Linux - Automatic IPsec Configuration
Prerequisites
- Ubuntu 18.04 or newer installed on your device
- Ecosystem set up with proper security policies
Create Gateway for IPsec
If you didn’t do it yet, you need to create a new Gateway device on the Acreto platform.
-
Login to the Acreto platform at wedge.acreto.net
-
Select your ecosystem and go to Objects using the left menu.
-
Click Add new Object and select Gateway.
-
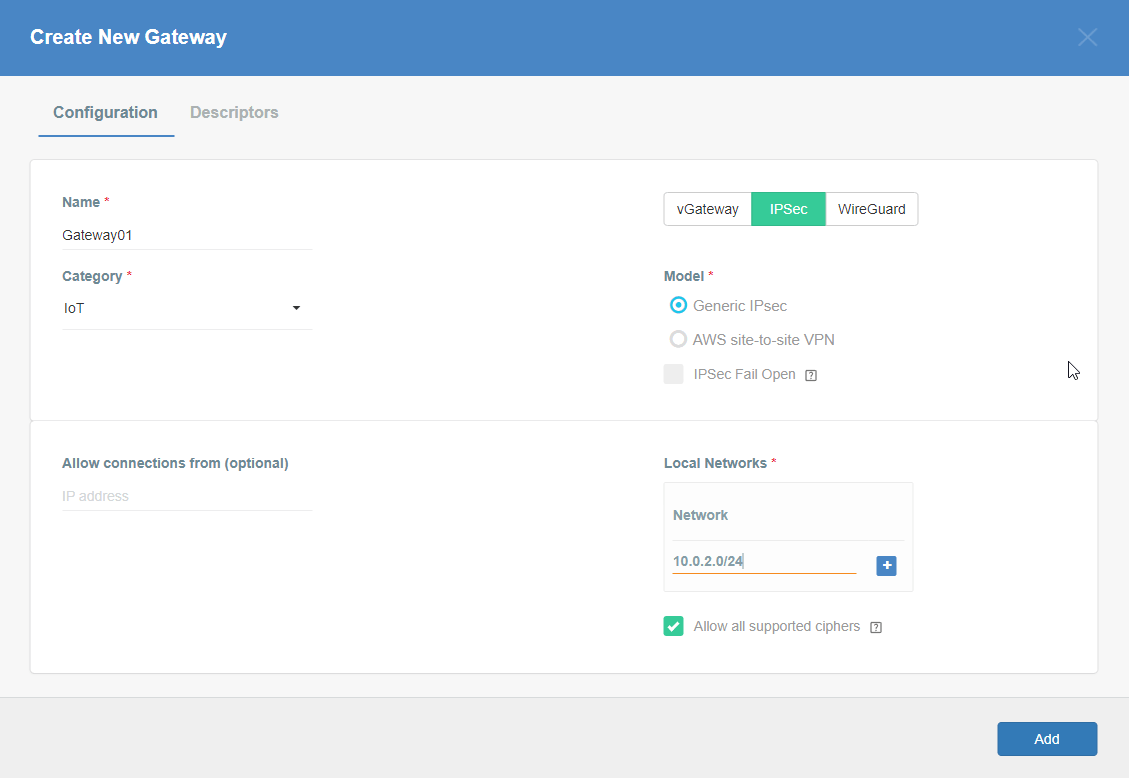
Fill at least:
-
Name: the name of the IPSec connection needs to be compatible with Strongswan connection name requirements (basically, only letters and numbers)
-
Category: IoT
-
Allow connection from: Empty (describes the source IP address where the IPsec connection will be permitted)
-
Local Networks: - your local network addresses that should be routed through this gateway
Note: To simplify testing, add IP addresses of all interfaces connected to your gateway as Local Networks (you can use /32 prefix for public interface). This will allow testing connectivity from the gateway through Acreto using ping, traceroute, and similar tools.
-
-
Save the created Gateway by pressing Add.
-
Add a security policy that will allow communication from the Gateway device to the Internet.
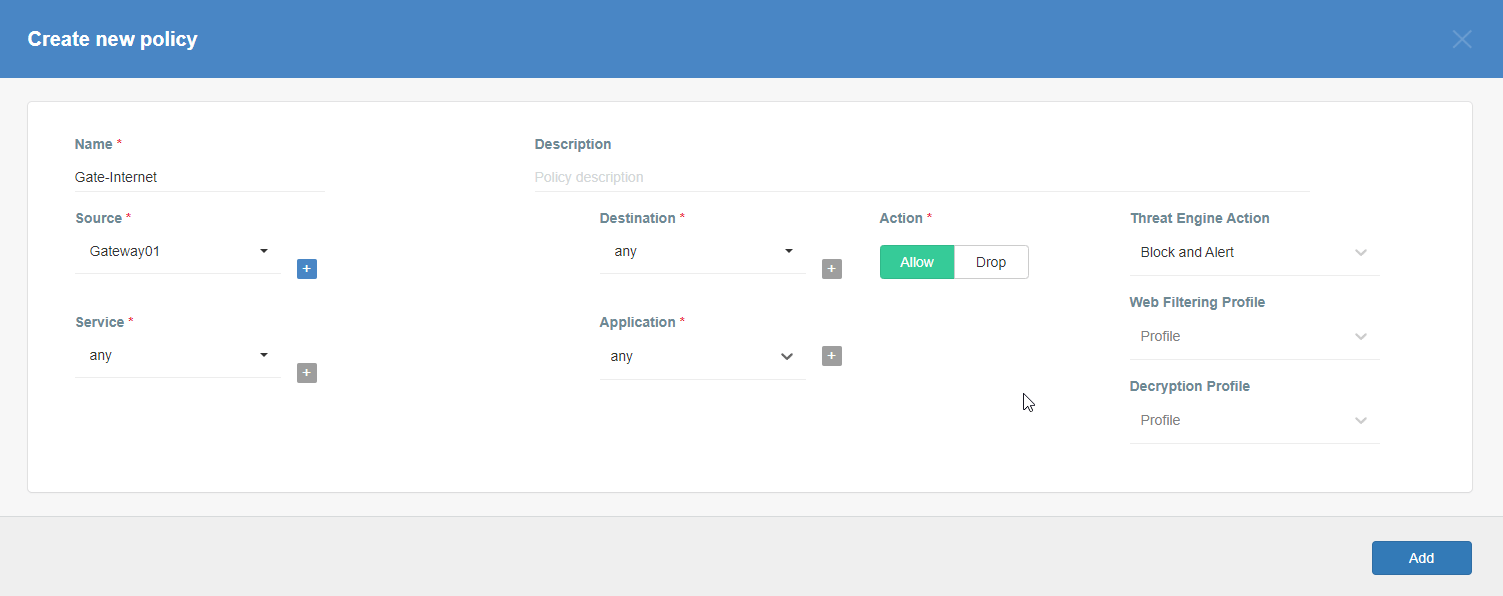

-
Commit pending changes (top of the screen)
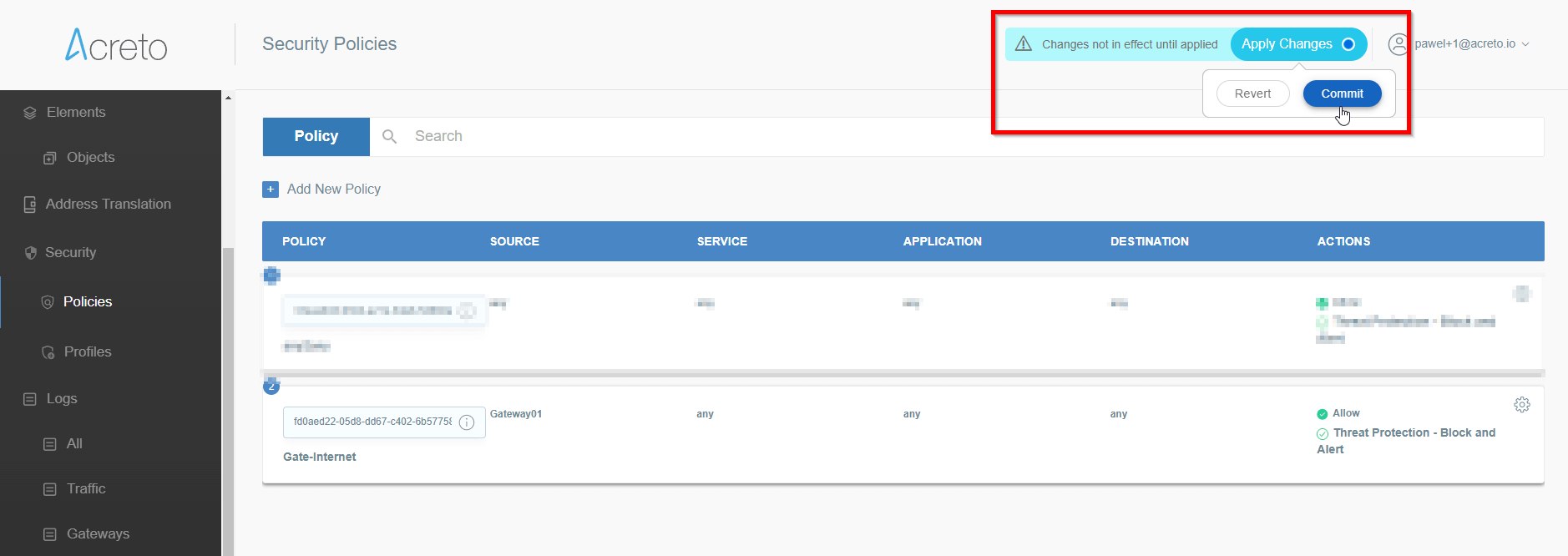
 Note: to successfully test your connectivity, you also need to create a
security policy that will allow traffic going through your device.
Note: to successfully test your connectivity, you also need to create a
security policy that will allow traffic going through your device.
Generate Strongswan config files
-
Log in to the Acreto platform at wedge.acreto.net
-
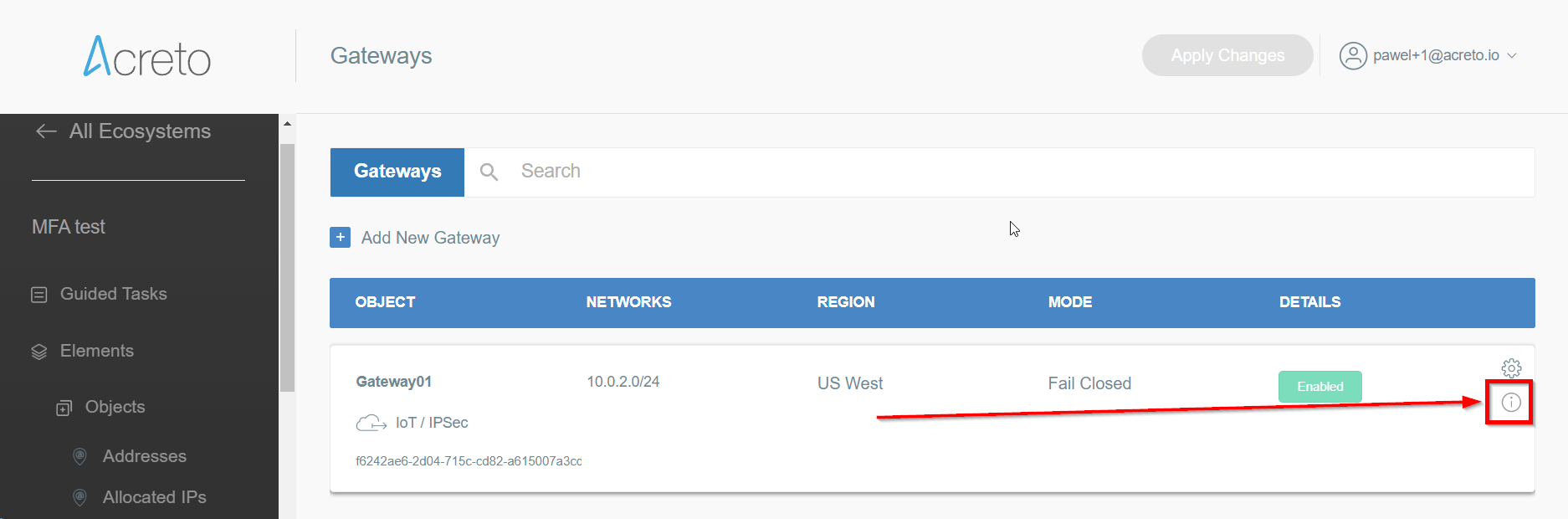
Select your ecosystem and go to Objects using the left menu
-
Open the gateway object which you want to use by clicking on its “Info” button.
-
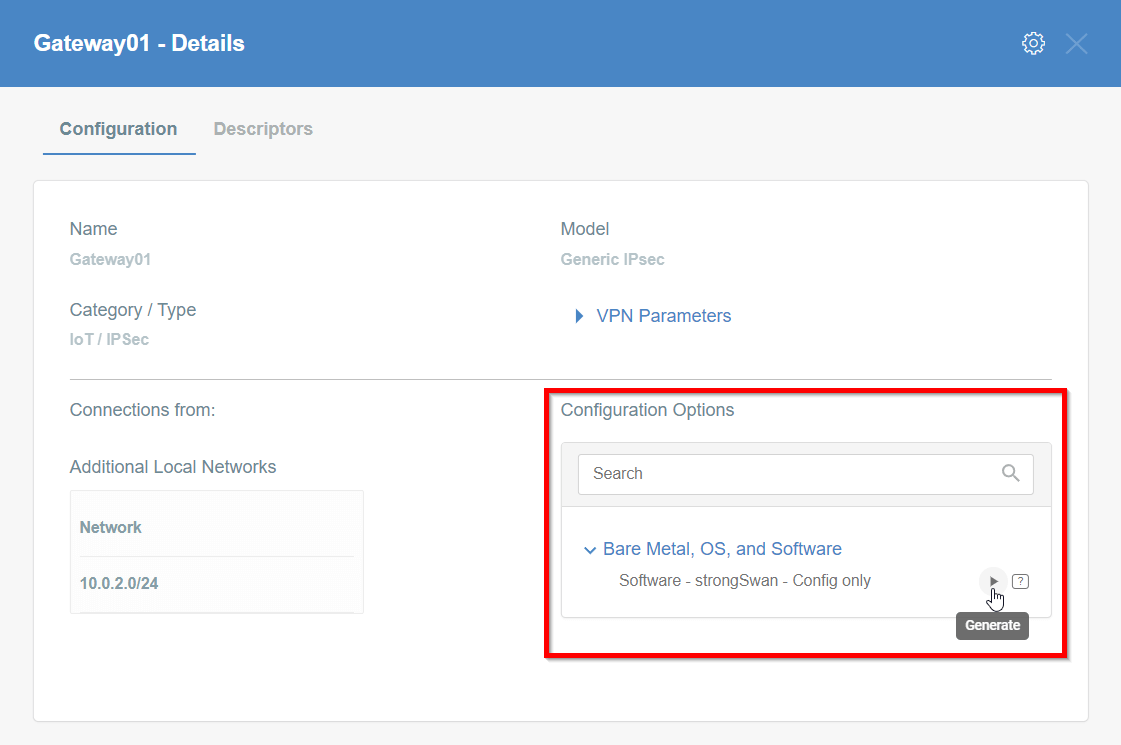
Generate the IPsec strongSwan config using Configuration Options > Bare Metal, OS and Software
Then Click on [Play Button]
-
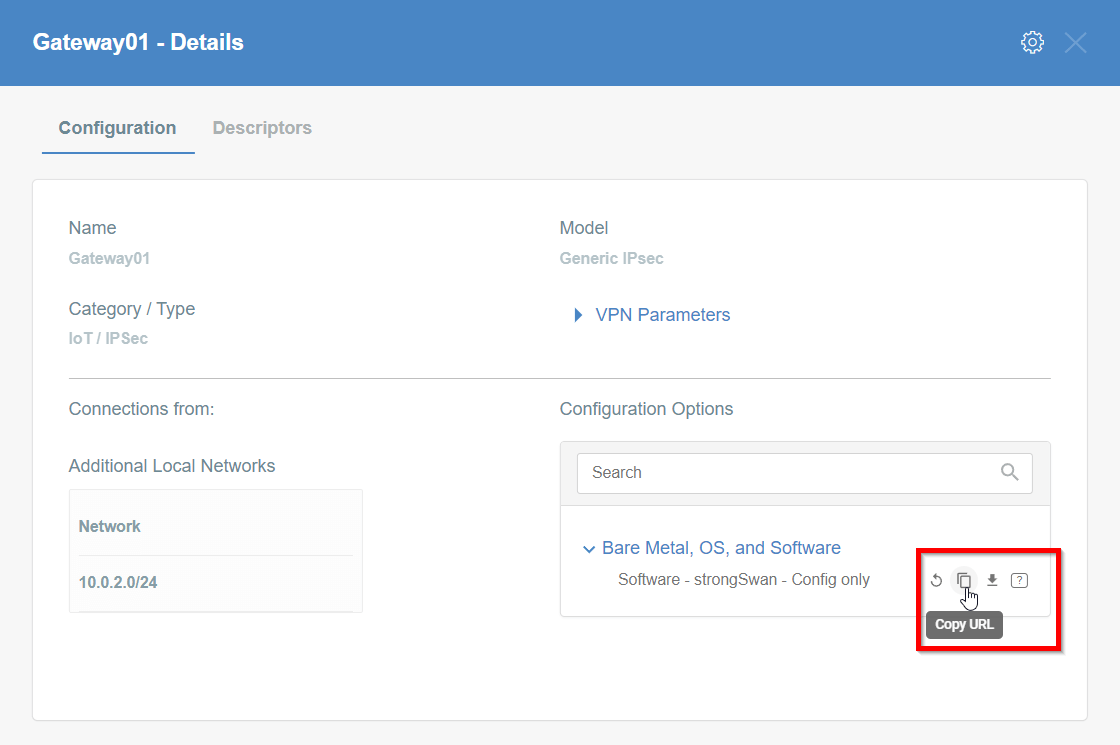
Copy the link to the IPsec strongSwan config file
Installation using acreto-ipsec.sh script
-
Execute the following commands on your Linux shell
curl -fsSL https://kb.acreto.net/reference-material/downloads/acreto-ipsec.sh | sudo bash -s -- [URL_to_strongswan_config]where
[URL_to_strongswan_config]is the URL copied in previous step.Example:
curl -fsSL https://kb.acreto.net/reference-material/downloads/acreto-ipsec.sh | sudo bash -s -- https://api-is-rock-solid.acreto.net/v2/gateways/ipsec/config/strongswan?_token=s.WNJJeTxWsIeXMkgeIA96SOe8
IPsec tunnel and routing verification
-
Ensure that traffic goes through Acreto (with traceroute or mtr)
Execute the command:
mtr 8.8.8.8The ouput should indicate that packets go through
100.65.0.x:Host Loss% Snt Last Avg Best Wrst StDev 1. 100.65.0.30 0.0% 9 225.1 225.1 224.6 225.8 0.3 2. 100.65.0.1 0.0% 8 225.9 227.5 225.7 237.1 3.9 3. ??? 4. nyk-b2-link.telia.net 0.0% 8 226.0 226.9 226.0 228.3 0.7 5. 72.14.218.254 0.0% 8 227.1 227.8 226.4 230.4 1.2 6. 108.170.248.97 0.0% 8 227.1 227.2 226.8 227.9 0.4 7. 108.170.227.211 0.0% 8 226.5 226.9 226.0 227.7 0.6 8. dns.google 0.0% 8 226.7 227.6 226.7 229.2 0.8
IPsec Operational Commands
-
Restart IPsec service with the following command:
ipsec restart -
Wait approximately 10 seconds, and check the status of IPsec:
ipsec statusall -
If the connection did not start, try to take it up manually:
CONN=`grep '^conn .*' /etc/ipsec.d/*.conf|cut -d' ' -f2`; echo $CONN ipsec up $CONNIt should display information useful for debugging purposes.
-
Ensure everything works fine with:
ipsec statusall ip address show ip route show -
Check if you have Internet access
IPsec Watchdog
In case you Internet connection if very unstable or your ISP changes your public IP, then you may consider running an IPsec watchdog that verifies every minute if the tunnel is passing the traffic to Acreto Ecosystem.
Please download the script and follow the steps from the comments section at the beginning of this script.
Click on the button and save the script in your home directory:
Get ipsec-watchdog.shor open the terminal and download the script directly to your vGateway using the command:
cd /etc/ipsec.d/
wget https://kb.acreto.net/reference-material/downloads/ipsec-watchdog.sh