IPsec Ciphers List
Overview
In this article, you will get a full list of IPsec ciphers supported by Acreto platform.
Problem statement
When configuring IPsec connectivity to a Gateway, you can encounter issues during negotiation of IPsec ciphers.
Example errors in IPsec logs: NO_PROPOSAL_CHOSEN
Solutions
Solution 1: Use recommended ciphers
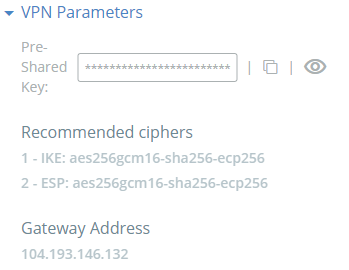
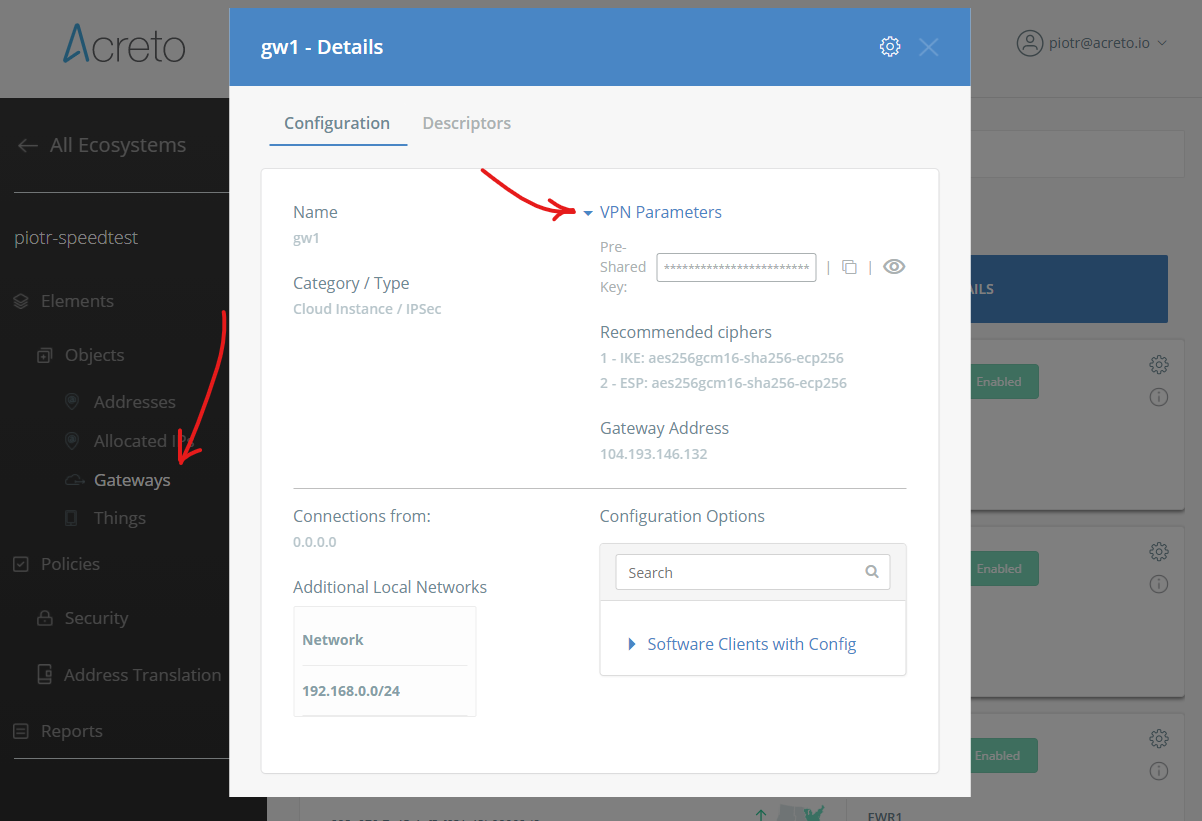
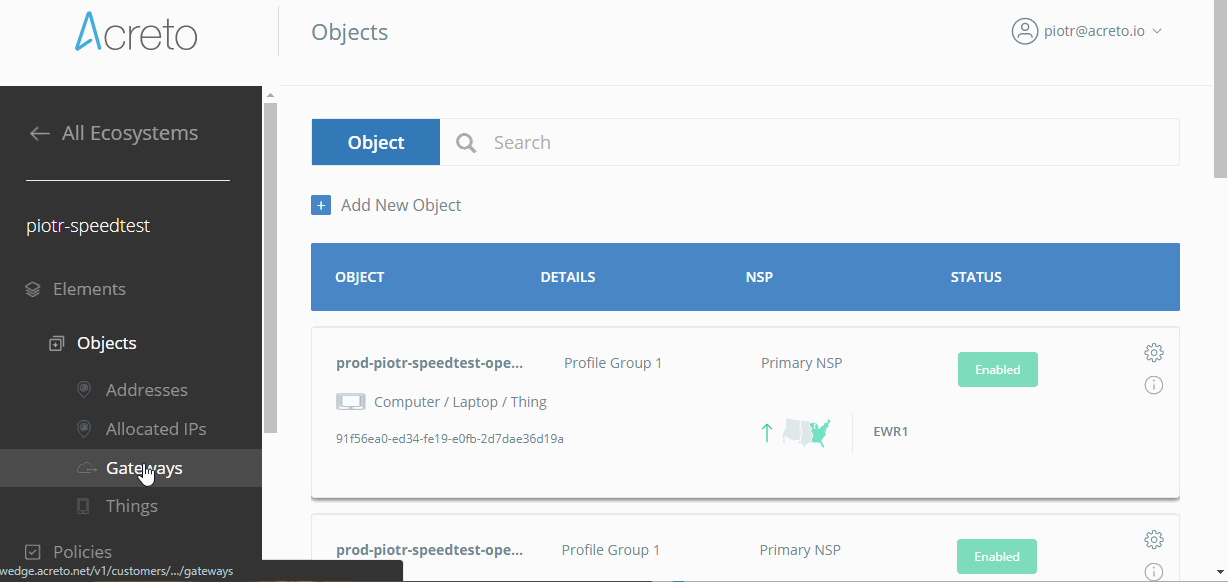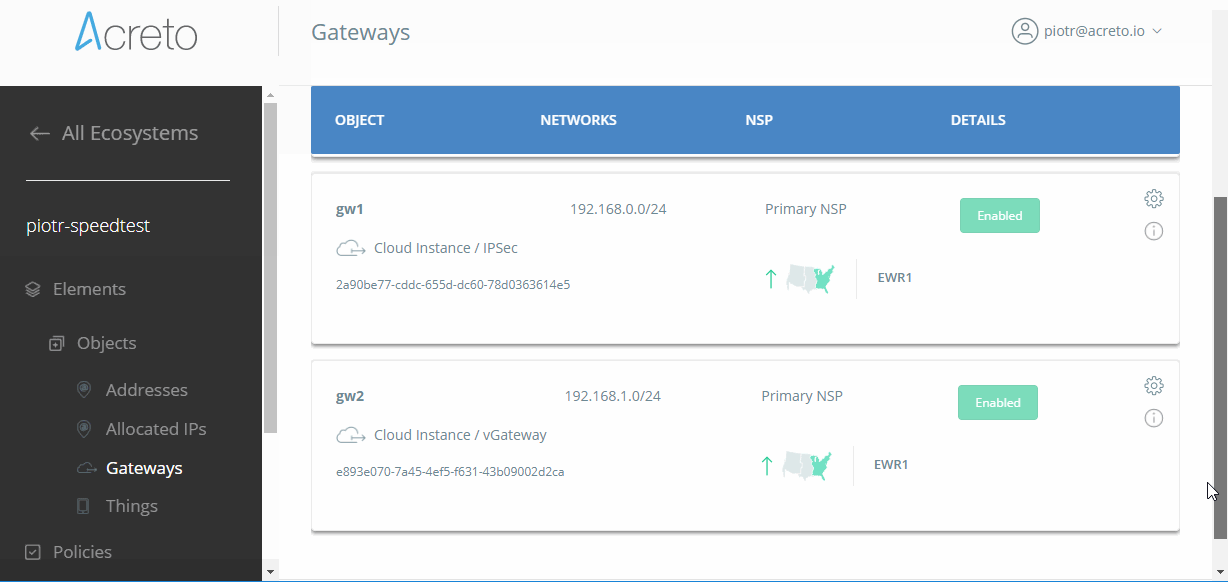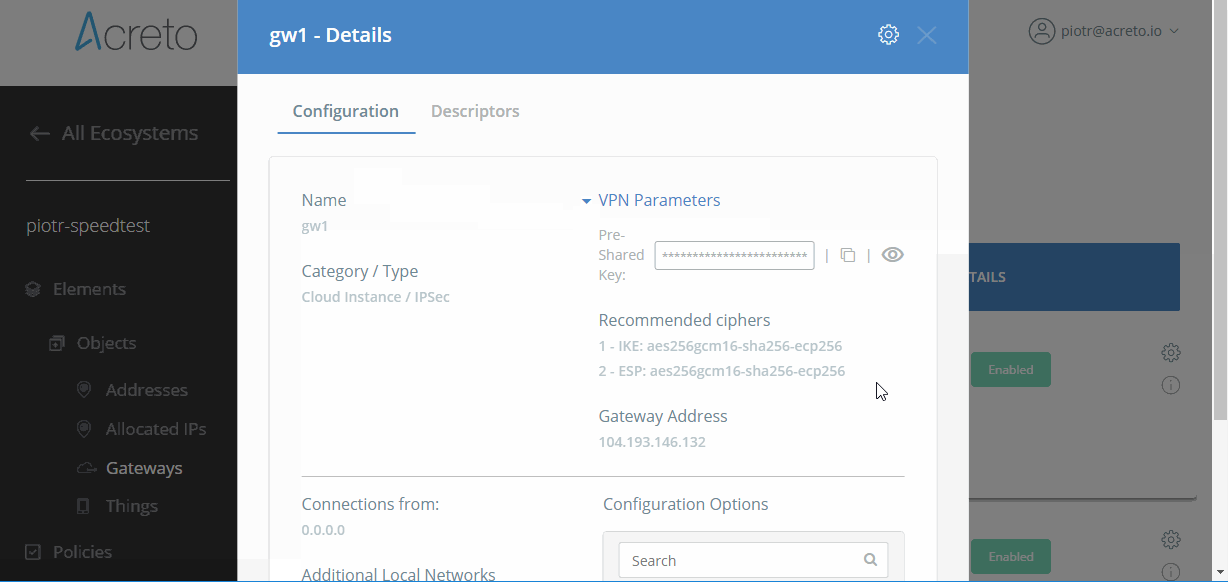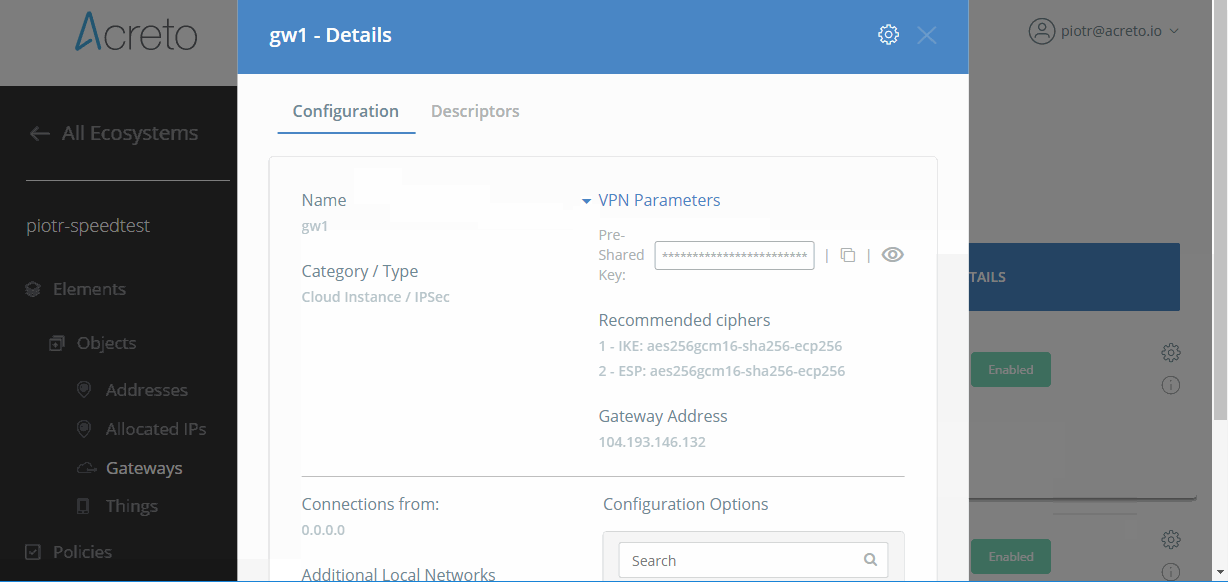
To see recommended ciphers, display details of your Gateway on the Acreto Platform and check Recommended Ciphers in the VPN Parameters section.
An example of recommended ciphers:
- IKE: aes256gcm16-sha256-ecp256
- ESP: aes256gcm16-sha256-ecp256
Solution 2: Use all supported ciphers
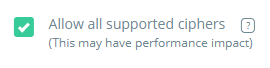
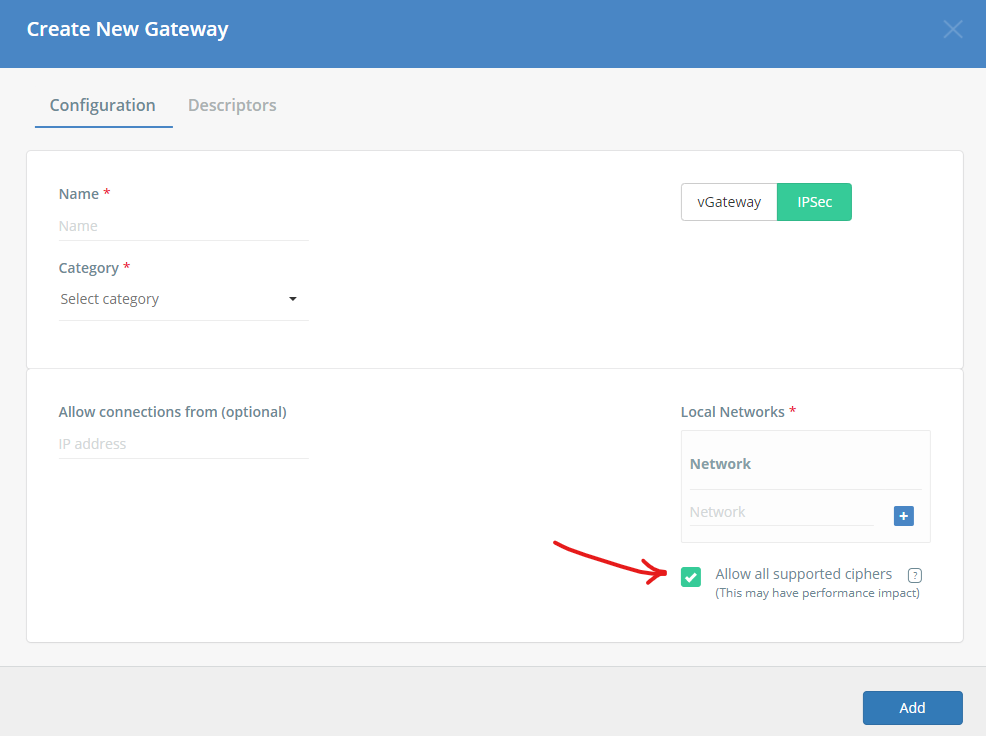
This solution allows the Acreto IPSec tunnel to support all supported ciphers.
-
Ensure that checkbox “Allow all supported ciphers” in Gateway definition on Acreto platform is checked
-
Ensure your Ecosystem has been committed
-
On your end, select one of the supported ciphers
All combinations of allowed algorithms can be found here:
Below you can find a list of all ciphers supported by Acreto.
Encryption
- aes256gcm16
- aes256
- aes256ctr
- aes256ccm16
- aes128gcm16
- aes128[!]
We consider aes128 as insecure, but we still have it supported for legacy systems, as per user request.
DH groups
- ecp384
- ecp256
- ecp512
- modp4096
- modp6144
- modp8192
- modp2048
- modp3072
Integrity
- sha384
- sha256
- sha512
FAQ - Frequently Asked Questions
Which SHA-2 ciphers are supported by Acreto IPsec?
We support the following ciphers from the SHA-2 family:
- SHA-256
- SHA-384
- SHA-512
See also
A list of default ciphers is created based on guidelines from:
- Commercial National Security Algorithm Suite (CNSA Suite)
- Recommendation for Key Management, Special Publication 800-57 Part 1 Rev. 5, NIST, 05/2020.
- Cryptographic Mechanisms: Recommendations and Key Lengths, TR-02102-1 v2020-01, BSI, 03/2020.
- strongSwan Security Recommendations
- www.keylength.com