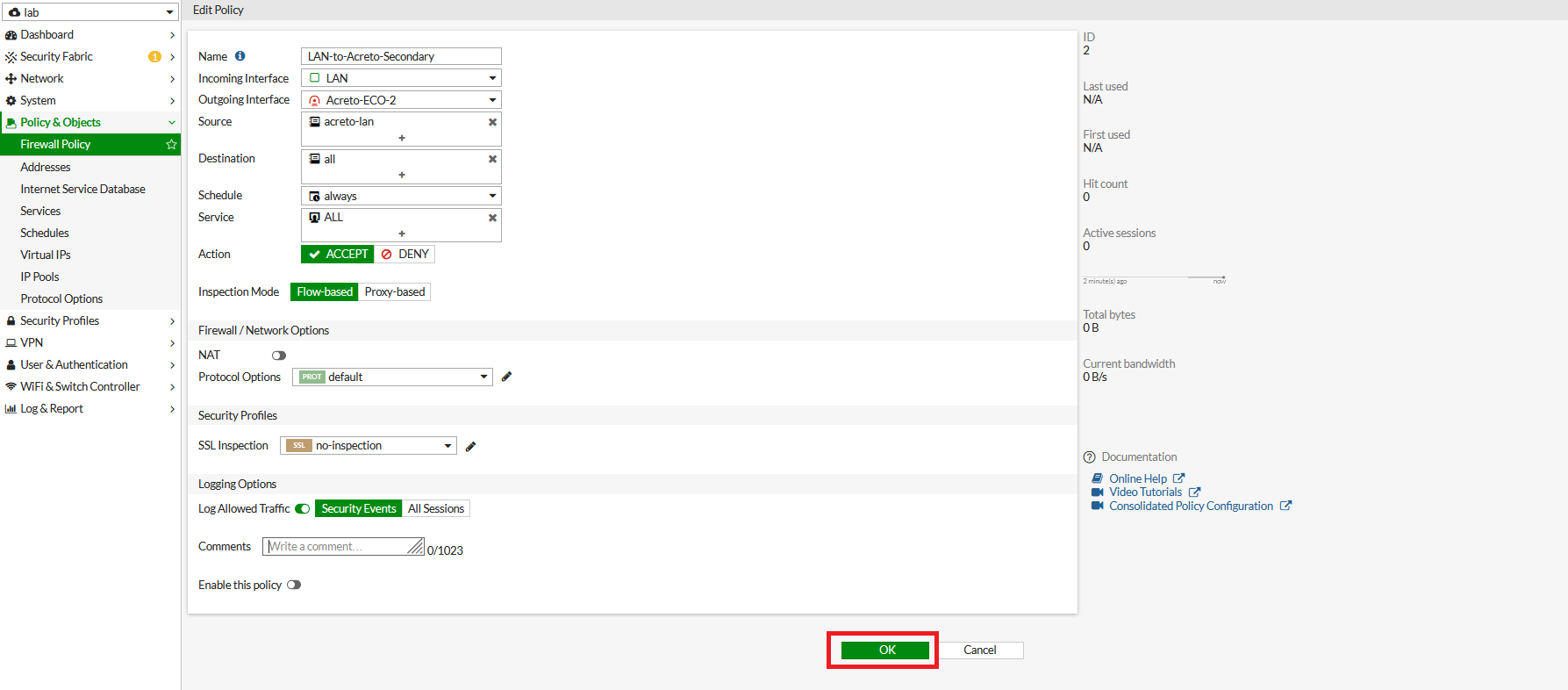
- Repeat the step to create a firewall policy to allow traffic on secondary VPN.
- Go to Policy & Objects > Firewall Policy. Click on Create New.
- Name: Give a name to the secondary policy
- Incoming Interface: LAN
- Outgoing Interface: Acreto-ECO-2 (Secondary Tunnel Interface)
- Source: LAN Address
- Destination: all
- Schedule: Always
- Service: All
- Action: Accept
- NAT: Disable
- Protocol Option: default
- SSL Inspection: no-inspection
- Logging: As needed
- Click on Save.

Task 8. Check the status of the VPN.
- Go to Dashboard > Network > IPsec.
- If the tunnel is showing down. Select the tunnel and click on Bring UP
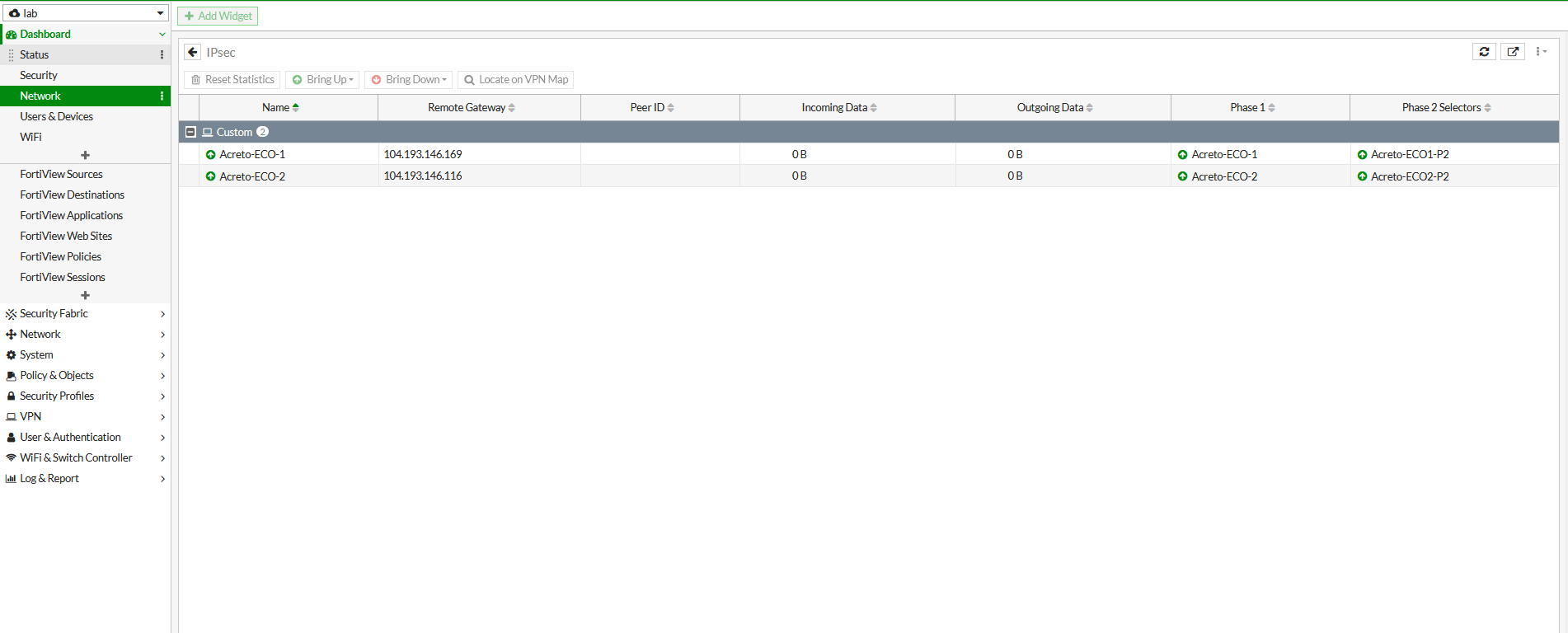

- Primary and secondary VPN selection is handled by Policy Route.
Traffic will be matched with the policy on top if both tunnels are up.

Summary
After this setup, there are two tunnels created from FortiGate to Acreto Primary and Secondary Ecosystem through Primary and Secondary tunnel respectively. If the primary tunnel goes down, all traffic will start going from the backup tunnel, which in this case is the Secondary tunnel.