MFA for Acreto Connect Client - User Guide
Before You Start
What is Multifactor Authentication, and why should you use it?
Two-Factor Authentication (2FA or MFA) - 2FA is an extra layer of security to ensure that people trying to access an online account are who they say they are. First, a user will enter their username and password. Then, instead of immediately gaining access, they must provide other information.
This article explains why you should enable MFA in Acreto.
Prerequisites
The Administrator of your Ecosystem should Enable the MFA for you.
To get the best User Experience with Acreto MFA, you need to download and install Acreto Connect Client
How To
Step 1: Start the Onboarding Procedure
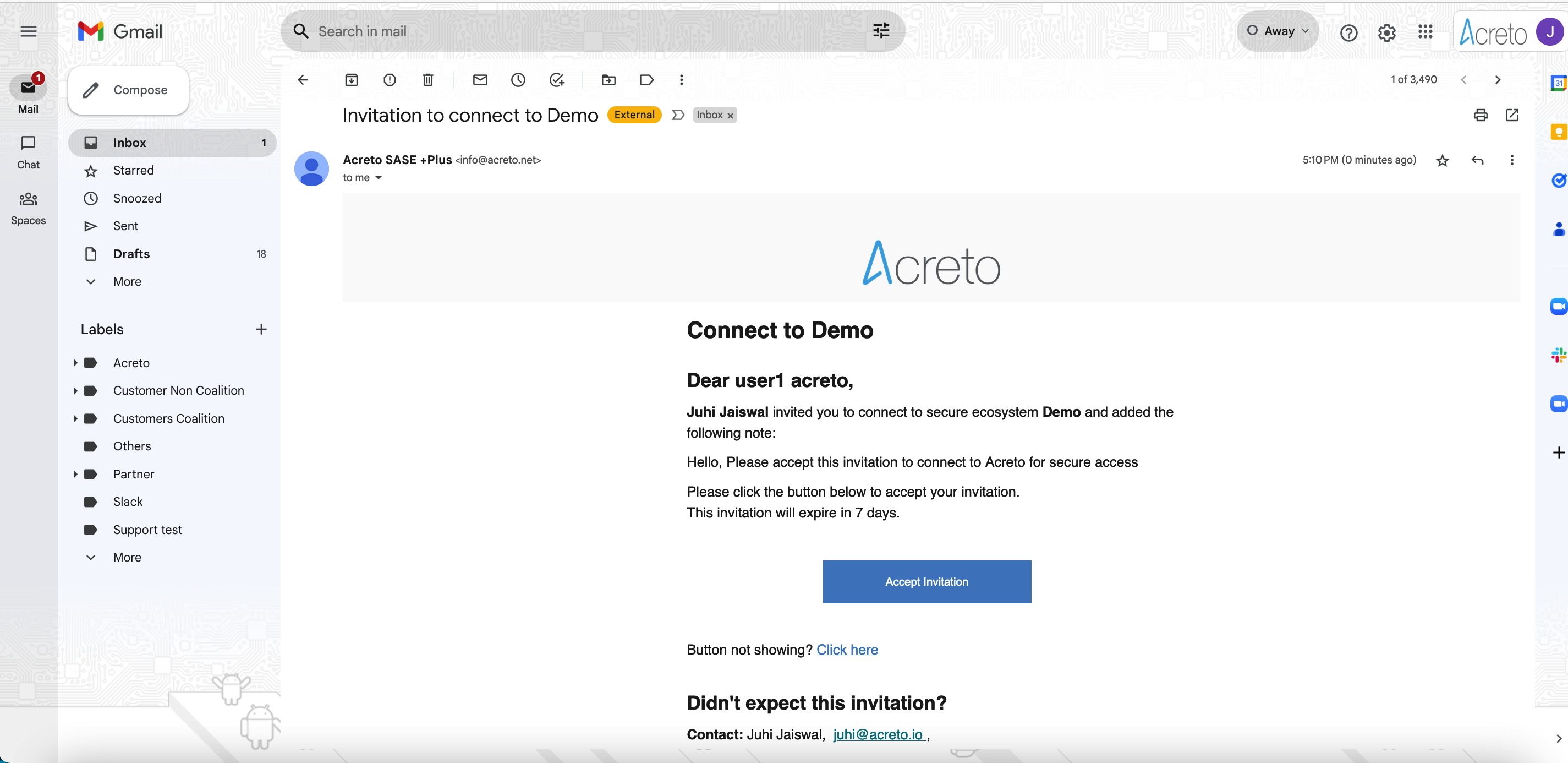
If MFA is enabled in your Ecosystem, you should receive an Invitation email that allows you to set up the MFA for your account.
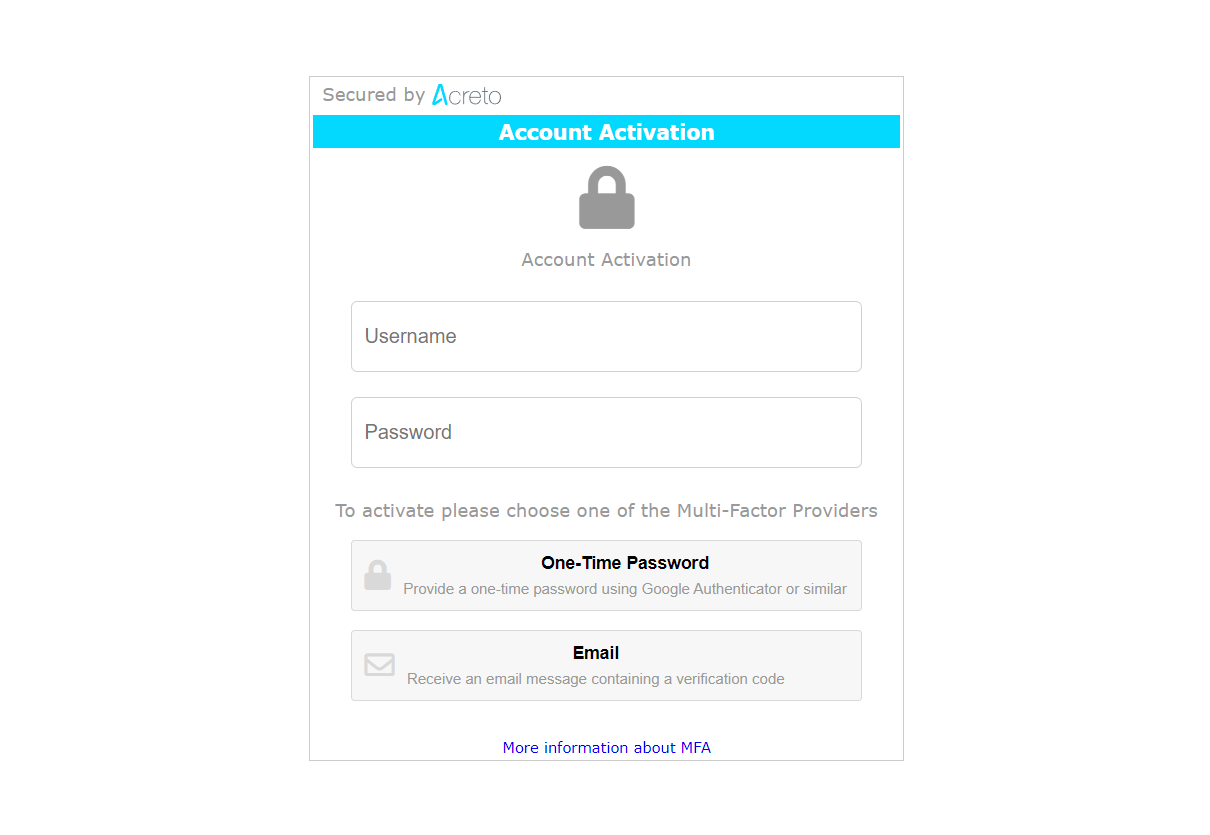
Click the Button Accept Invitation to start the onboarding process. Next, you see an MFA setup page - provide your username and password registered on Identity Provider ( Generic LDAP, Azure Active Directory, Windows Server AD, Google Workspace, etc.) and select one of the Multi-Factor Providers to register their Multi-factor device.
On this screen, you may also choose the second-factor method: Email or Authentication Application - more details about them in next the step.
Step 2: Choose the Second Factor
There are two ways of receiving the second factor of authentication - Email and Authentication Application.
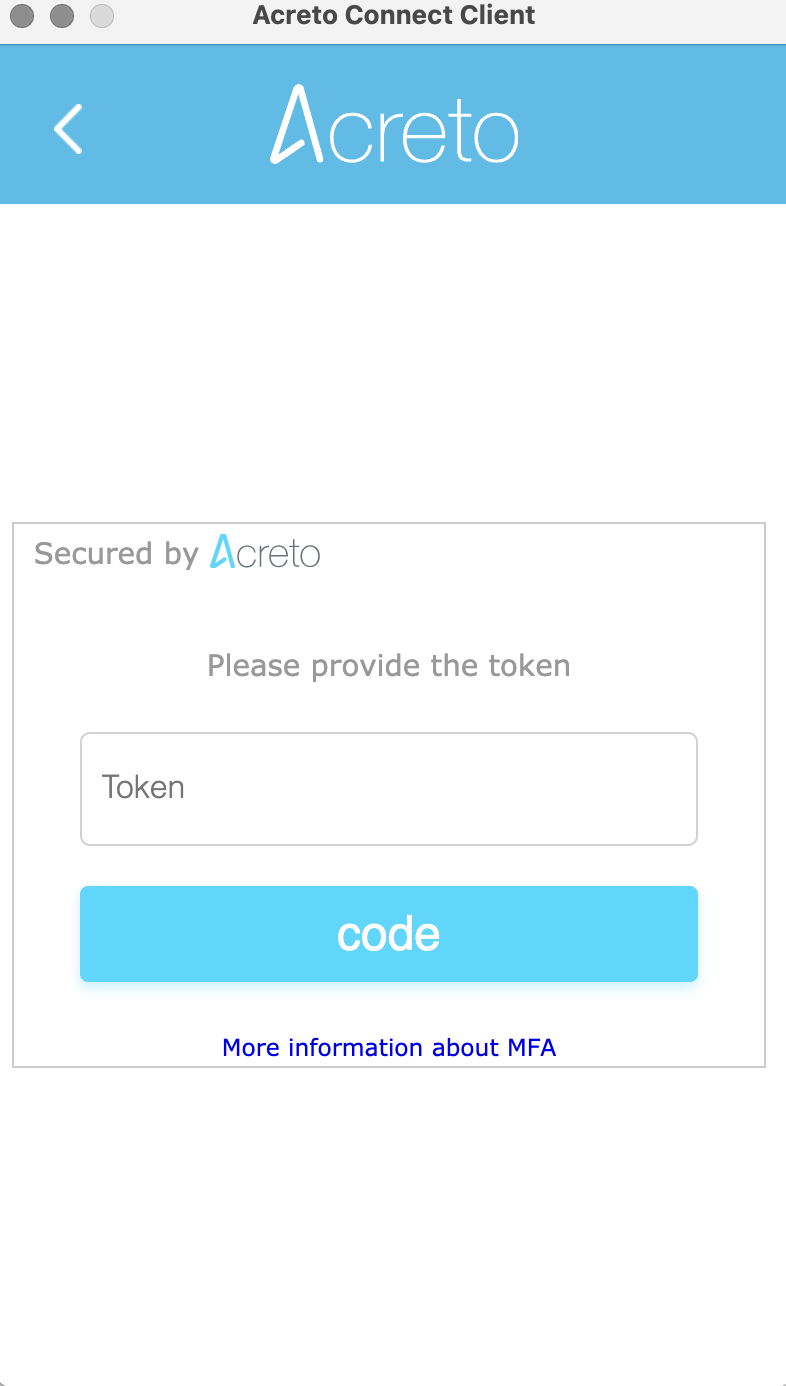
- If you choose Email as the Multi-factor provider, you receive the auth code as an email message whenever you try to log in.
- Provide the token received on the email on the Acreto auth page.
- Whenever the token expires(generally 24 hours), Acreto will prompt for reconnection, and the user will have to provide the username/password and new token sent via email to reconnect.
- Proceed to the next step for finishing the Onboarding process to Acreto VPN.
One-Time Password
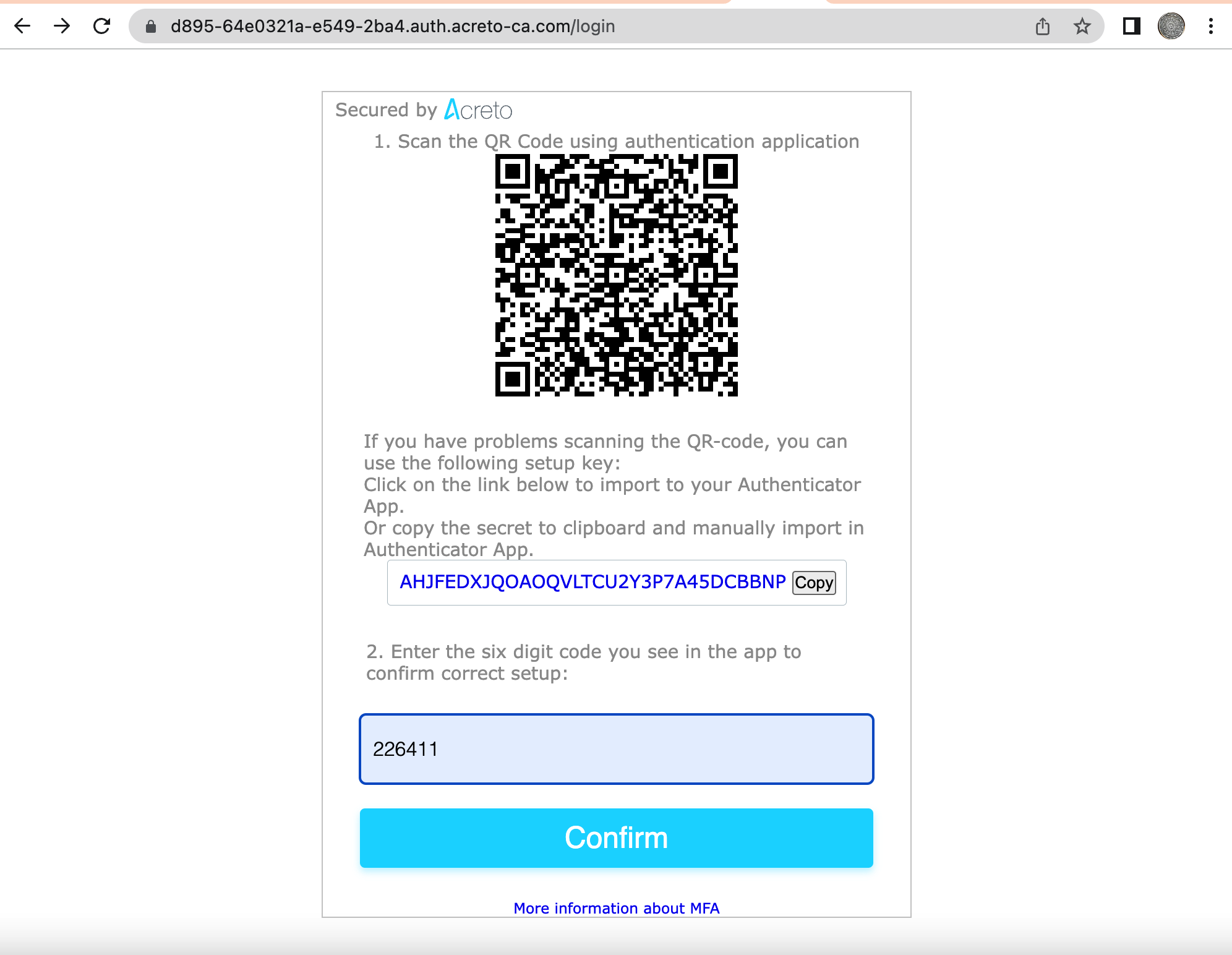
- If you choose One-Time Password as the Multi-factor provider, you need to scan the QR code screen to register the authenticating device which can receive the token.
- Download Google Authenticator or an equivalent app from the App Store on your mobile device.
- Scan the QR code on the Acreto page to add the account on the Authenticator app.
- The Authenticator app will generate the token after adding the account. Use the token on the Authenticator app and provide it on the token box on the Acreto page.
- Whenever the token expires(generally 24 hours), Acreto will prompt for reconnection, and the user will have to provide the username/password and token generated on the Authenticator app to reconnect.
- PProceed to the next step for finishing the Onboarding process to Acreto VPN.

Step 3: Complete the onboarding process
- After successful authentication, the user will be provided the link to download the VPN configuration.
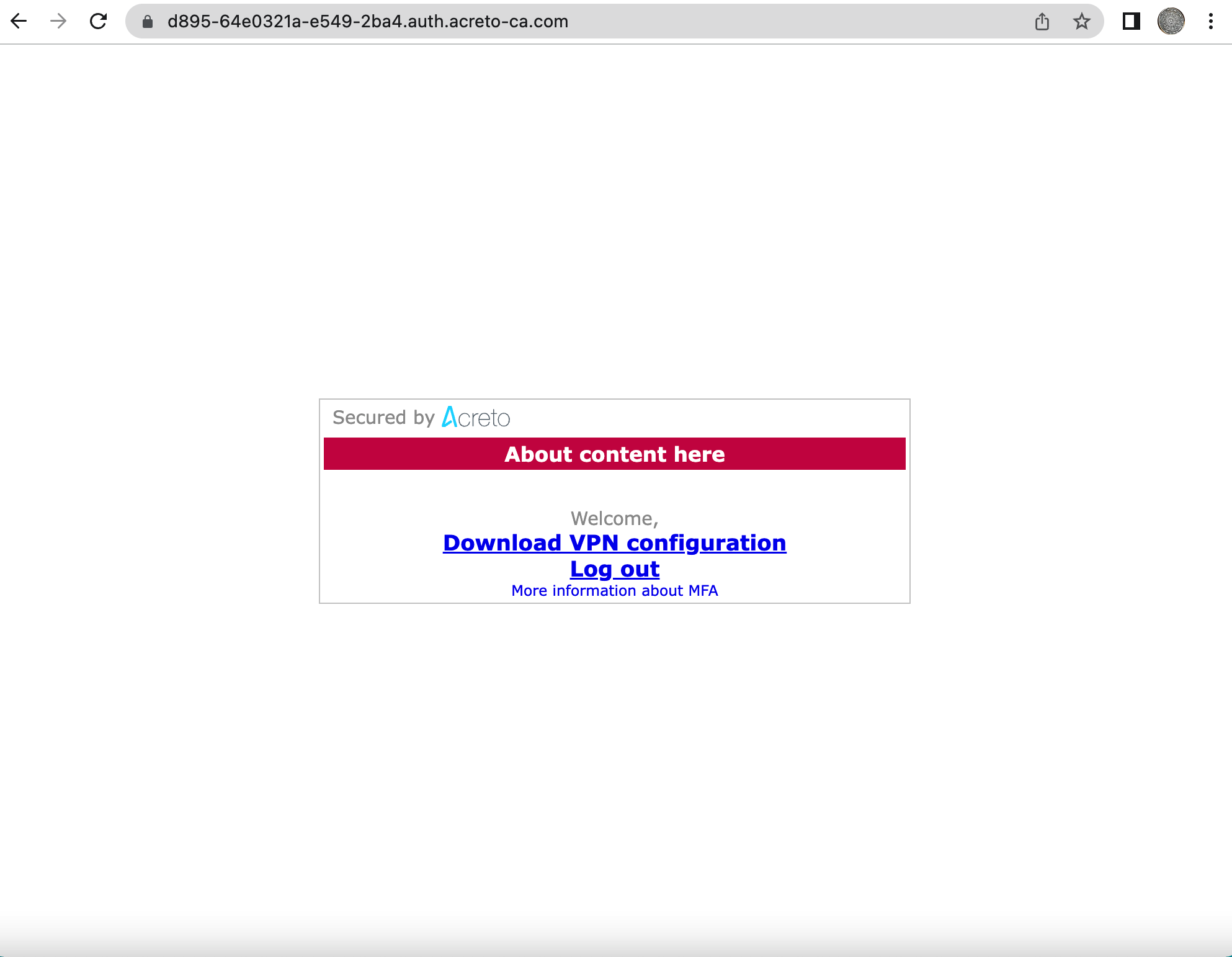

- Click the link to download the VPN configuration.
- Import the downloaded VPN configuration on the Acreto Connect Client
- Upon successful import, the Acreto VPN will be auto-connected.
- Verify your connection by checking Acreto’s ISP.
ACC Connection
From now on, periodically (usually once for 24h), Acreto Connect Client will ask you about the second factor.
You must provide the token to keep the connection or establish a new one. Acreto Connect CLient will inform you about the need to authenticate with the proper window.
Summary
In an increasingly interconnected and threat-prone digital landscape, Multi-Factor Authentication has emerged as a “must-have” feature for organizations and individuals. By mitigating password vulnerabilities, enhancing security, complying with regulations, and offering user convenience, MFA significantly strengthens access control and protects against unauthorized access and data breaches. Implementing MFA is a proactive step towards bolstering overall cybersecurity posture and safeguarding sensitive information.