Ubiquiti Unifi IPsec Configuration
Overview
In this article, you will learn how to connect to the Acreto ecosystem with your Unifi USG/Edgerouter using IPSec VPN.
Prerequisites
- Ubiquiti USG/EdgeRouter installation
- Ecosystem set up with proper security policies
How-To
Step1: Create Gateway for IPsec
Firstly, you will need to create a new Gateway device in the Acreto platform. Instructions on how to create a new Gateway are available here. If you already have one, make sure that it’s IPsec type and jump to How-to.
- Name: IPsec connection name must meet the same requirements as the Strongswan connection name (letters and numbers only).
- Category: IoT
- Type: IPsec
- Allow connection from: Empty (describes the source IP address where the IPsec connection will be permitted).
- Local Networks: any local network addresses that will be routed through this gateway.
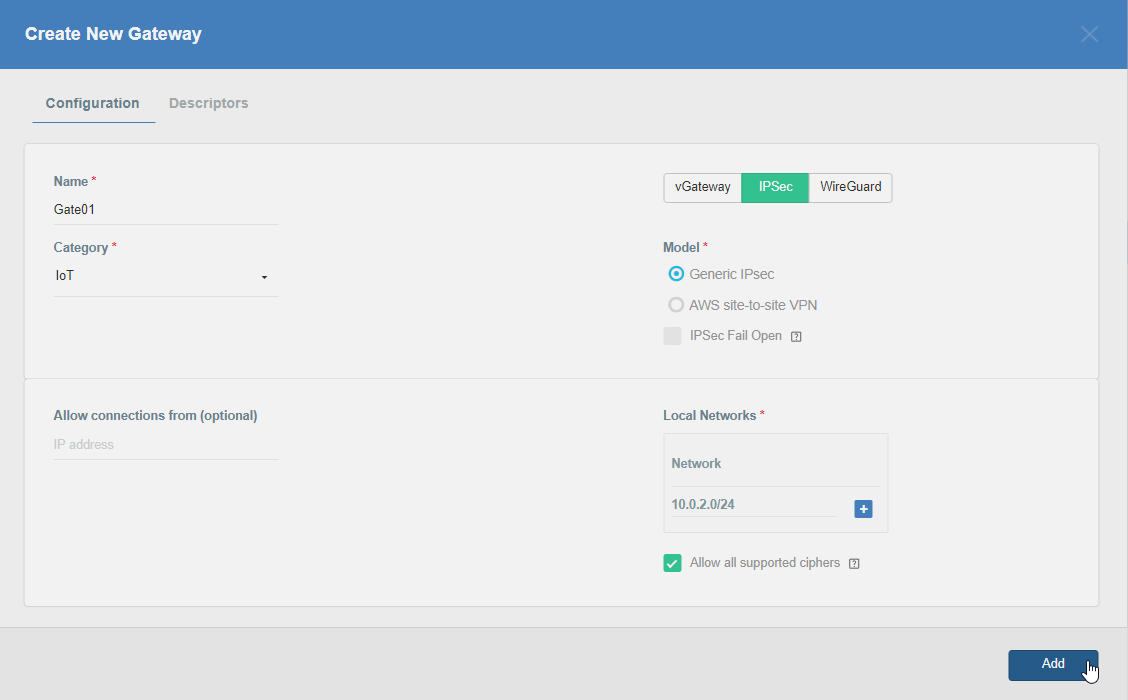

To simplify testing, add the IP addresses of all interfaces connected to your gateway as Local Networks (you can use /32 prefix for public interface). This will allow you to test connectivity from the gateway through Acreto by using Ping, Traceroute, or similar tools.
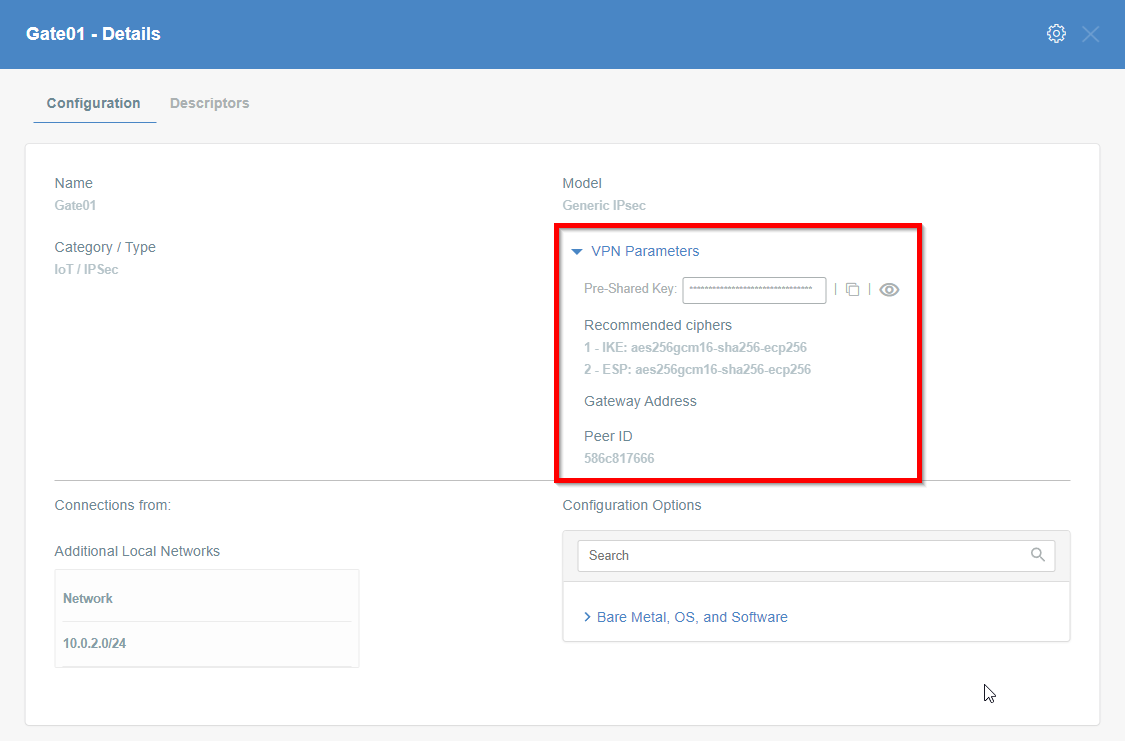
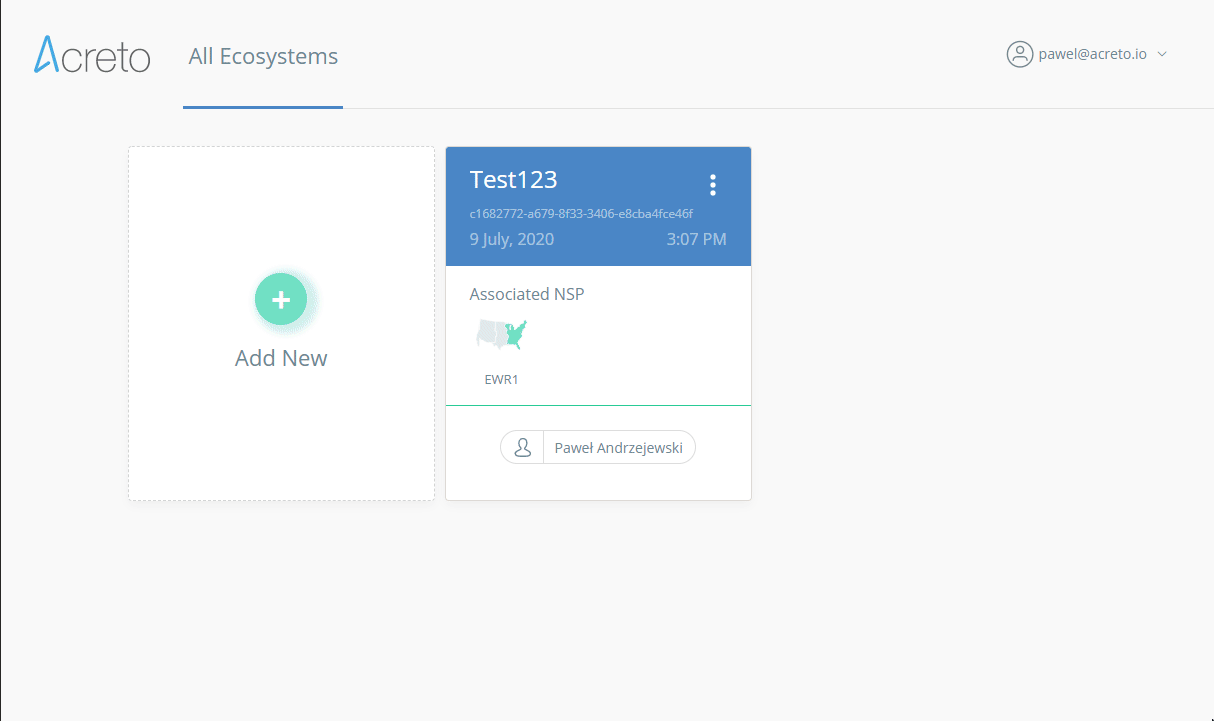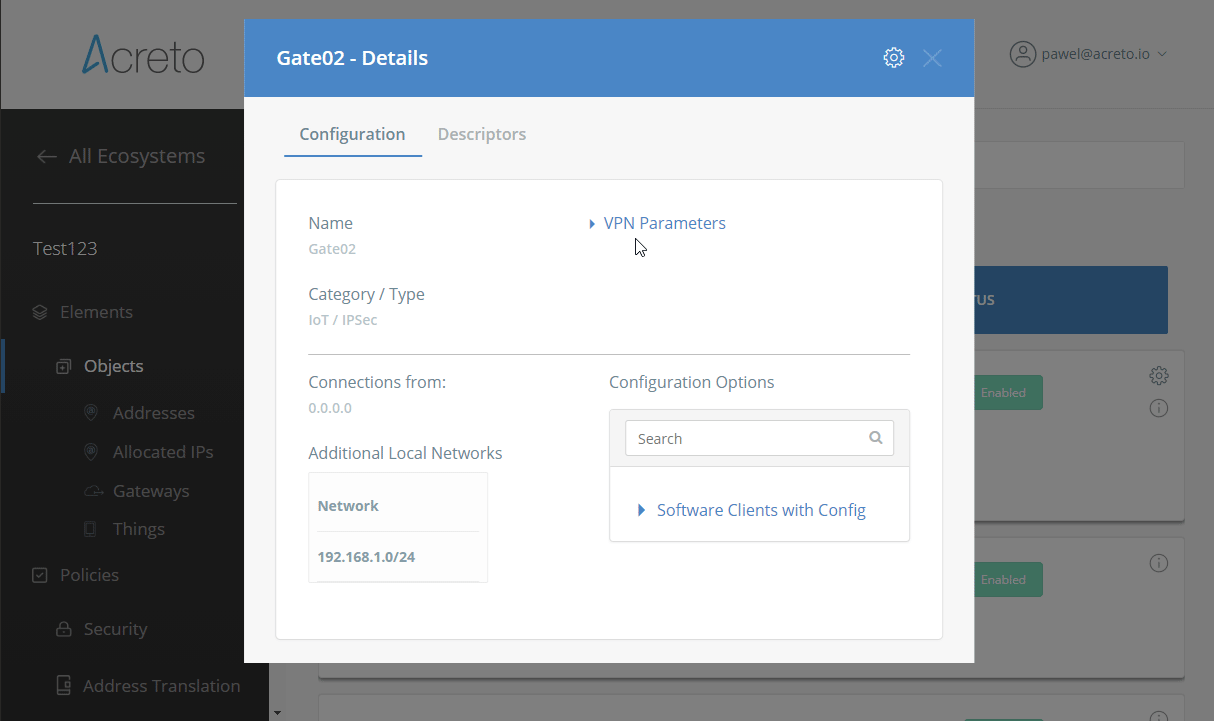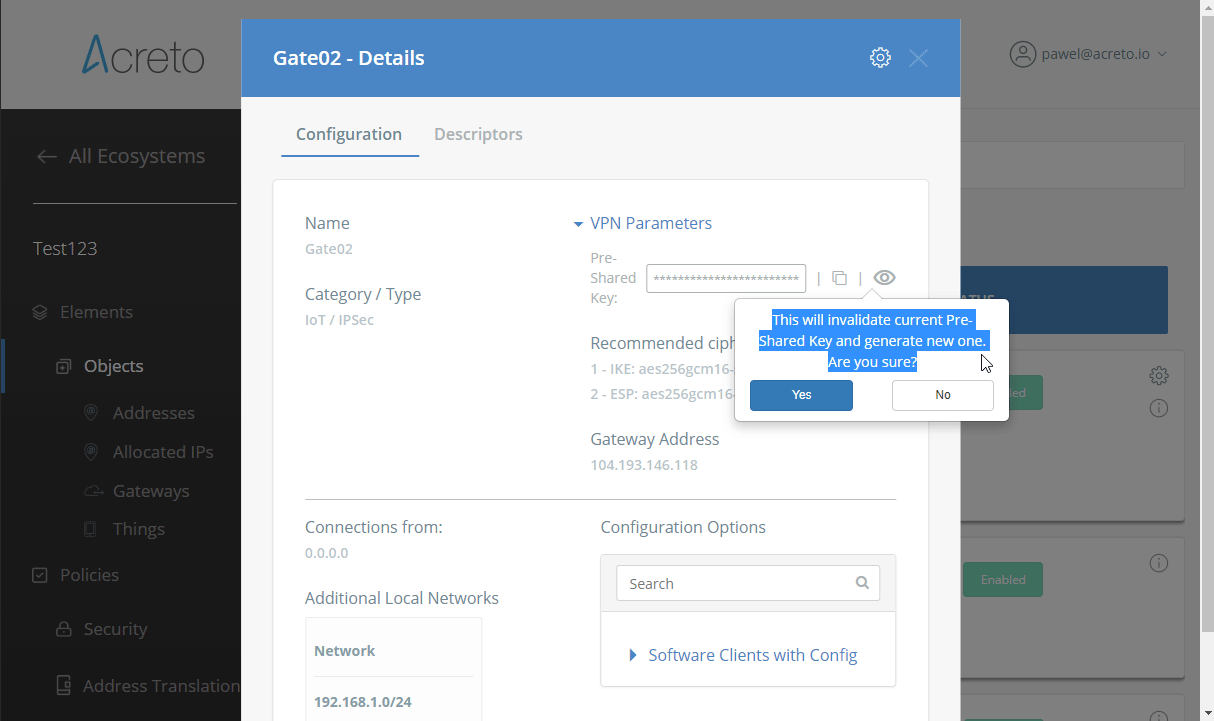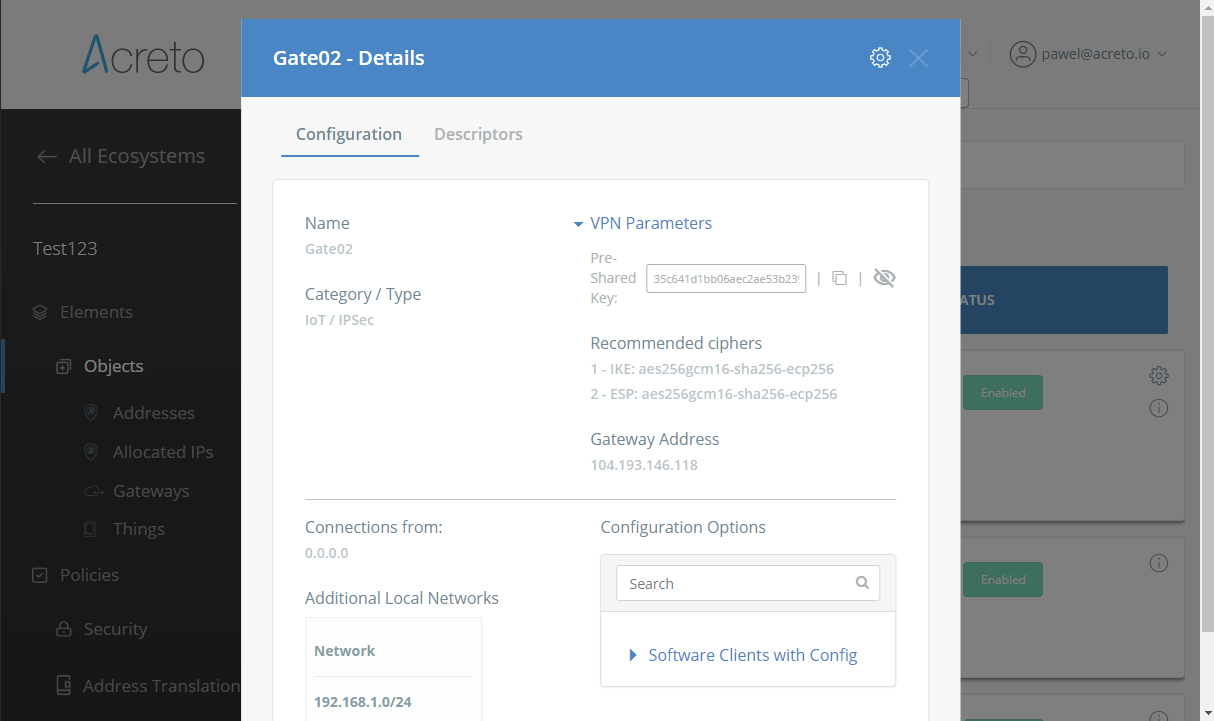
Step 2: Read the IPsec Gateway Values Required for Ubiquiti Configuration from Acreto Ecosystem
To proceed with the Ubiquiti configuration, you will need a few values from an existing committed Acreto Gateway:
All of these may be found within the Gateway details panel - view the below animation for further instruction.
Step 3: Configure VPN settings on Ubiquiti
-
Login into Ubiquiti and enter Configuration mode
configure -
Enable the auto-firewall-nat-exclude feature which automatically creates the IPsec firewall/NAT policies in the iptables firewall.
set vpn ipsec auto-firewall-nat-exclude enable. -
Create the IKE / Phase 1 (P1) Security Associations (SAs) by providing the following values
set vpn ipsec ike-group AcretoGate key-exchange ikev2 set vpn ipsec ike-group AcretoGate lifetime 10800 set vpn ipsec ike-group AcretoGate proposal 1 dh-group 16 set vpn ipsec ike-group AcretoGate proposal 1 encryption aes256 set vpn ipsec ike-group AcretoGate proposal 1 hash sha256 -
Create the ESP / Phase 2 (P2) SAs.
set vpn ipsec esp-group AcretoGate lifetime 3600 set vpn ipsec esp-group AcretoGate proposal 1 encryption aes256 set vpn ipsec esp-group AcretoGate proposal 1 hash sha256 set vpn ipsec esp-group AcretoGate compression disable -
Execute the below command using values from previous steps: Configure the below steps with values for Gateway address, Preshared key and Peer Id collected in Step 1.
- GATEWAY_ADDRESS - available in step 1, number 1 on screen.
- PRE-SHARED KEY - available in step 1, number 2 on screen.
- PEER ID - available in step 1, number 4 on screen.
set vpn ipsec site-to-site peer GATEWAY_IP_ADDRESS authentication mode pre-shared-secret set vpn ipsec site-to-site peer GATEWAY_IP_ADDRESS authentication pre-shared-secret PRE-SHARED_KEY set vpn ipsec site-to-site peer GATEWAY_IP_ADDRESS description ipsec set vpn ipsec site-to-site peer GATEWAY_IP_ADDRESS authentication id PEER_ID -
Copy the WAN IP and router address from the Ubiquiti gateway device
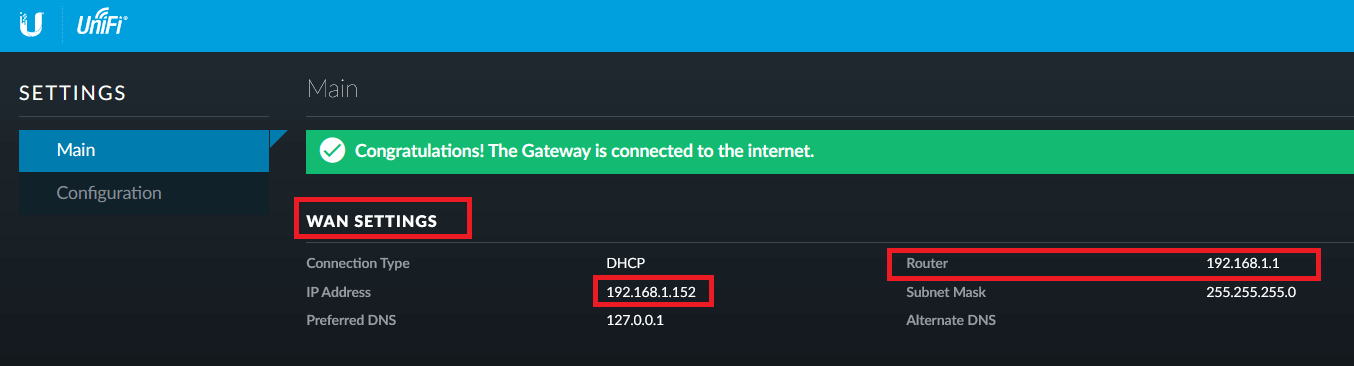

-
Use the above WAN IP and conFigure the Peer with the below commands
set vpn ipsec site-to-site peer GATEWAY_IP_ADDRESS local-address LOCAL_WAN_INTERFACE -
Link the SAs created in the above steps to the remote peer and bind the VPN to a virtual tunnel interface (vti0).
set vpn ipsec site-to-site peer GATEWAY_IP_ADDRESS ike-group AcretoGate set vpn ipsec site-to-site peer GATEWAY_IP_ADDRESS vti bind vti0 set vpn ipsec site-to-site peer GATEWAY_IP_ADDRESS vti esp-group AcretoGate -
Configure a static route to route gateway address to the internet directly. Use router address copied from step 6.
set protocols static route GATEWAY_IP_ADDRESS next-hop ROUTER_IP_ADDRESS -
Configure default static route to send all traffic to Acreto VPN.
set protocols static interface-route 0.0.0.0/0 next-hop-interface vti0 -
Commit the changes and save the configuration.
commit ; save
Summary
Once the VPN connection is successfully established, all the internet traffic will be routed through Acreto.