Connect to multiple VPCs in AWS using Transit Gateway
Before You Start
Overview
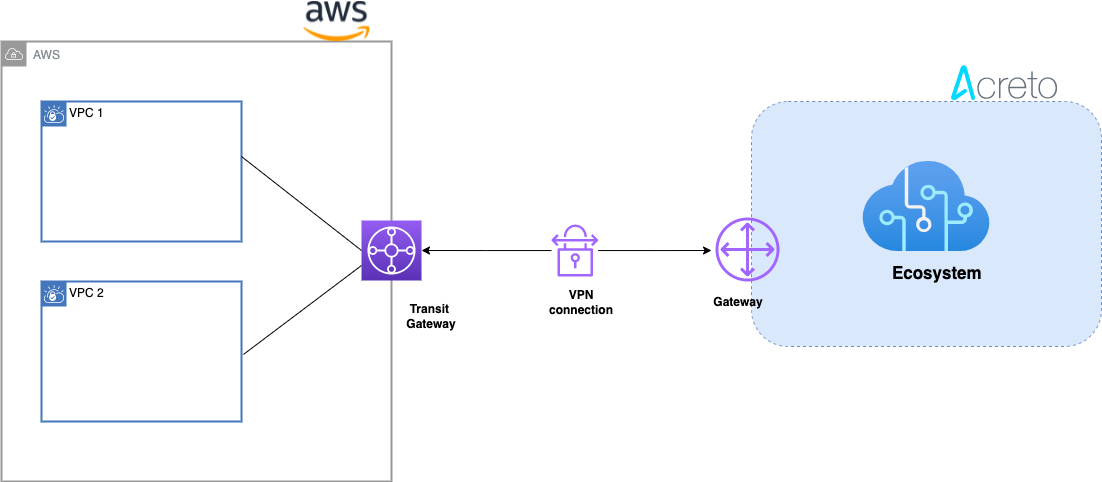
This article describes configuring a Route-Based Site-to-Site IPsec VPN between an Acreto Ecosystem and the Amazon Web Services (AWS) Transit Gateway to access multiple VPCs.
Network Diagram
Concepts and Glossary
- IPsec VPN tunnel: An encrypted link where network traffic can pass between Acreto Ecosystem and AWS VPS.
- Customer gateway: An AWS resource that provides information to AWS about the Acreto IPsec Gateway object.
- Virtual private gateway: The VPN concentrator on the Amazon side of the Site-to-Site VPN connection.
Prerequisites
To setup an IPsec Site-to-Site VPN tunnel between Acreto Ecosystem and AWS VPS, you need:
- Access to Active Acreto Ecosystem
- Access to AWS Management Console
- Pre-configured VPC, subnets, route tables, NACL, and security groups
The Purpose of Site-to-Site IPsec VPN
Acreto, as a Cloud Provider, allows to connect and integrate multiple physical and virtual networks. All connections require stable and secure links. Virtual (EC2) Instances running on Amazon VPC can’t communicate securely with your own (remote) network by default. However, it is possible to connect your network to Acreto Ecosystem. Then, you can enable access to your remote network from your VPC by creating an AWS Site-to-Site VPN (Site-to-Site VPN) connection and configuring routing to pass traffic through the connection.
Acreto Ecosystem configures the routing automatically and passes the traffic between AWS VPC and your network. Additionally, the traffic is scanned by the Acreto Threat Engine to block suspicious traffic and malware.
How To
Configure Site-to-Site VPN in AWS
Use the following procedures to manually set up the AWS Site-to-Site VPN connection transit gateway on Amazon AWS.
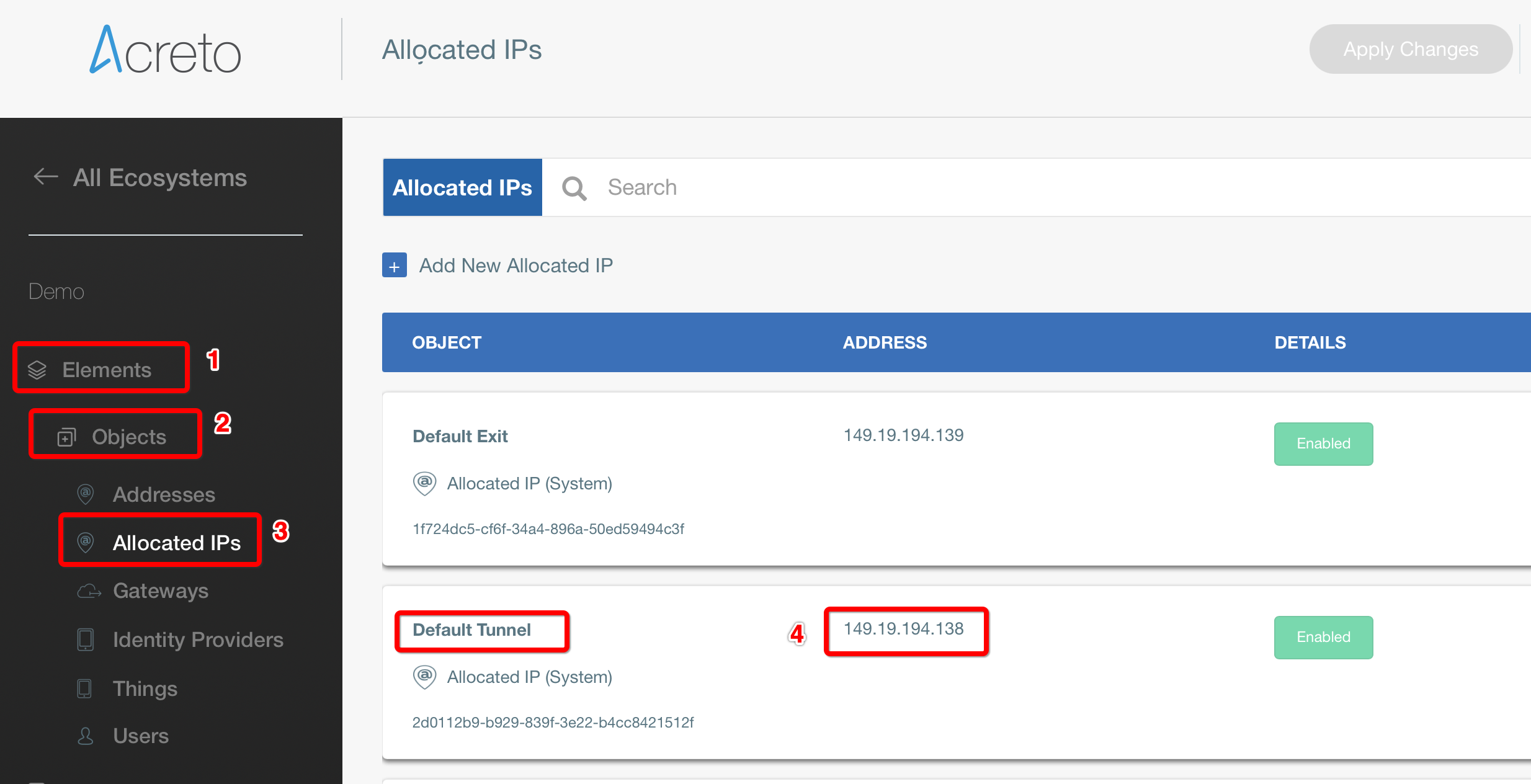
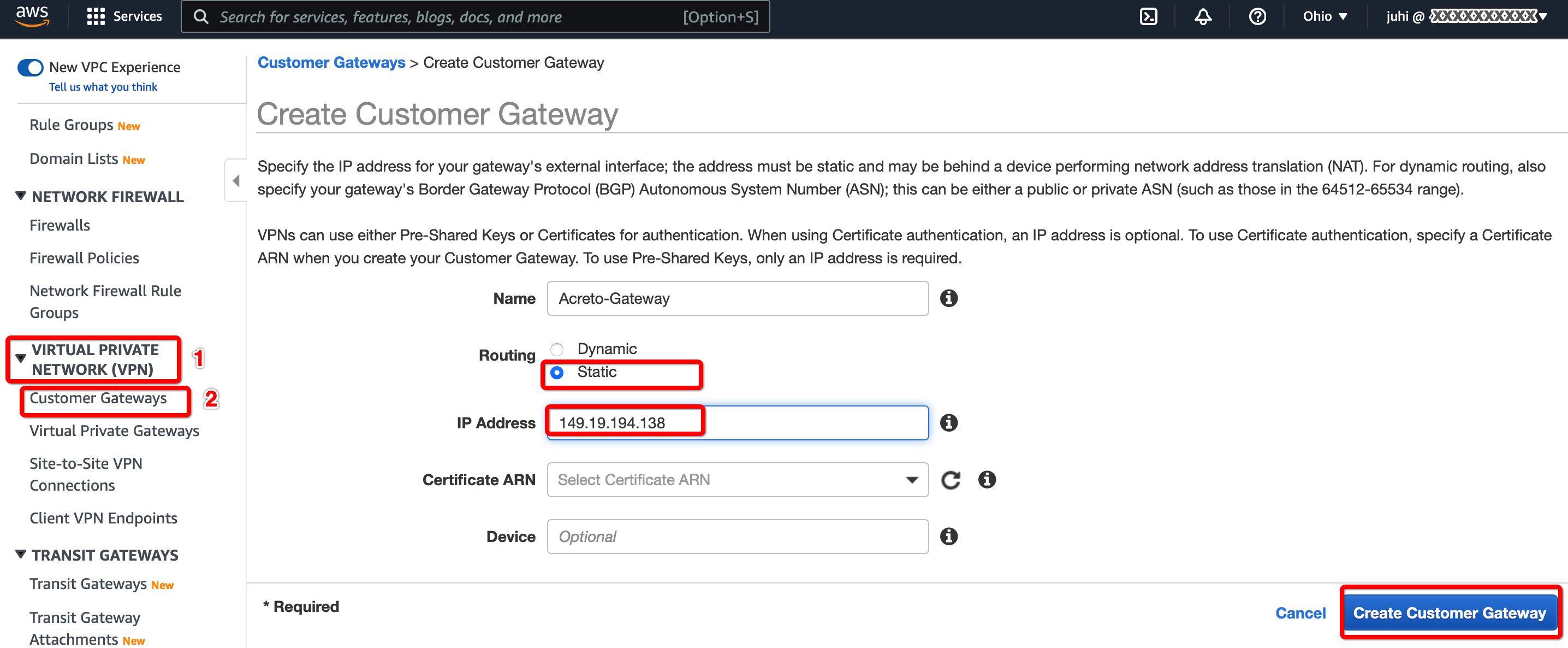
Step 1.1: Create Customer Gateway
Create a new Customer Gateway with Acreto’s public IP.
-
From the VPC Dashboard in the left sidebar, go to VIRTUAL PRIVATE NETWORK (VPN) » Customer Gateways
-
Click Create Customer Gateway
-
Provide the following values :
- Name: Acreto
- Routing: Static
- IP Address: Acreto’s Default Tunnel IP
-
Click Create Customer Gateway.
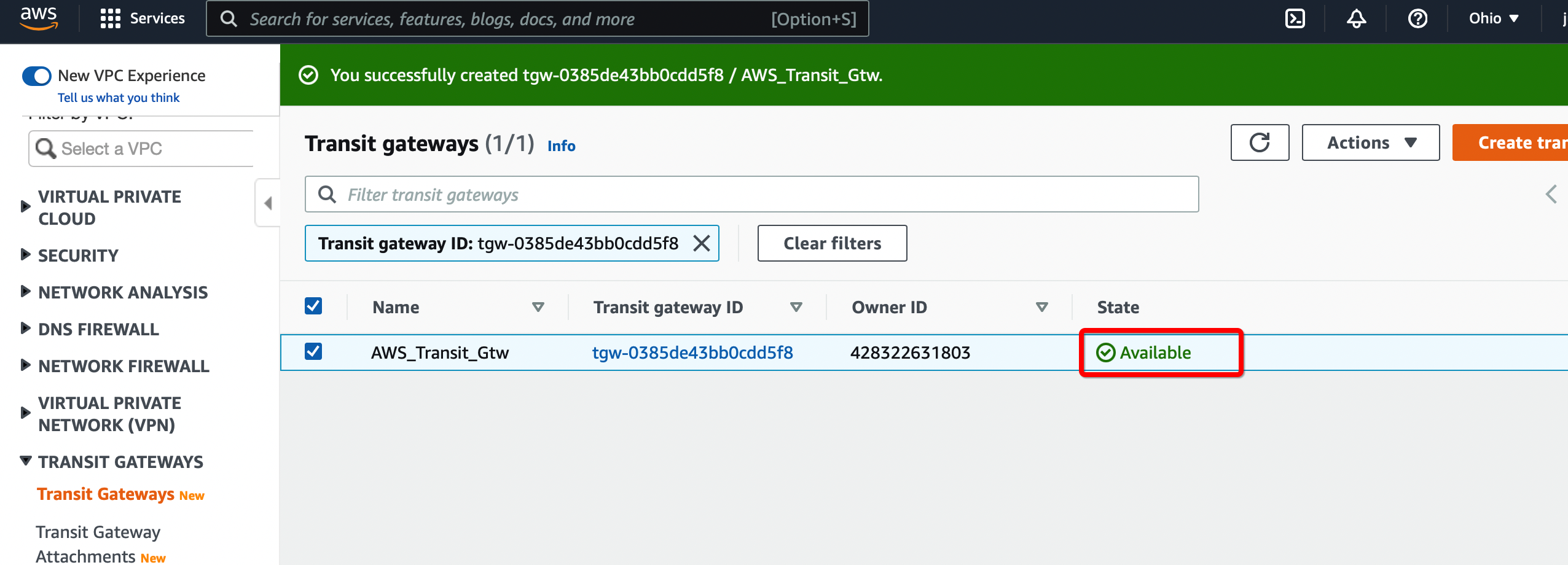
Step 1.2: Create Transit Gateway
Create a Transit gateway that will be used to form the IPsec tunnel with Acreto.
-
From the VPC Dashboard in the left sidebar, go to TRANSIT GATEWAYS » Transit Gateways.
-
Click Create Transit Gateway.
-
Give the name and click Create Transit Gateway
-
Wait for a few minutes to get the state of Transit Gateway to Available.
Step 1.3: Create Transit Gateway attachment
Create a Transit gateway attachment that will attach to the primary VPC.
-
From the VPC Dashboard in the left sidebar, go to TRANSIT GATEWAYS » Transit Gateways Attachment
-
Click Create Transit Gateway Attachment
-
Provide the following values
- Transit Gateway ID - Select the Transit gateway created in the previous step
- Attachment type - VPC
- VPC ID - Select the VPC
- Subnet IDs - Select the subnets that will communicate over the VPN
-
Click Create Transit Gateway attachment
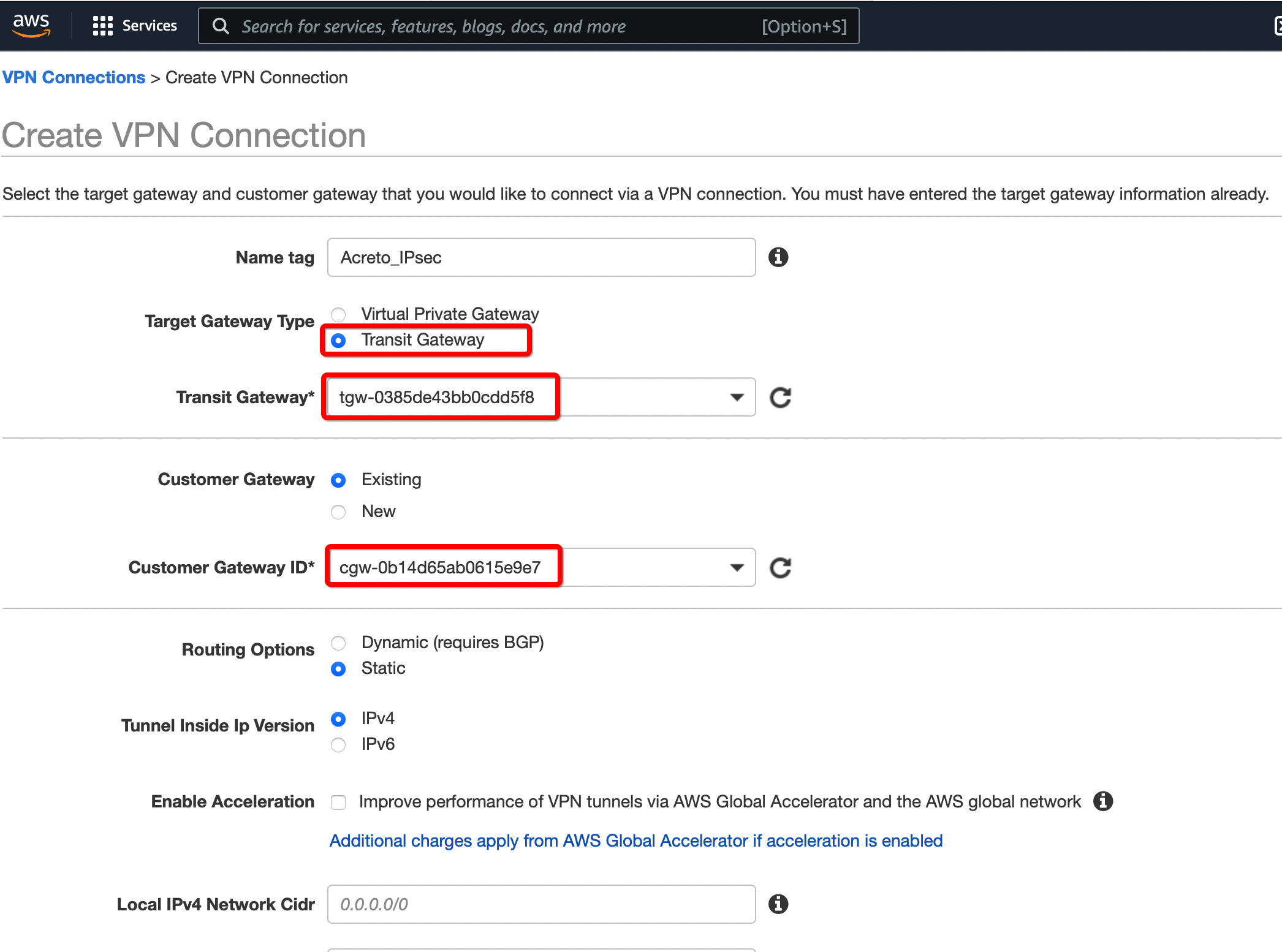
Step 1.4: Create and Configure VPN Connection
Create a new VPN connection and associate the previously created Virtual Gateway in Step 2 and Customer Gateway in Step 1.
-
From the VPC Dashboard in the left sidebar, go to VIRTUAL PRIVATE NETWORK (VPN) » Site-to-Site VPN Connections.
-
Click Create VPN Connection.
-
Provide the following values in the tunnel setting:
- Name: Acreto_ipsec
- Target Gateway Type: Transit Gateway
- Transit Gateway: Select the Transit gateway created Step 6
- Customer Gateway: Existing
- Customer Gateway ID: Select the Customer gateway created in Step 5
- Routing Options: Static
- Static IP Prefixes: 100.64.0.0/16
-
Click Create VPN Connection.
-
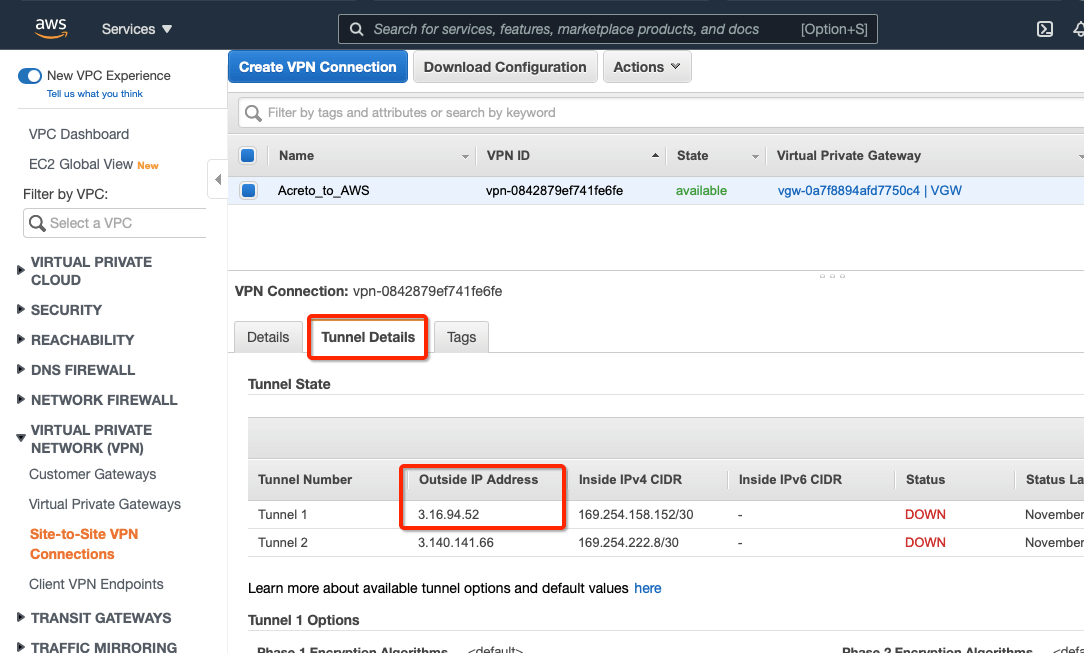
Select the VPN created and click the tab Tunnel Details. Copy the Outside IP address of the tunnel to form a VPN with Acreto.
This Outside IP address will be used in the next steps to configure the Acreto gateway on Wedge Ecosystem.
Step 1.5: Create Acreto Gateway for IPsec
Create Gateway on Ecosystem by following the instructions in the link. Provide the following values:
- Type: IPsec
- Category: Data Center
- Model: AWS site-to-site VPN
- Connections from: AWS Tunnel’s Outside IP address
- Local network: local_network
- Save and Commit the changes.
Step 1.6: Read the Configuration
-
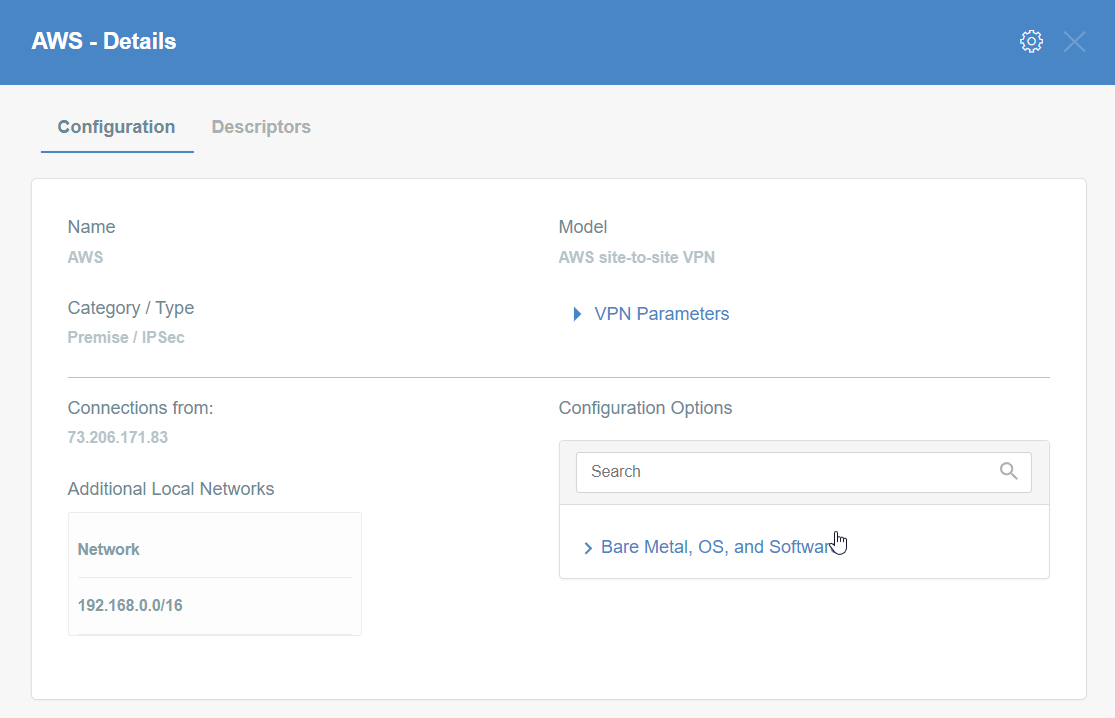
Click the gateway created on the Wedge.
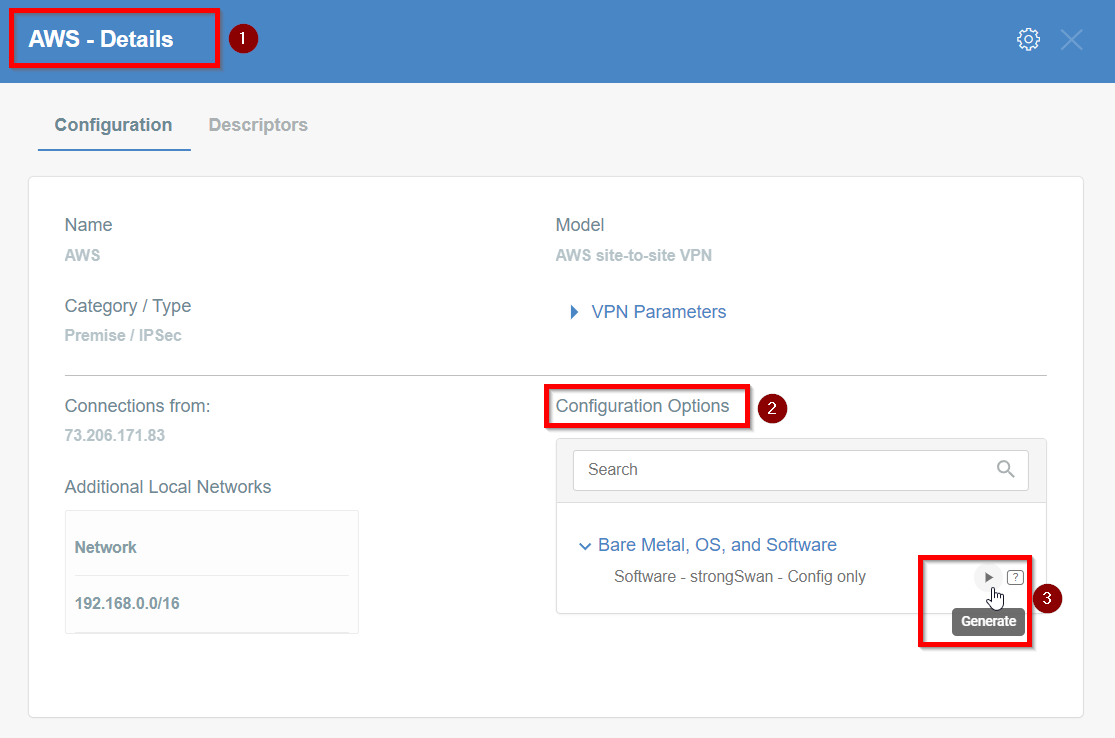
-
Click the Play button under Configuration Options to generate the strongSwan Config.
-
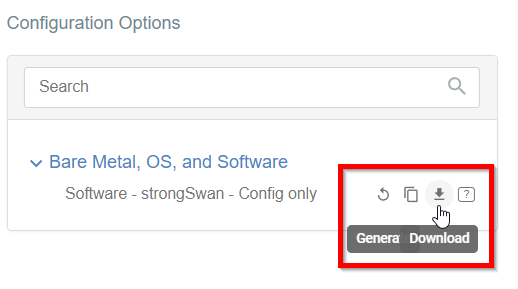
Once the Config file is generated, click the Download button to download the configuration on the local computer.
-
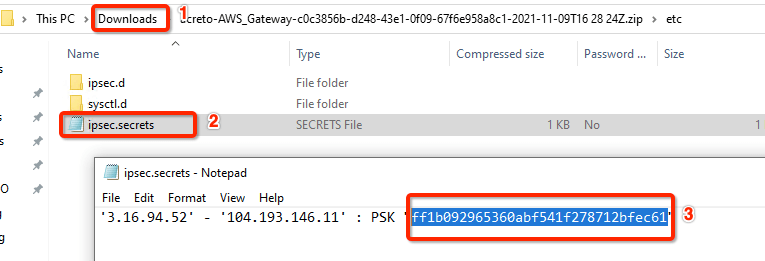
Unzip the downloaded file and copy the PSK from the file ipsec.secrets
Step 1.7: Update AWS VPN tunnel configuration
-
Goto AWS Site-to-Site VPN connections
-
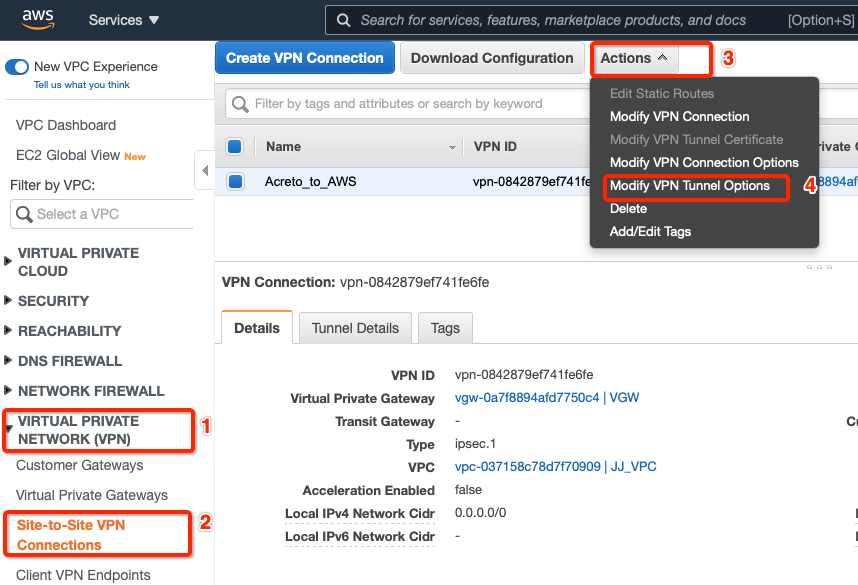
Select the VPN and click Actions » Modify VPN Tunnel Option
-
Select the tunnel used to create the VPN with Acreto.
-
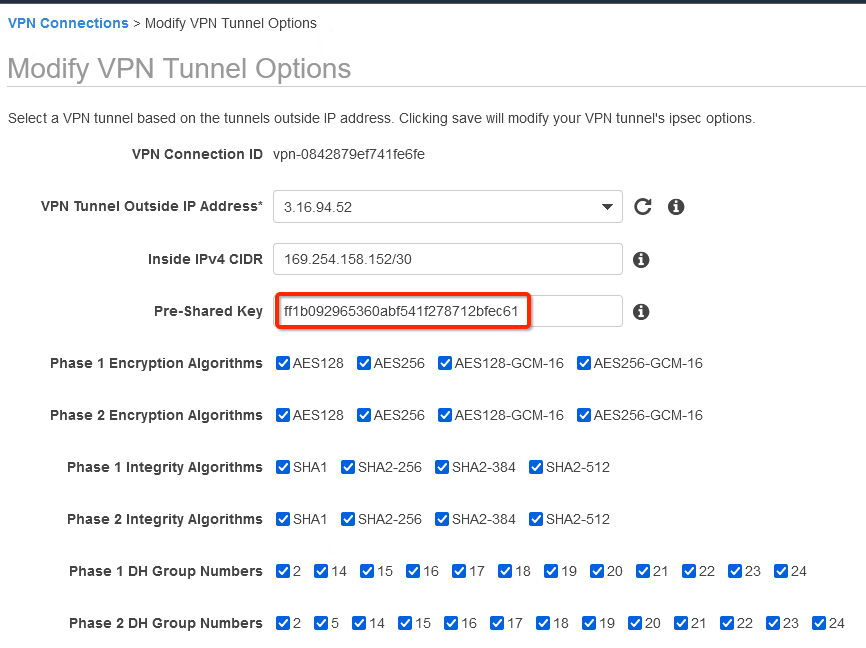
Update the password copied from the ipsec.secrets file from strongSwan config file downloaded from Wedge
-
In the same window “Modify VPN Tunnel Options” scroll down and select the following action under tunnel configuration:
- DPD Timeout Action: Restart
- Startup Action: Start
-
Click Save
Step 1.8: Update the Transit Gateway Route Table
Configure the Route table to set the default route to the VPN tunnel.
-
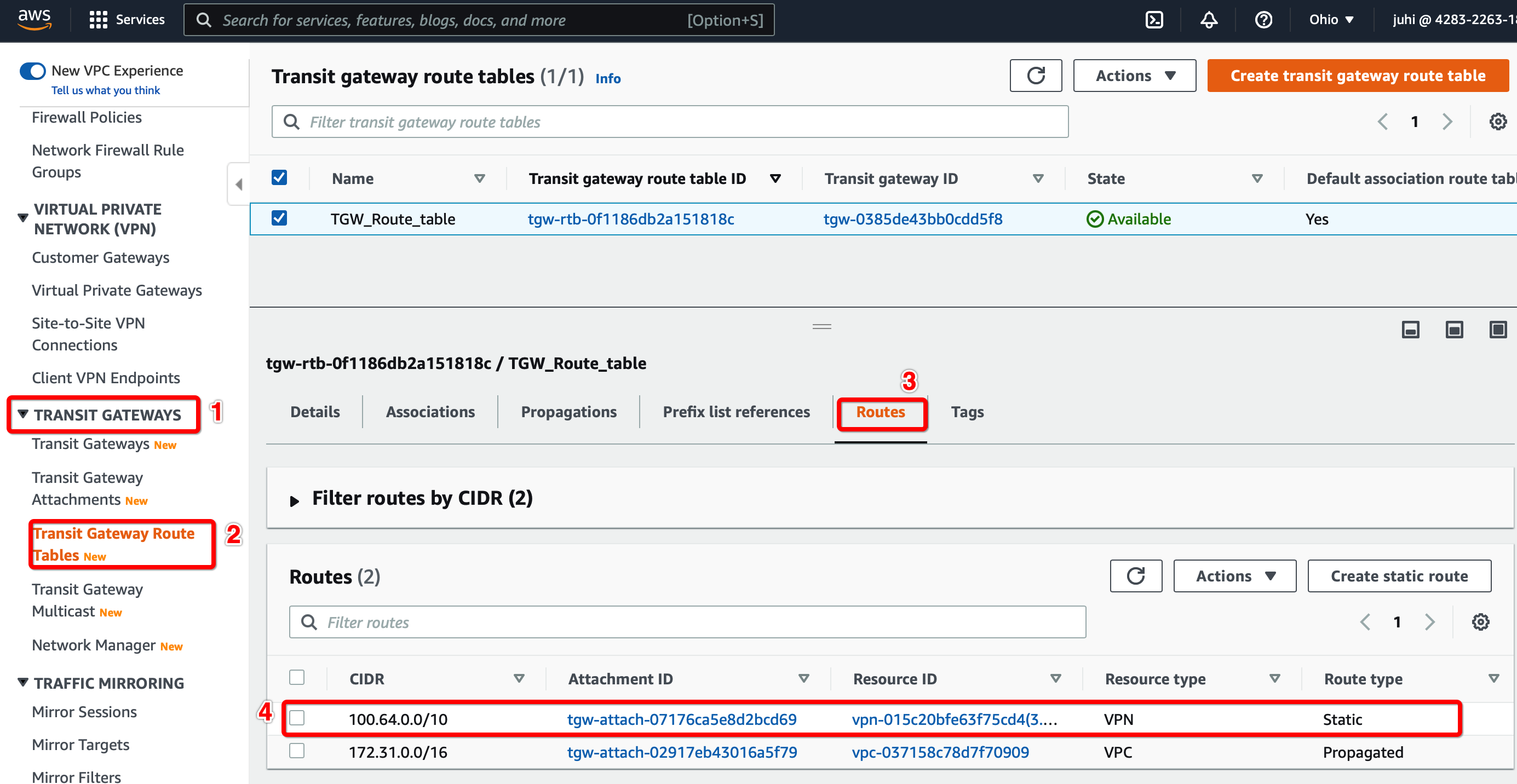
From the VPC Dashboard, click Transit Gateway Route Table under TRANSIT GATEWAYS in the left sidebar
-
Select the Transit gateway Route table entry.
-
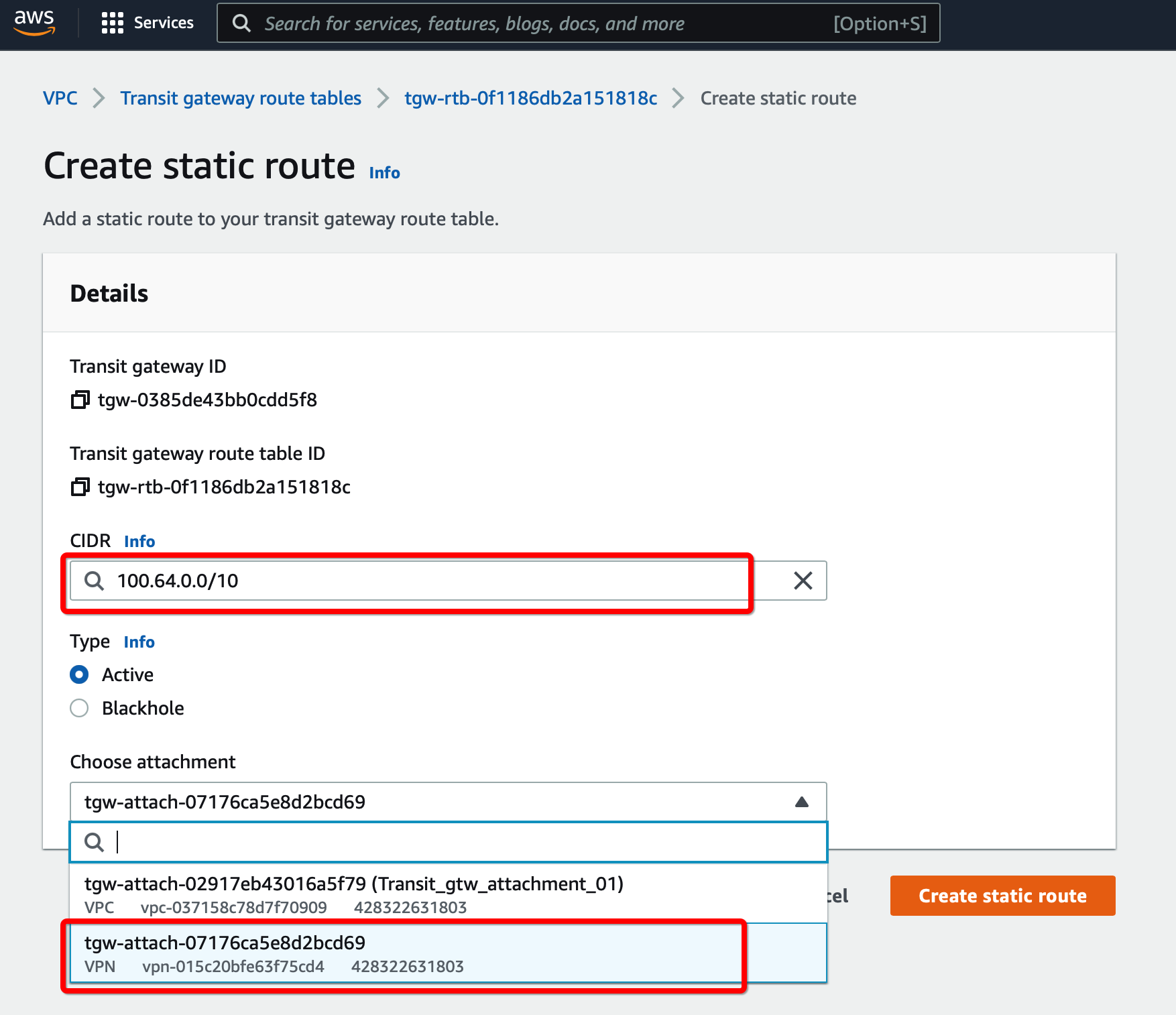
Select tab Routes and click Create Static Route
-
Click Create Static Route
Step 1.9: Update Route the Table for the Subnet
-
From the VPC Dashboard, click Route Tables under VIRTUAL PRIVATE CLOUD in the left sidebar
-
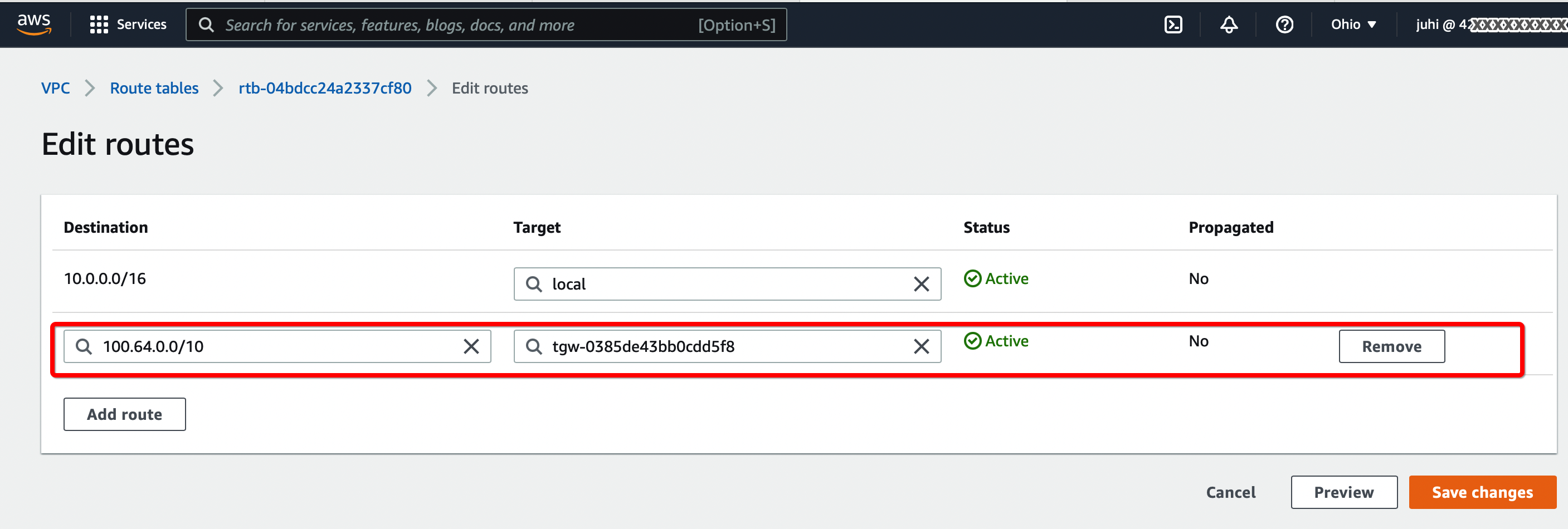
Select the Route table and click Edit routes. Add the following values :
- CIDR - 100.64.0.0/16
- Attachment - Select the Transit VPN attachment id
-
Click Save changes.
Attach Secondary VPC in the same account to the Transit Gateway
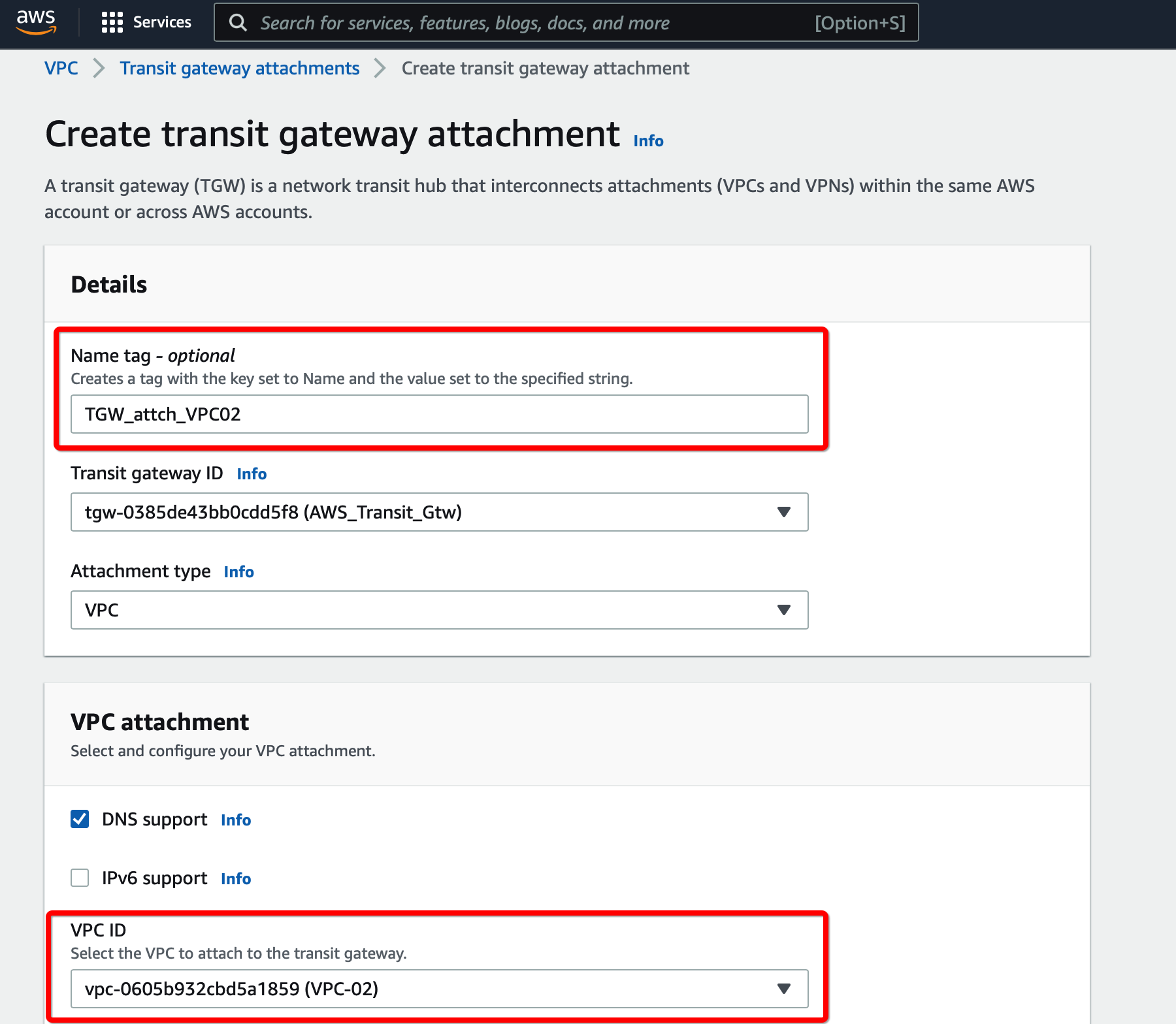
Step 2.1: Create Transit Gateway attachment for Secondary VPC
to TRANSIT GATEWAYS » Transit Gateways Attachment
-
Click Create Transit Gateway Attachment
-
Provide the following values
- Transit Gateway ID - Select the Transit gateway created in step 6
- Attachment type - VPC
- VPC ID - Select the new VPC
- Subnet IDs - Select the subnets that will communicate over the VPN
-
Click Create Transit Gateway attachment
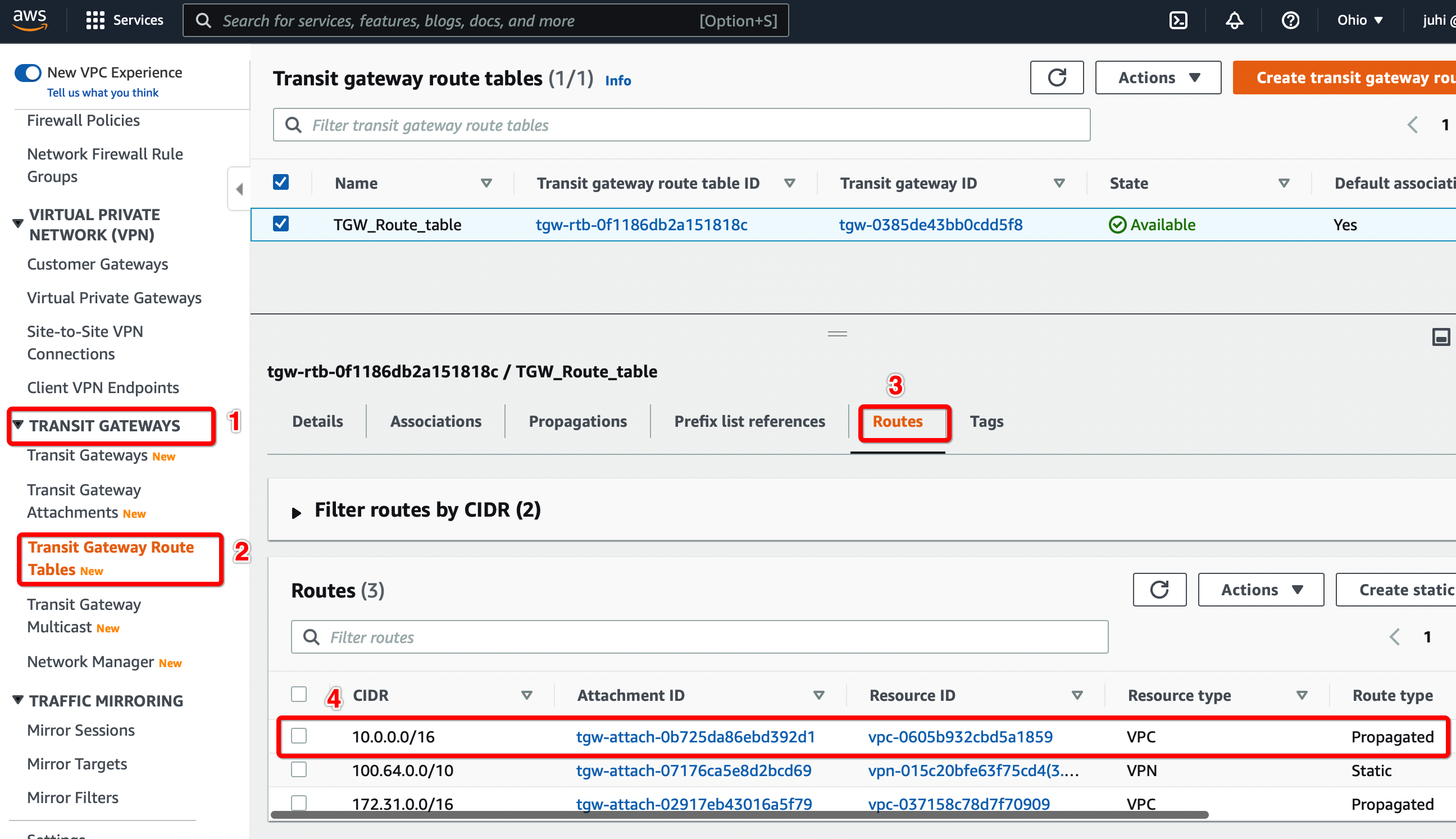
Step 2.2: Verify the routes from the new VPC Transit Gateway attachment is available on the Transit Gateway Route table.
Configure Routes from the new VPC transit gateway attachment appears in the Transit Gateway Route table.
-
From the VPC Dashboard, click Transit Gateway Route Table under TRANSIT GATEWAYS in the left sidebar
-
Select the Transit gateway Route table entry.
-
Select tab Routes
-
Check the Static route from the new VPC Transit Gateway attachment is available
Step 2.3: Update the routes for the Subnet in Secondary VPC
Follow Step 1.9 to add the route for Acreto subnet 100.64.0.0/16 through the transit gateway.
Verify the connections
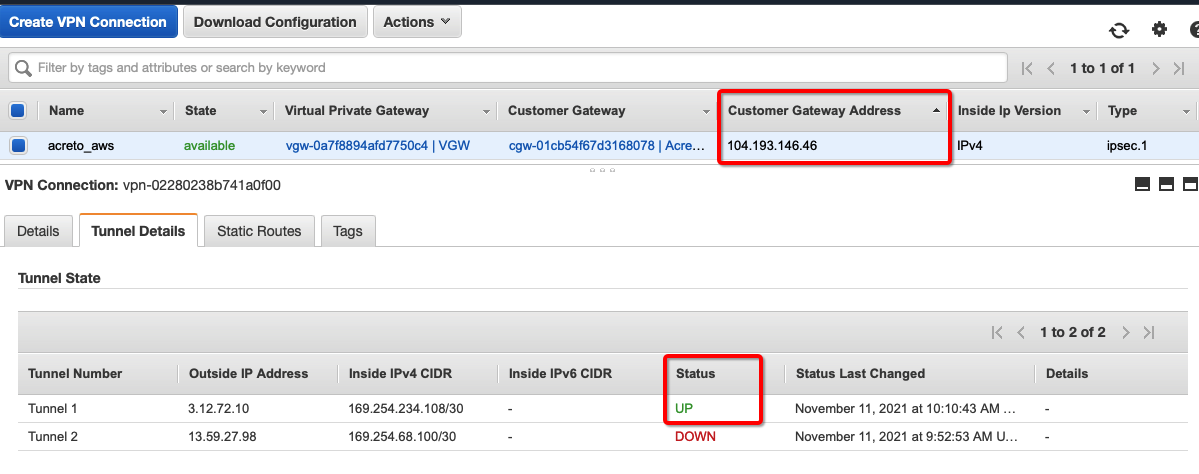
Once the tunnel connection is successfully established, the status of the connection will be up.
-
To verify on AWS, navigate to the VPN created under VIRTUAL PRIVATE NETWORK (VPN) » Site-to-Site VPN Connections. Verify the following:
- Customer Gateway: Acreto’s Default Tunnel IP
- Status: UP
-
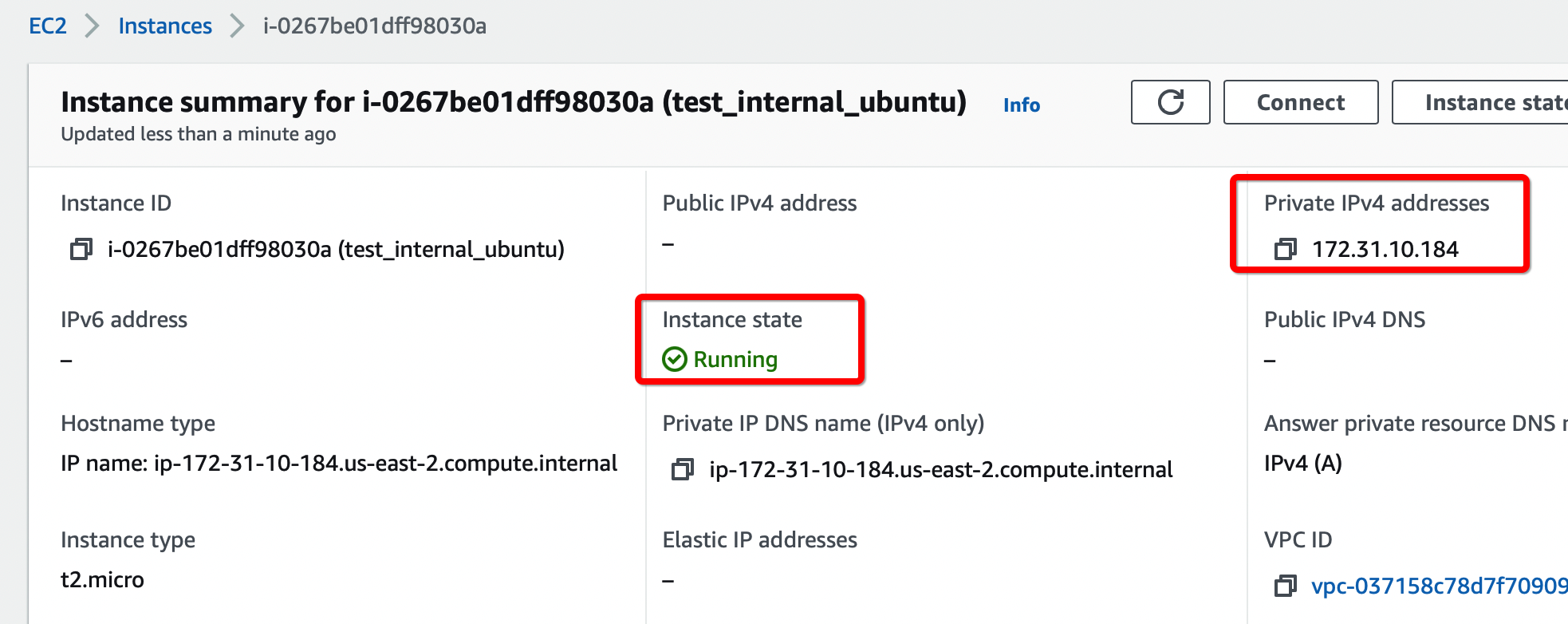
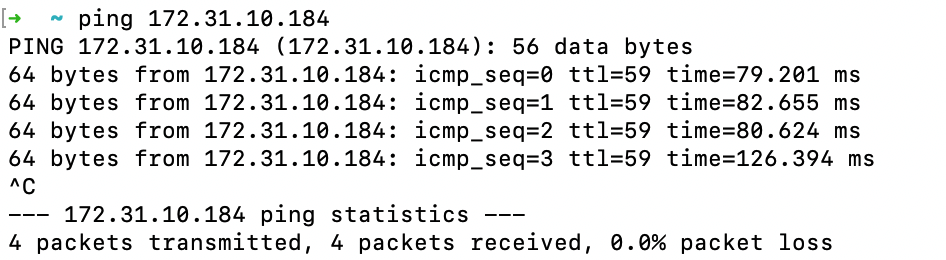
Connect a Remote user with the Acreto Connect Client and access the resources in the VPC connected using Transit Gateway.
References and Related Articles
Summary
Acreto Gateway allows setting up an IPsec VPN tunnel with AWS Transit Gateway, which can be used to access resources in multiple VPCs.